Transparency Policy
Given that GNSS spoofing detection systems are designed to protect critical infrastructure, we firmly believe in upholding a policy of complete transparency. Therefore, we are publishing this detailed report on the testing of our system at JammerTest 2023.
Our commitment to excellence is demonstrated by our transparency in acknowledging areas for improvement within our system. This openness reflects our confidence in the system’s market-leading status and our proactive approach to enhancements. We see each shortcoming as an opportunity for growth and are dedicated to implementing solutions promptly. Our track record of rapid innovation ensures that any issues are addressed swiftly, solidifying our system as the most reliable choice in the industry.
Our transparency policy encompasses the following principles:
- Detail-Oriented Transparency: We provide comprehensive data on methodologies, processes, and test results, enabling all stakeholders to gain a deeper understanding of our system and the testing process.
- Accessibility of Results: We make our results publicly accessible to facilitate knowledge exchange within the industry and support collaborative efforts in developing effective protection systems.
- Trust in Transparency: Our belief in the superiority of our system motivates us to embrace open criticism and self-analysis, ensuring continuous improvement and reliability of our solutions.
We believe that only through complete transparency can we ensure the highest level of protection for critical infrastructure and contribute to the development of secure technological solutions in this field.
Intro
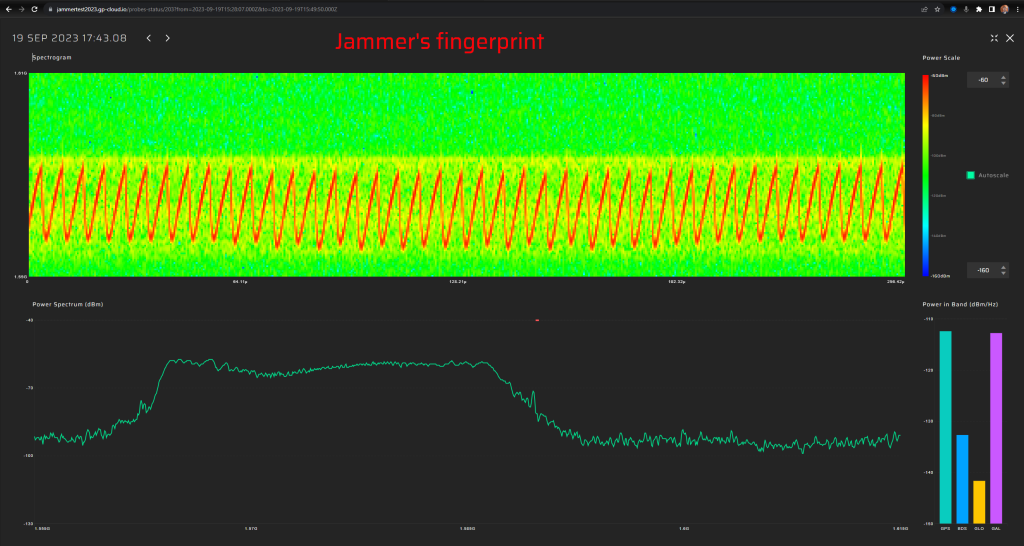
In September 2023, GPSPATRON participated in Jammertest 2023, a campaign organised by Norwegian authorities to assess the impact of jamming and spoofing on satellite navigation systems. The campaign was held on the island of Andøya, Norway, a remote area where the organisers can interfere with the Global Navigation Satellite System (GNSS) signal in a controlled environment. The campaign involved various tests and scenarios, such as high-power jamming, and sophisticated spoofing attacks.
We had two objectives:
- Testing our new GNSS interference classification algorithms for GP-Probe TGE2.
In jammertest2022 we found that some types of GNSS jamming modulation lead to false positive spoofing triggering.
https://gpspatron.com/jammertest2022-norway/
We have now significantly improved our classification algorithms. - Testing our new single channel detector – GP-Probe DIN L1.
https://gpspatron.com/gp-probe-din-l1/ - Testing the new implementation of the GP-Probe TGE2 for heavy weather conditions with an integrated GNSS antenna system.
This article is a detailed report on the testing of our equipment during the event. In this report, we focus on the following parameters for anomaly detection and spoofing classification:
- Detection/classification latency
- Recovery time after spoofing
The numbering of sections and subsections in this report is aligned with the official Testplan for the event “Jammertest 2023” (Transmission Plan).
Event Overview and Interview with Organizers
Insights & Highlights
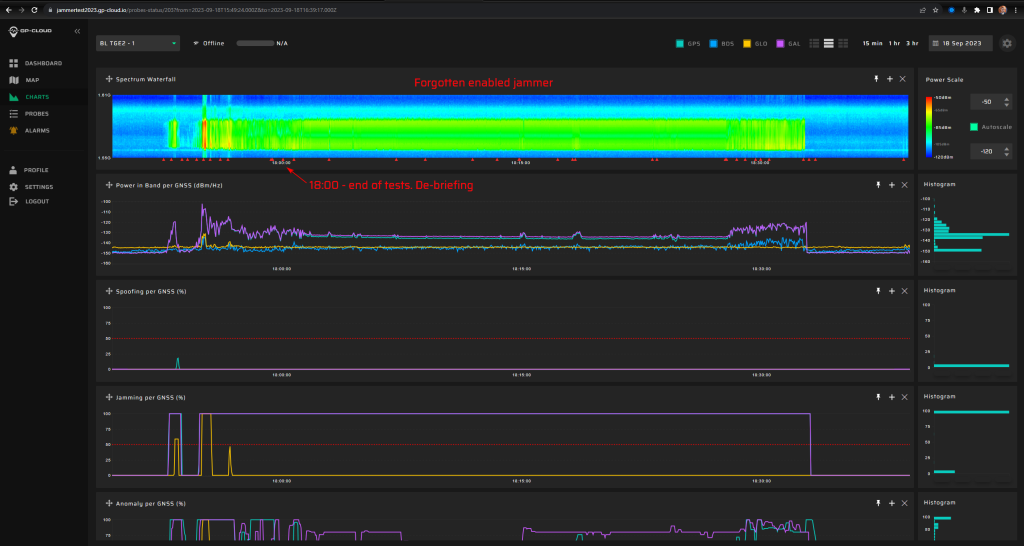
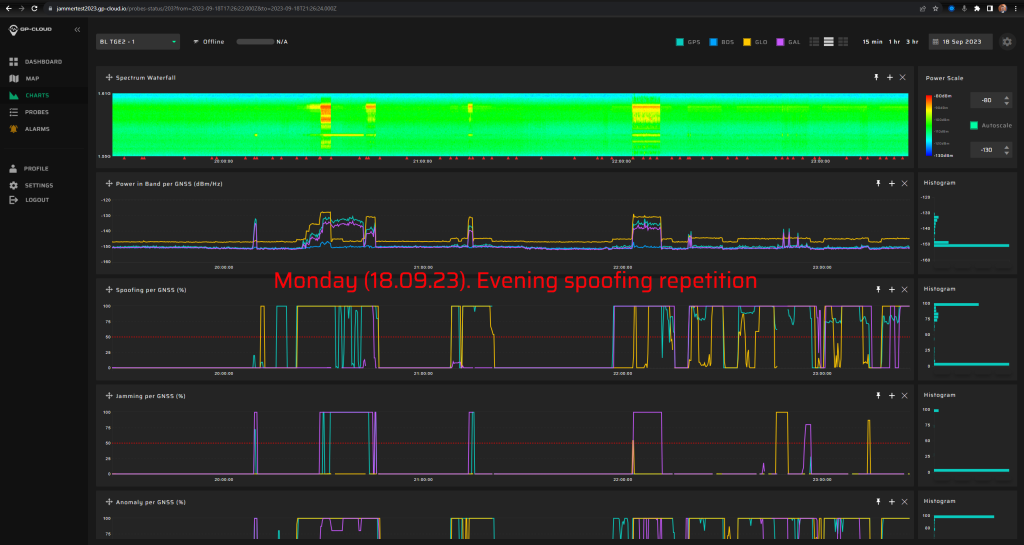
Managing extensive exercises like JammerTest2023 requires a large team and often, the best-laid plans take unexpected turns.
Thursday's Surprises
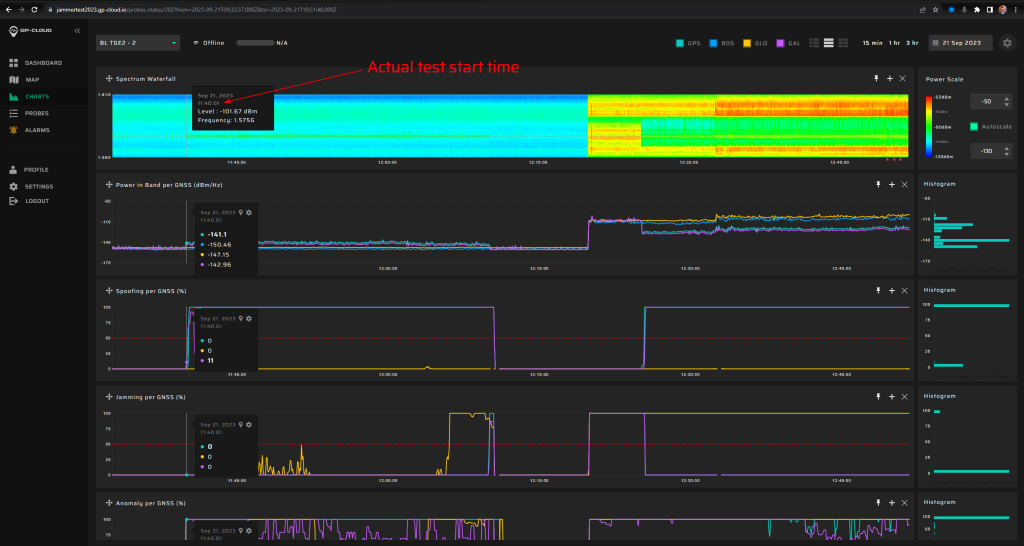
Thursday’s agenda took a detour from the expected route. In the morning session, we encountered a hiccup and couldn’t locate test items 18.1.1 and 18.1.4. Adding to the day’s surprises, test 19.1.1 launched a brisk 20 minutes earlier than anticipated.
In the second half of Thursday, we successfully identified only the first two scenarios. The subsequent scenarios did not proceed as planned:
Equipment Under Test
- GP-Probe TGE2
- GP-Probe DIN L1
- GP-Probe TGE2 in protected design with integrated antenna system
Spoofing detection algorithms are tuned to minimize false positives under all types of interference. This of course reduces the sensitivity of the algorithms. But it completely eliminates false positives.
Testing Program
This time JammerTest2023 was entirely focused on spoofing. Jamming was only during the first day and half of the second. More detailed information can be found in the following documents.
11 Stationary meaconing with varying power and time exposure
The objective is to observe how equipment and systems behave under meaconing. GNSS re-transmission of real live sky signals, where the GNSS environment will have a wrong position with real satellite data, only slightly time delayed.
The test will re-transmit only the GPS L1 and L2 bands. The re-transmitted signals need a lot of amplification, with the added risk of amplifying background noise. Therefore, it is hard to give precise estimates of effective power levels and range. Attendees should try to observe PNT changes and/or loss of PNT, and monitor the changes when their equipment and systems are exposed to two different power levels and varying degrees of time exposure to the meaconed signal. Maybe especially interesting is to see if the effects of movement and speed, coupled with other sensor data, will result on the total output. The tests are performed with constant power outputs (0.1 W or 1 W), and with varying lengths of transmission times.
11.1.1 Test: 0.1 W meaconing: 3 minutes
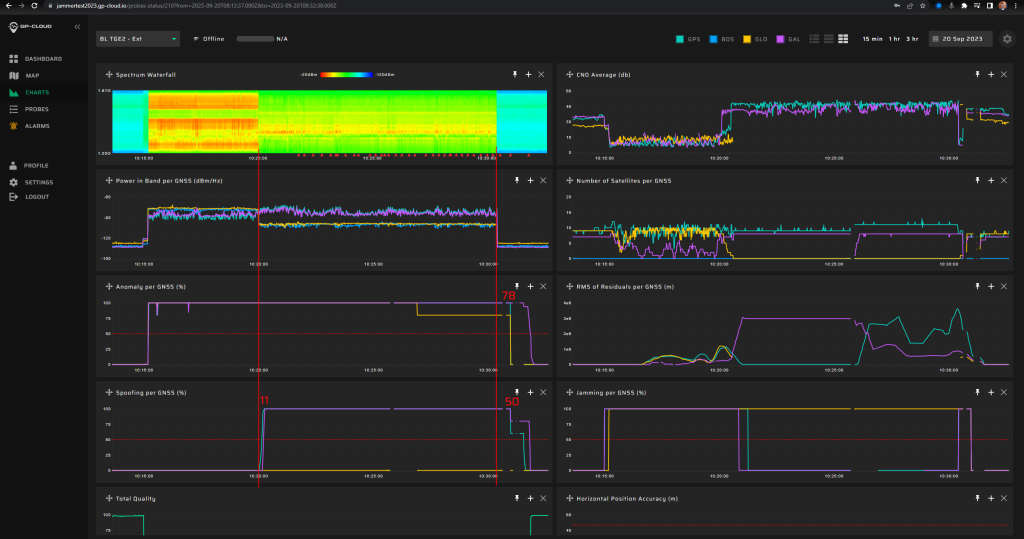
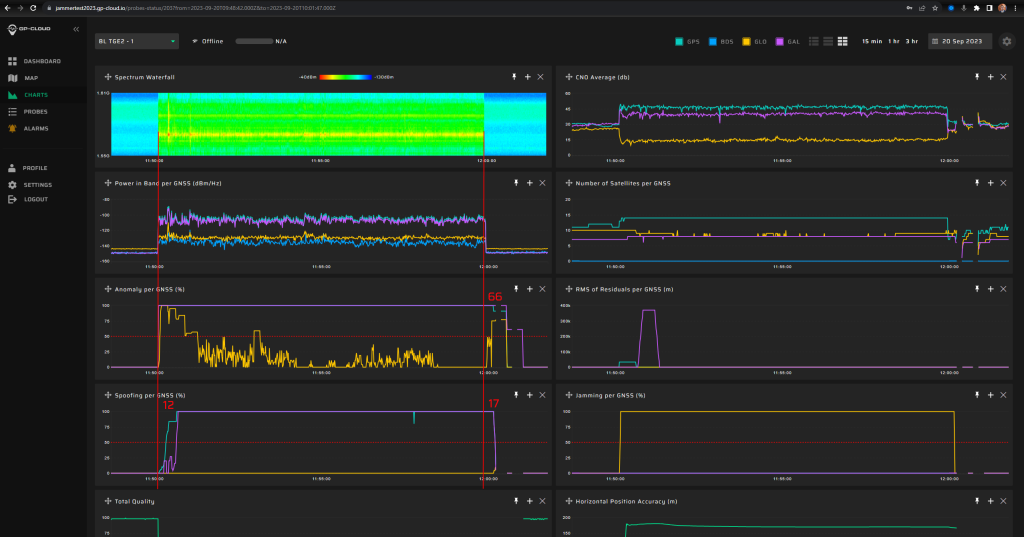
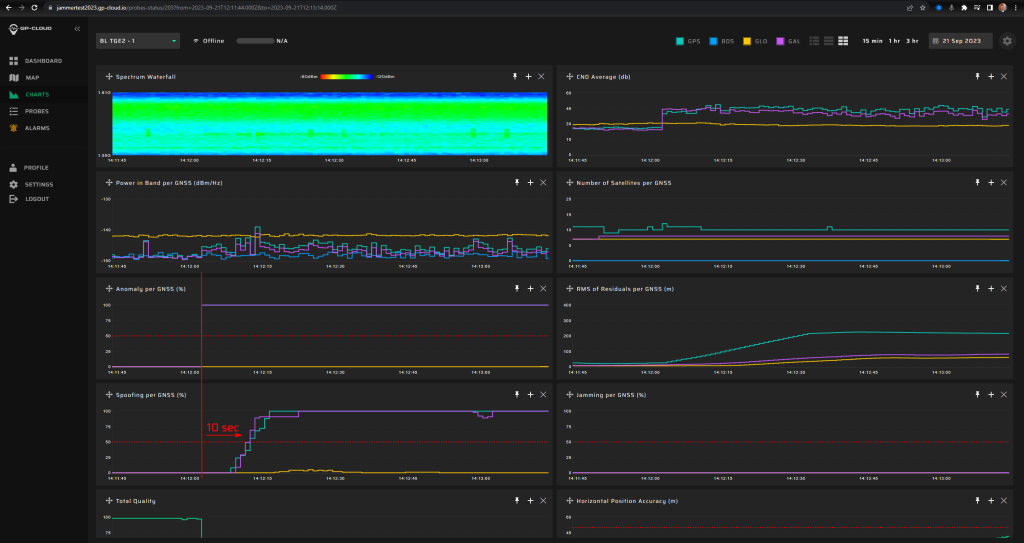
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
15 |
✓
20 |
34 | Despite the repeater being designed for GPS signals only, minor Galileo spoofing signatures were detected. This is normal since Galileo E1 and GPS L1 share the same center frequency.
The instability of the interference classification as spoofing is caused by the low power of the fake signal which had almost no effect on the reception of the original signals. |
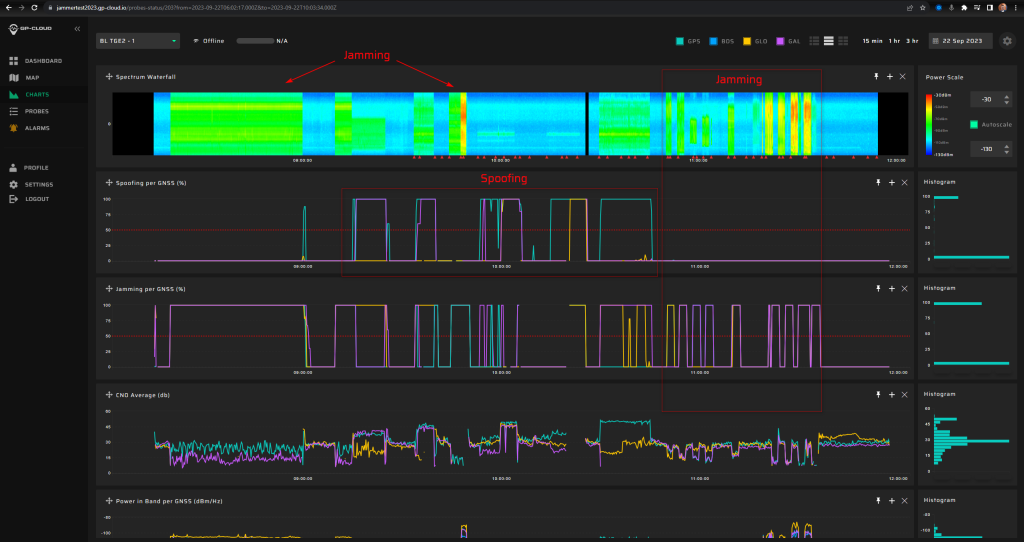
Screenshot from GP-Cloud:
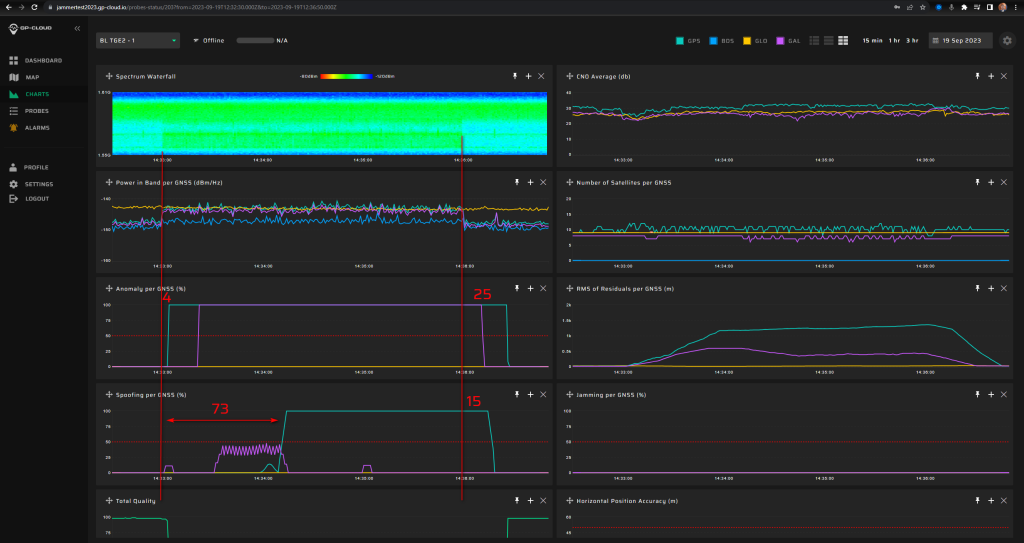
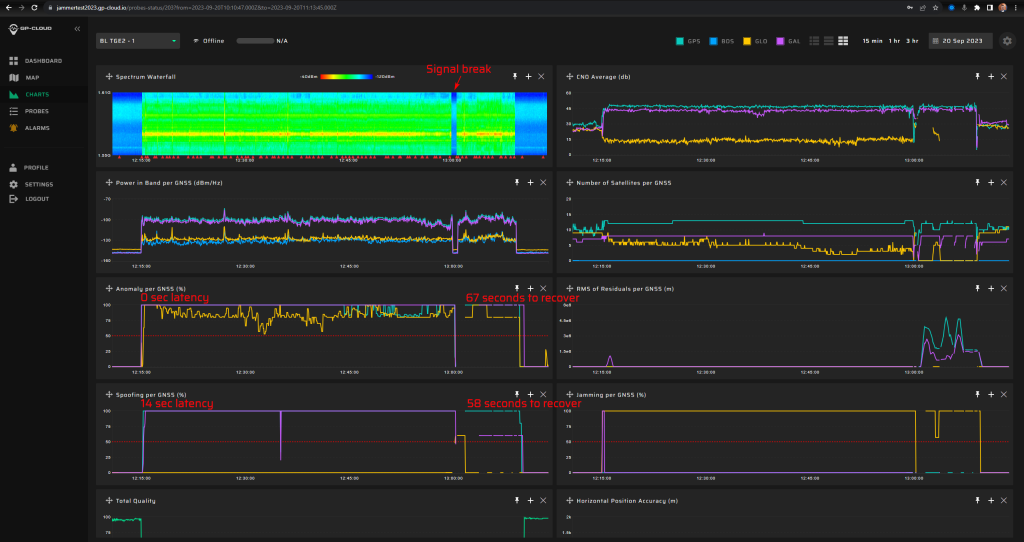
11.1.2 Test: 0.1 W meaconing: 3 minutes (repeat 11.1.1)
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
4 |
✓
73 |
25 |
|
Screenshot from GP-Cloud (In the screenshots, we indicate the detection latency and recovery time for spoofing and anomaly):
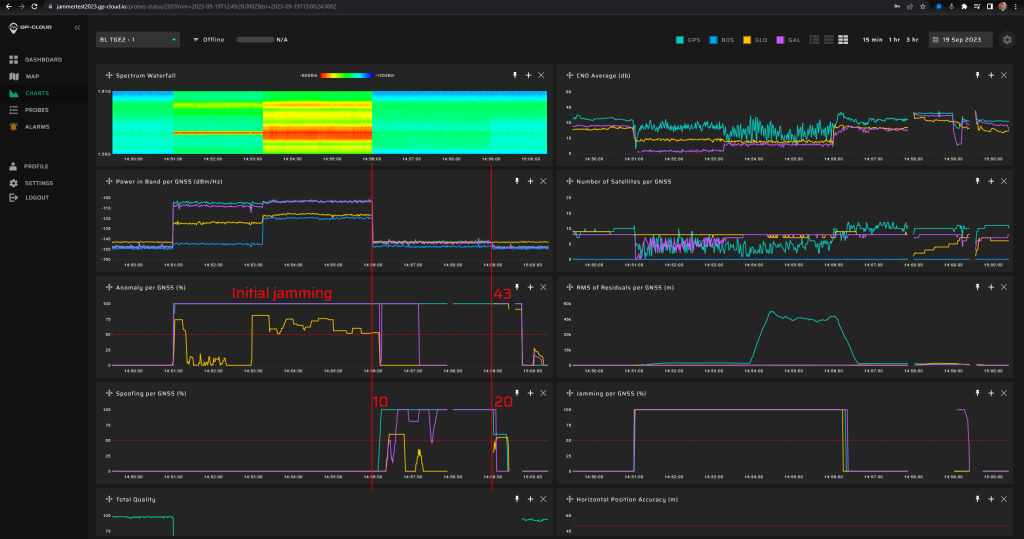
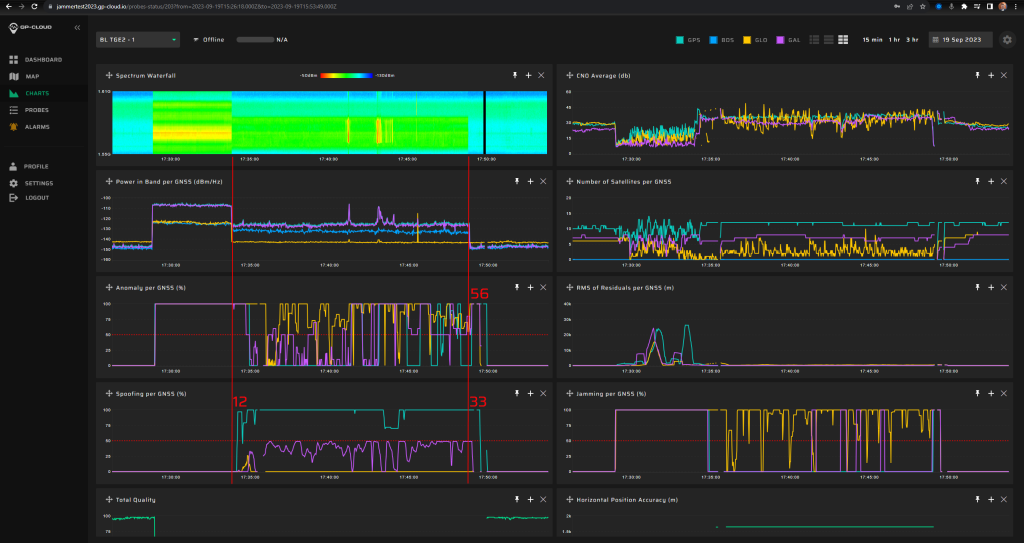
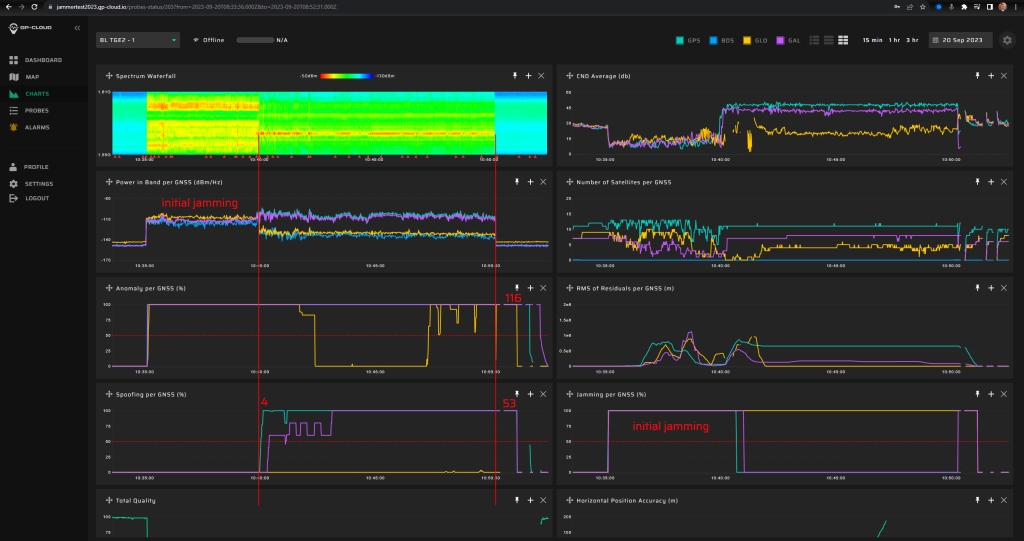
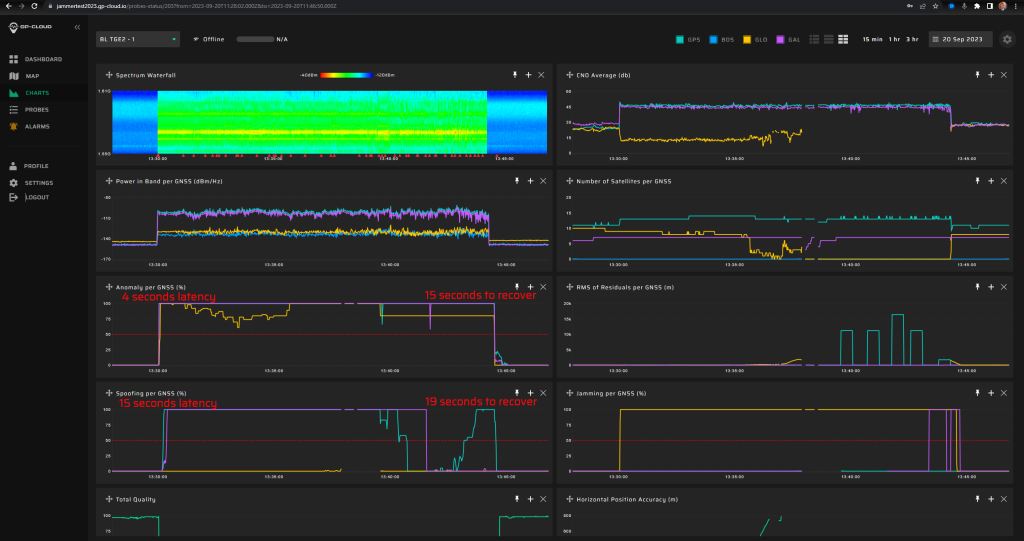
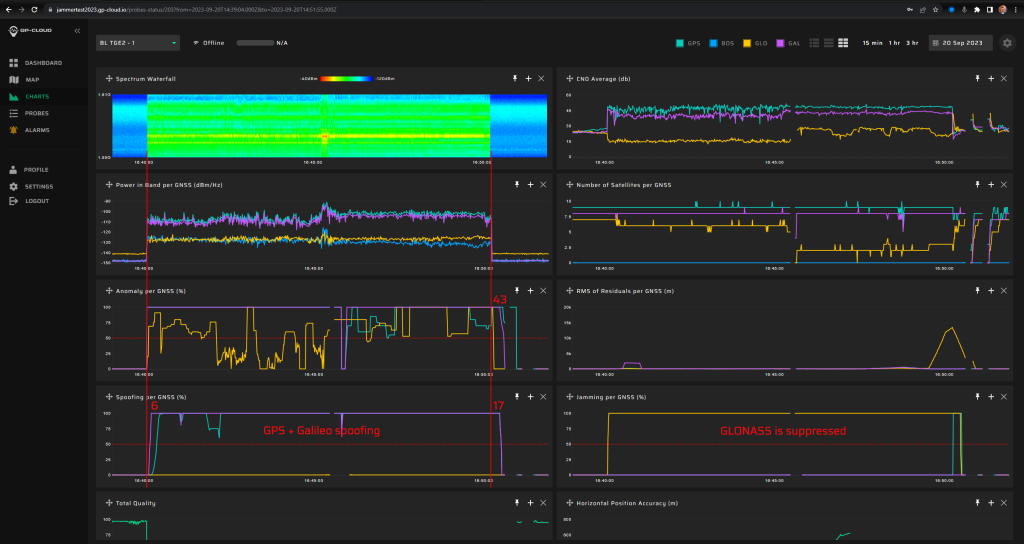
11.1.3 Test: 0.1 W meaconing: 3 minutes preceded by 5 min jamming
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
10 |
20/43 | There were minor false positives of GLONASS spoofing under GPS+Galileo spoofing. This issue will be fixed in the next release of GP-Cloud. Refer to the “Test Results” section of this report. |
Screenshot from GP-Cloud:
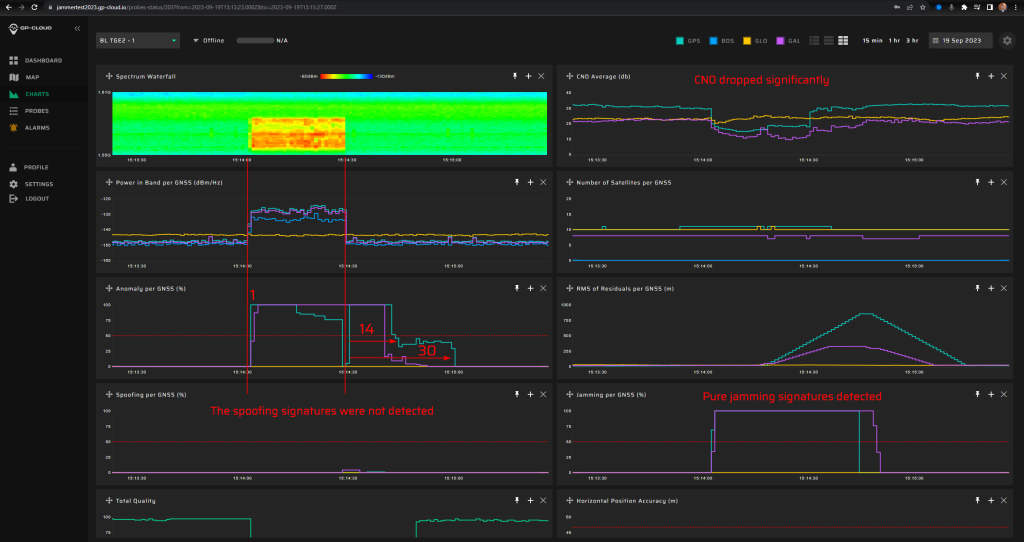
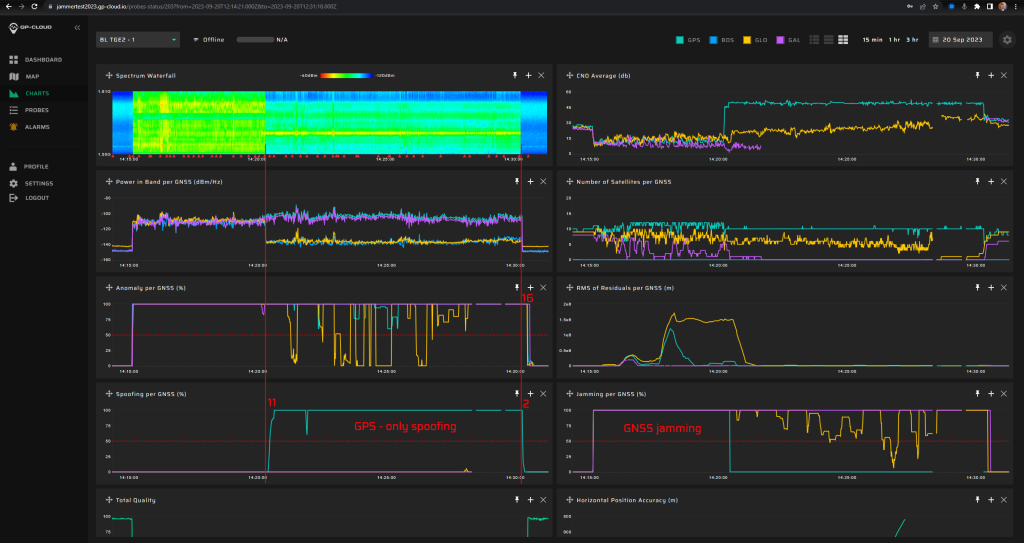
11.1.4 Test: 10 W meaconing: 30 seconds
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
1 |
✕
NA |
14/30 | GPS spoofing signatures were not detected. This may be due to the repeater gain settings not being adjusted correctly. The signal-to-noise ratio for GPS satellites on all tested probes just dropped sharply. This indicates that the amplified noise significantly exceeded the power of the original re-transmitted GPS signal. |
Screenshot from GP-Cloud:
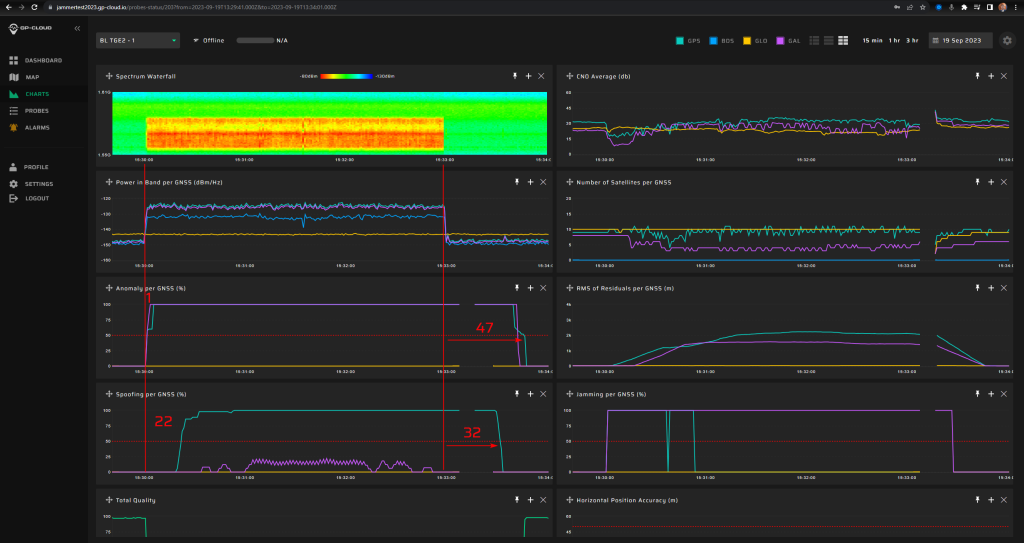
11.1.7 Test: 10 W meaconing: 3 minutes preceded by 5 min jamming
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
29 |
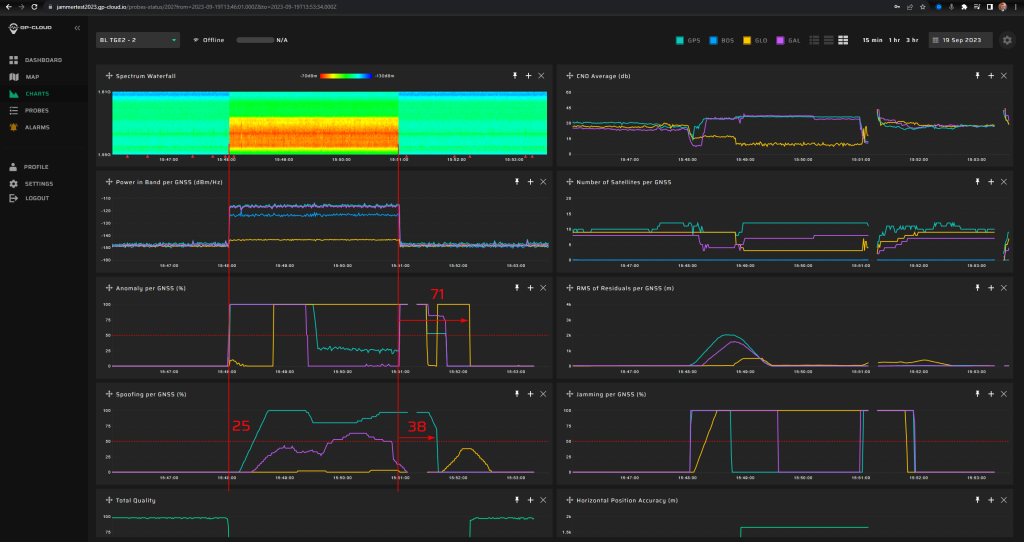
32/101 | Long recovery of true signal tracking after spoofing is caused by the non-optimal performance of recovery algorithms. This will be fixed in the next release of GP-Cloud. Refer to the “Test Results” section of this report. |
Screenshot from GP-Cloud:
11.1.8 Test: 10 W meaconing: 15 minutes
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
1 |
✓
21 |
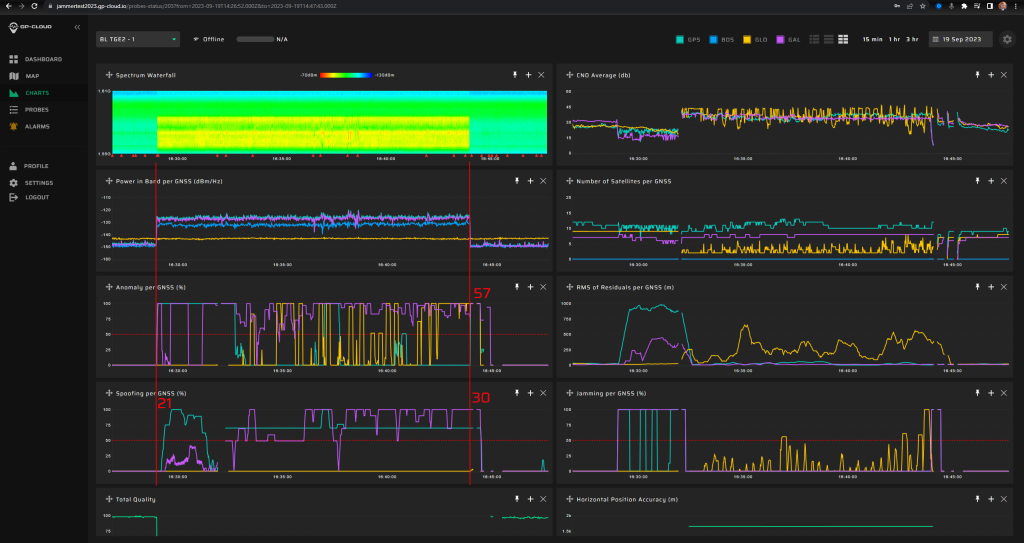
30/57 | The classification of the interference as GPS spoofing was not 100% due to a bug in the classification algorithm. This will be fixed in the next release of GP-Cloud. Refer to the “Test Results” section of this report. |
Screenshot from GP-Cloud:
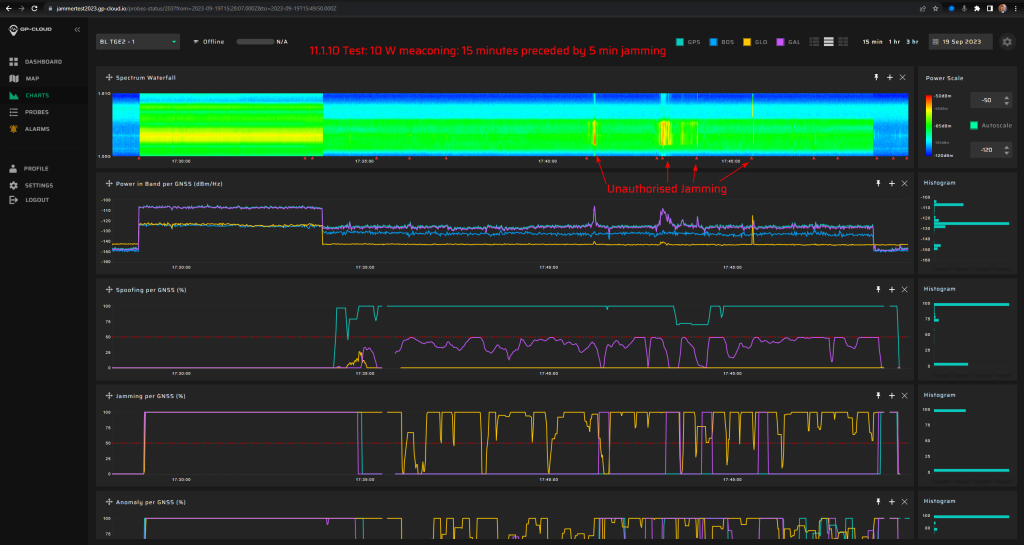
11.1.10 Test: 10 W meaconing: 15 minutes preceded by 5 min jamming
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
12 |
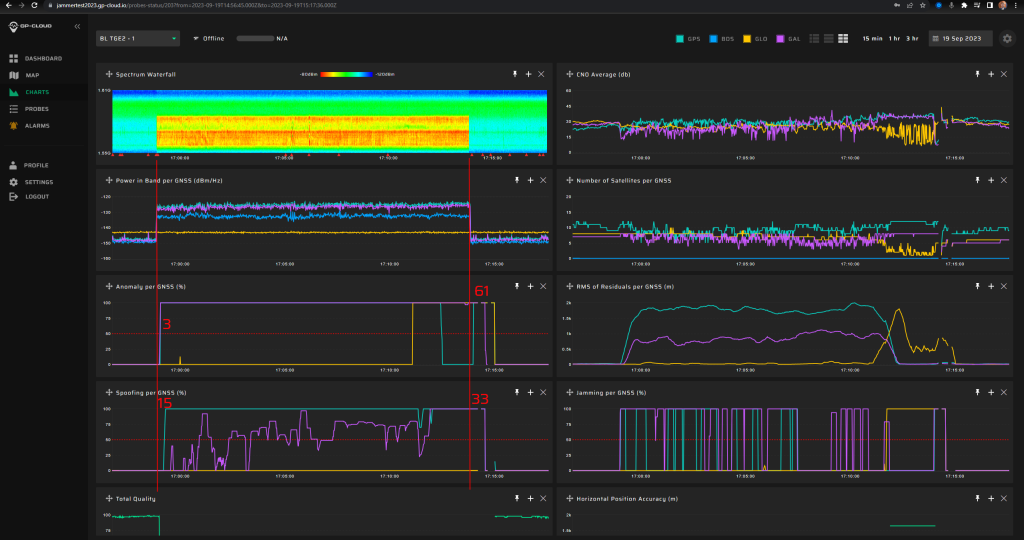
33/56 | Unstable detection of Galileo spoofing signatures, which is normal since the repeater is designed for GPS signals only. |
Screenshot from GP-Cloud:
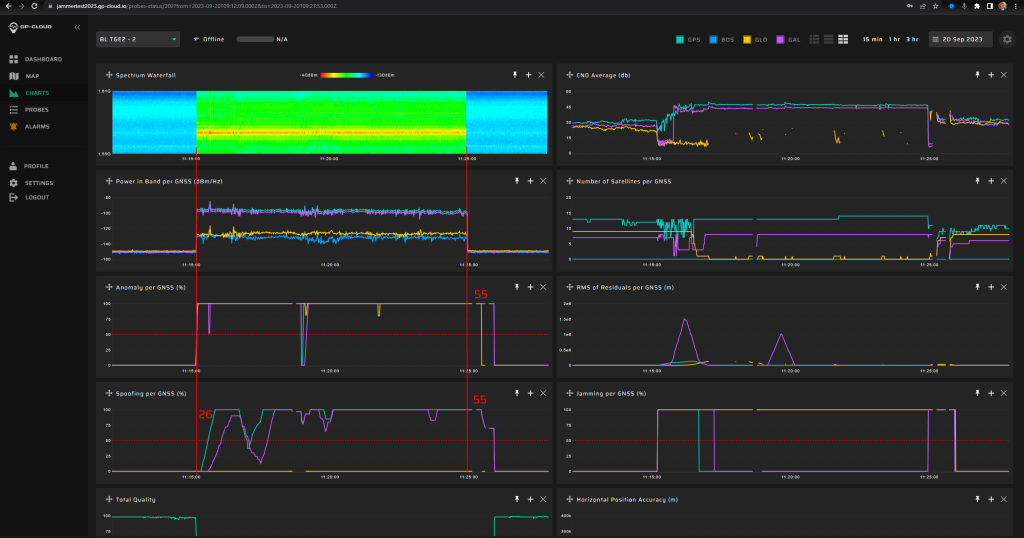
15 Incoherent spoofing from stationary spoofer using synthetic ephemerides
Generated spoofing scenarios will use satellite ephemerides different from live sky satellites. Simulated signals may use one or more constellations and one or more signal bands.
Initial positions are either False (e.g. 70 N, 10 E) or True (target location at Bleik community house). The initial time is either False (e.g. a jump in time) or True ( < 100 ns timing error for a receiver at the target location). Some test scenarios may be started with jamming (lasting for 5 min, one or several signal bands, before the spoofing transmission is activated). Some spoofing scenarios may be accompanied by continuous jamming (one or several signal bands).
Static scenarios are a fixed position, while motion scenarios are a drive around Andøya. Each test runs for between 10 and 20 minutes with 5 –10 minutes break between each test. For each dynamic test, the motion is first spoofed to a fixed start position (see 26.8) for 5 minutes before the dynamic motion
starts.
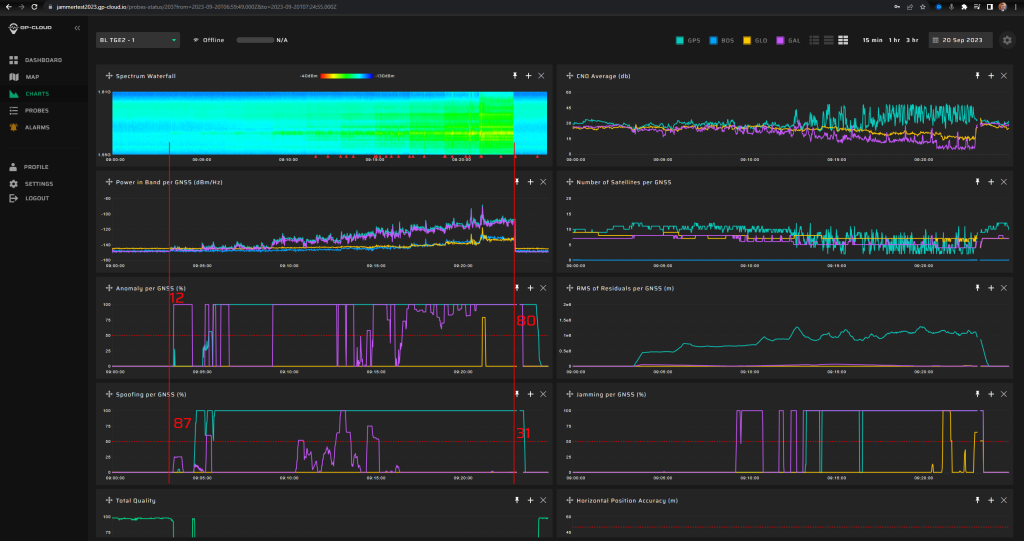
15.1.1 Test: Large position and time jump, gradually increasing signal strength
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
No jamming
Simulated position: 70 N, 10 E
Simulated start time: 01.10.2023 12:00
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
12 |
✓
87 |
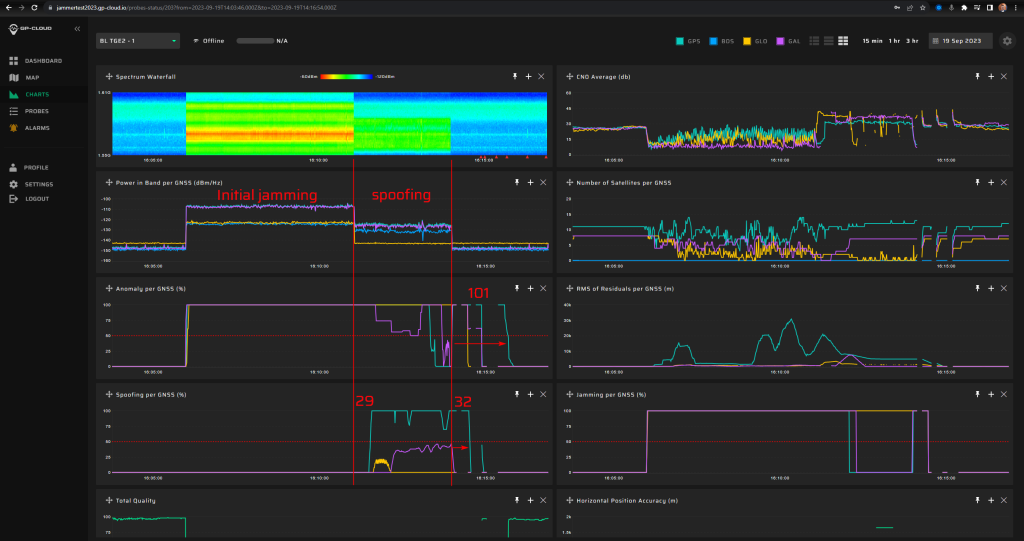
31/80 | Poor sensitivity to Galileo spoofing signatures for this particular case. This will be fixed in the next release of GP-Cloud. Refer to the “Test Results” section of this report. |
Screenshot from GP-Cloud:
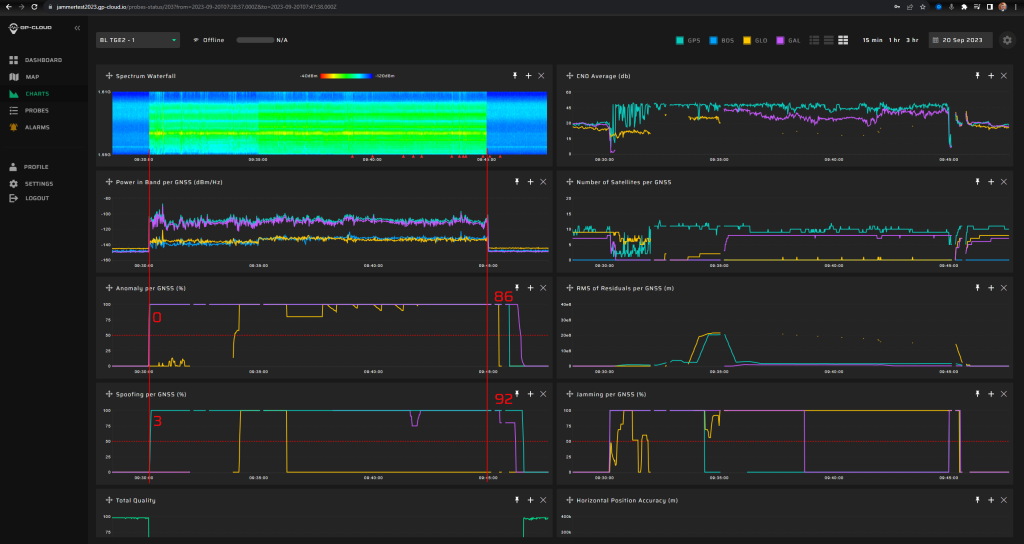
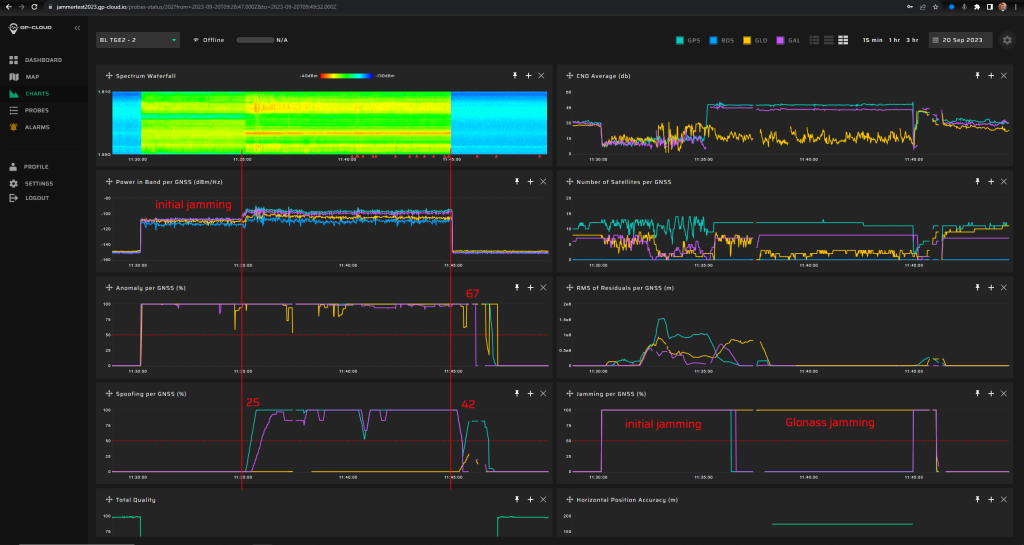
15.1.2 Test: Large position and time jump
Signals:
- GPS L1 C/A
- Galileo E1
No jamming
Position: 70 N, 10 E
Simulated start time: 01.10.2023 12:00
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
3 |
92/86 | There was a false positive of GLONASS spoofing |
Screenshot from GP-Cloud:
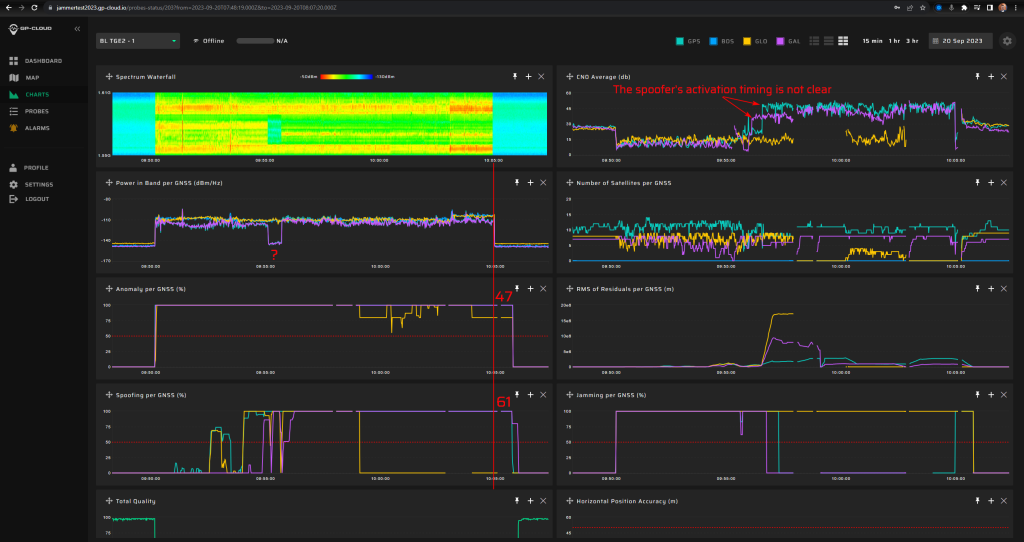
15.1.3 Test: Large position and time jump, with jamming
Signals:
- GPS L1 C/A
- Galileo E1
5 minutes of initial jamming (L1, G1, B1l, E6, L2, E5b, L5 with 2 W) prior to spoofing transmission, then continuous on other bands than the ones spoofed.
Simulated position: 70 N, 10 E
Simulated start time: 01.10.2023 12:00
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
not defined |
47/61 | The moment when the spoofer is switched on could not be determined precisely. Therefore, it is not possible to measure the detection latency.
There was a false positive of GLONASS spoofing. |
Screenshot from GP-Cloud:
15.1.4 Test: Simulated driving (route 1)
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
5 minutes of initial jamming (L1, G1, B1l, E6, L2, E5b, L5 with 2 W) prior to spoofing transmission.
Simulated start position: Bleik community house
Simulated start time: 01.10.2023 12:00
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
11 |
50/78 |
Screenshot from GP-Cloud:
15.1.5 Test: Simulated driving, true reference time (route 1)
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
5 minutes of initial jamming (L1, G1, B1l, E6, L2, E5b, L5 with 2 W) prior to spoofing transmission.
Simulated start position: Bleik community house.
Simulated start time: Referenced to live GPS-signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
4 |
56/116 | Long recovery time |
Screenshot from GP-Cloud:
16 Incoherent spoofing from stationary spoofer using broadcast(true) ephemerides
Simulated signals will be transmitted from a stationary antenna near Bleik community house. Generated spoofing scenarios will use broadcast satellite ephemeris data. Simulated signals may use one or more constellations and one or more signal bands.
Initial positions are either False (e.g. 70 N, 10 E) or True (target location at Bleik community house). Initial time is either False (e.g. a jump in time/date) or True ( < 100 ns timing error for a receiver at target location). Some test scenarios may be started with jamming ((lasting for 5 min, one or several
signal bands, before the spoofing transmission is activated). Some spoofing scenarios may be accompanied by continuous jamming (one or several signal bands).
Static scenarios are a fixed position, while motion scenarios are a simulated drive around Andøya. Each test runs for between 10 and 20 minutes with 5–10 minutes break between each test to allow receivers to reacquire fix onto real satellite signals. For each dynamic test, the motion is first spoofed
to a fixed start position (see 26.8) for 5 minutes before the dynamic motion starts.
16.1.1 Test: Large position jump
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
No jamming
Simulated position: 70 N, 10 E
Simulated start time: Referenced to live GPS-signals
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
26 |
55/55 |
Screenshot from GP-Cloud:
16.1.2 Test: Small position jump, large time jump
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
5 minutes of initial jamming (L1, G1, B1l, E6, L2, E5b, L5 with 2 W) prior to spoofing transmission, then continuous on other bands than the ones spoofed.
Simulated position: North end of the football field – 69.27701401, 15.96932835 4 , 45 m hae. (Height Above Ellipsoid).
Simulated start time: 01.10.2023 12:00.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
25 |
42/67 |
Screenshot from GP-Cloud:
16.1.3 Test: Small position jump
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
No jamming
Simulated position: North end of the football field – 69.27701401, 15.96932835, 45 m hae. (Height Above Ellipsoid)
Simulated start time: Referenced to live GPS signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
12 |
17/66 |
Screenshot from GP-Cloud:
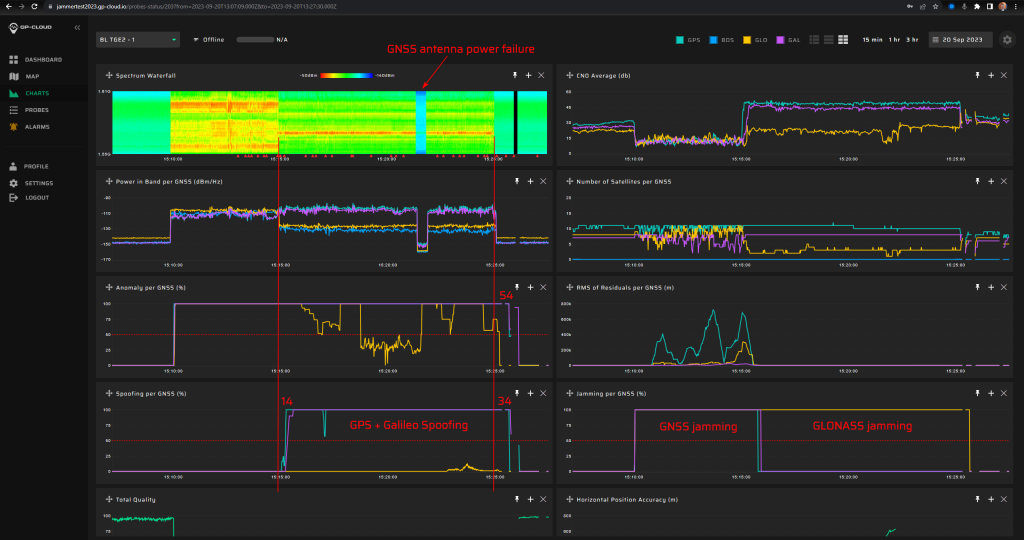
16.1.4 Test: Flying (route 2) – “helicopter scenario”
Signals:
GPS L1 C/A, L2C, L5
Galileo E1, E5
No jamming
Simulated start position: Over the sea 1 km N (Midnattskjæran) at 200 m height.
Simulated start time: Referenced to live GPS-signals.
Spoofing transmission will be corrected for signal delay to simulated start position. Helicopter at start position should see coherent signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
14 |
58/67 | Toward the end of the scenario, there was a power failure of the active GNSS antennas. Minor GLONASS false positives. |
Screenshot from GP-Cloud:
16.1.5 Test: Fixed position
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
No jamming
Simulated position: Cemetery – 69.2824699, 15.9906568, 48 m hae. (Height Above Ellipsoid).
Simulated start time: Referenced to live GPS signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
4 |
✓
15 |
15/19 | In the last 3 minutes of the scenario, spoofing signatures were not detected due to a bug in the classification algorithms. This will be fixed in the next release of GP-Cloud. Refer to the “Test Results” section of this report. |
Screenshot from GP-Cloud:
17 Coherent spoofing from stationary spoofer using broadcast(true) ephemerides
Simulated signals will be transmitted from a stationary antenna near Bleik community house. Generated spoofing scenarios will use broadcast satellite ephemeris data. Simulated signals may use one or more constellations and one or more signal bands.
Initial positions are True (target location at Bleik community house). The initial time is True ( < 100 ns timing error for a receiver at target location). Some test scenarios may be started with jamming (lasting for 5 min, one or several signal bands, before the spoofing transmission is activated). Some spoofing scenarios may be accompanied by continuous jamming (one or several signal bands).
For all of test group 17, the spoofing transmission will be corrected for the signal delay to the simulated start position.
Static scenarios are a fixed position, while motion scenarios are a drive around Andøya. Each test runs for between 10 and 20 minutes with 5 –10 minutes break between each test to allow receivers to reacquire fix onto real satellite signals. For each dynamic test, the motion is first spoofed to a fixed start position (see 26.8) for 5 minutes before the dynamic motion starts.
17.1.1 Test: Simulated driving (route 1). GPS only with initial jamming
Signals:
- GPS L1 C/A, L2C, L5
5 minutes of initial jamming (L1, G1, B1l, E6, L2, E5b, L5 with 2 W) prior to spoofing transmission.
Simulated start position: Bleik community house parking lot.
Simulated start time: Referenced to live GPS-signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
11 |
2/16 |
Screenshot from GP-Cloud:
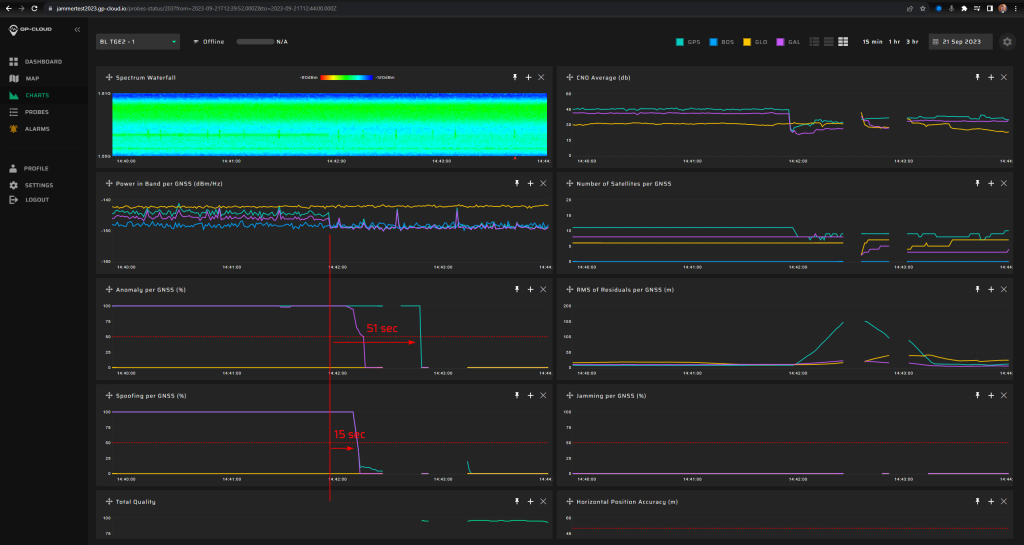
17.1.2 Test: Simulated driving (route 1). Galileo only with initial jamming
Signals:
- Galileo E1, E5
5 minutes of initial jamming (L1, G1, B1l, E6, L2, E5b, L5 with 2 W) prior to spoofing transmission.
Simulated start position: Bleik community house parking lot.
Simulated start time: Referenced to live GPS signals.
Measurement results:
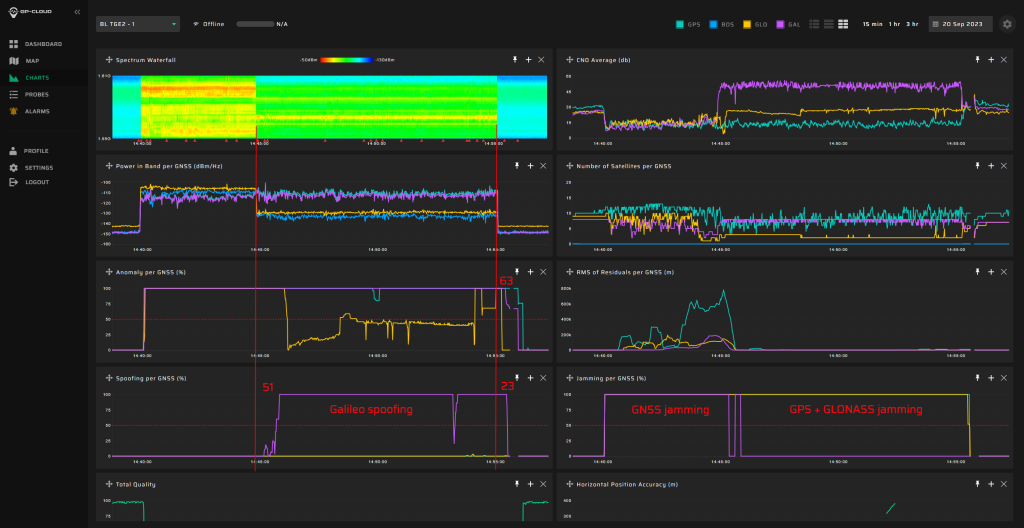
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
1 |
✓
51 |
23/63 |
Screenshot from GP-Cloud:
17.1.3 Test: Simulated driving (route 1) with initial jamming
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
5 minutes of initial jamming (L1, G1, B1l, E6, L2, E5b, L5 with 2 W) prior to spoofing transmission.
Simulated start position: Bleik community house parking lot.
Simulated start time: Referenced to live GPS signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
1 |
✓
14 |
34/54 | During testing, there was an accidental power failure of active GNSS antennas. Well, it’s curious that this fact didn’t affect spoofing detection at all. |
Screenshot from GP-Cloud:
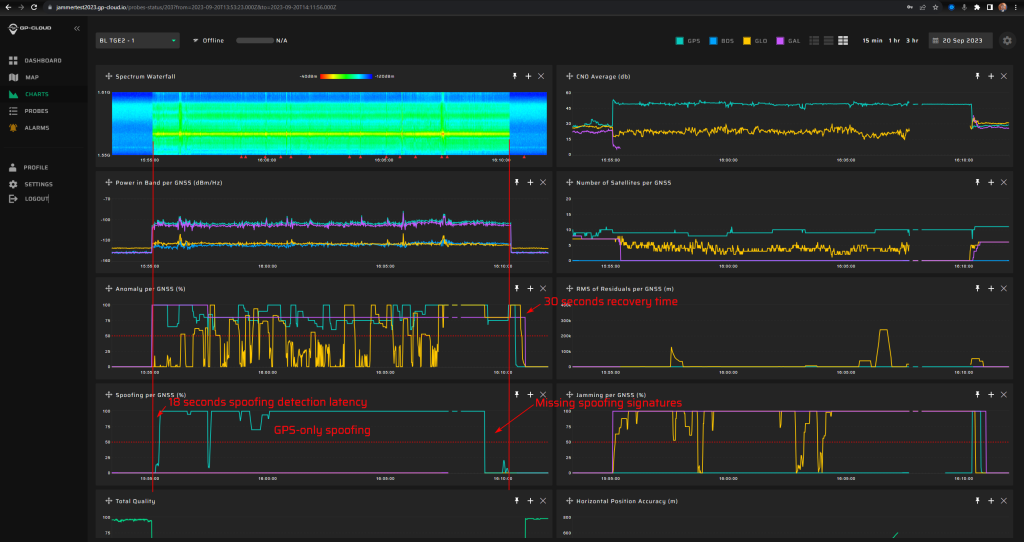
17.1.4 Test: Simulated driving (route 1). GPS only
Signals:
- GPS L1 C/A, L2C, L5
No jamming
Simulated start position: Bleik community house parking lot.
Simulated start time: Referenced to live GPS signals
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
18 |
30 | 1.5 minutes before the end of the scenario, the GPS spoofing signatures stopped being detected due to a bug in the classification algorithms. This will be fixed in the next release of GP-Cloud. Refer to the “Test Results” section of this report. |
Screenshot from GP-Cloud:
17.1.5 Test: Simulated driving (route 1). GPS L1 and Galileo E1
Signals:
- GPS L1 C/A
- Galileo E1
No jamming
Simulated start position: Bleik community house parking lot.
Simulated start time: Referenced to live GPS signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
8 |
11/54 |
Screenshot from GP-Cloud:
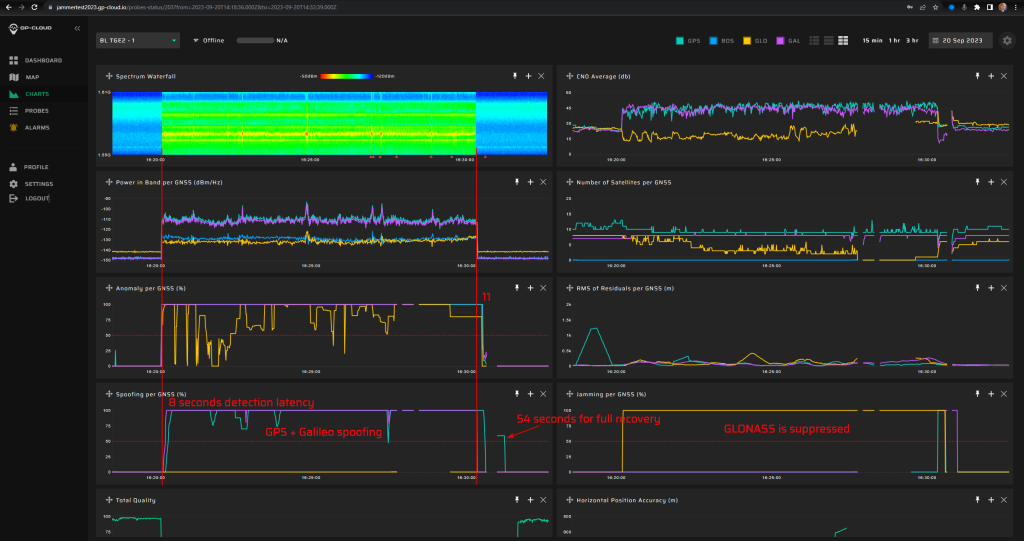
17.1.6 Test: Simulated driving (route 1)
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
No jamming
Simulated start position: Bleik community house parking lot.
Simulated start time: Referenced to live GPS signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
6 |
17/43 |
Screenshot from GP-Cloud:
17.1.7 Test: Flying (route 4) – “drone scenario”
Signals:
GPS L1 C/A, L2C, L5
Galileo E1, E5
No jamming
Simulated start position: 69.277014014, 15.969328354, 40 mhae.
Simulated start time: Referenced to live GPS signals.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
12 |
18/43 |
Screenshot from GP-Cloud:
18 Incoherent time spoofing from stationary spoofer using synthetic ephemerides
Simulated signals will be transmitted from a stationary antenna near Bleik community house. Generated spoofing scenarios will use satellite ephemerides different from live sky satellites. Simulated signals may use one or more constellations and one or more signal bands.
Initial positions are True (target location at Bleik community house). Some test scenarios may be started with jamming (5 min, one or several signal bands). Some spoofing scenarios may be accompanied by continuous jamming (one or several signal bands).
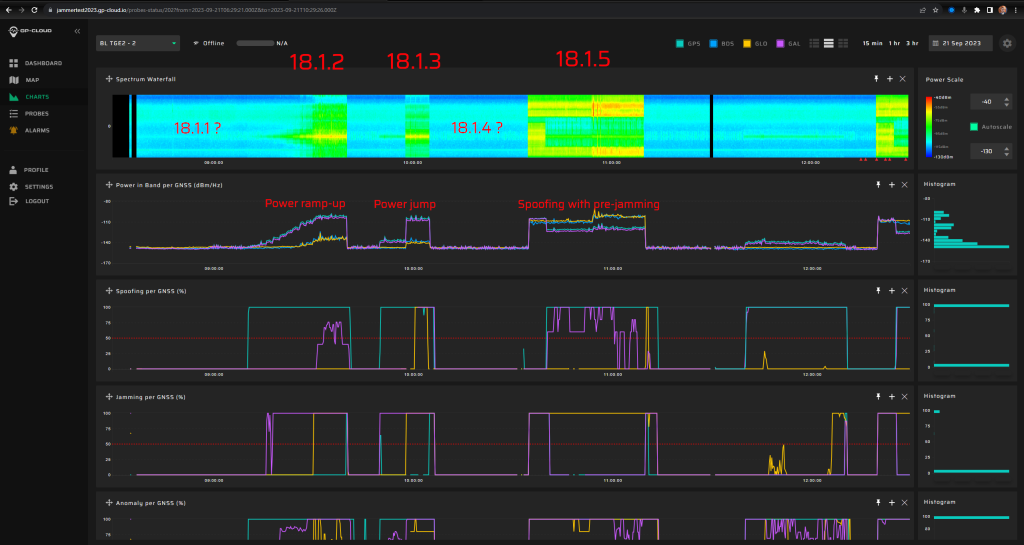
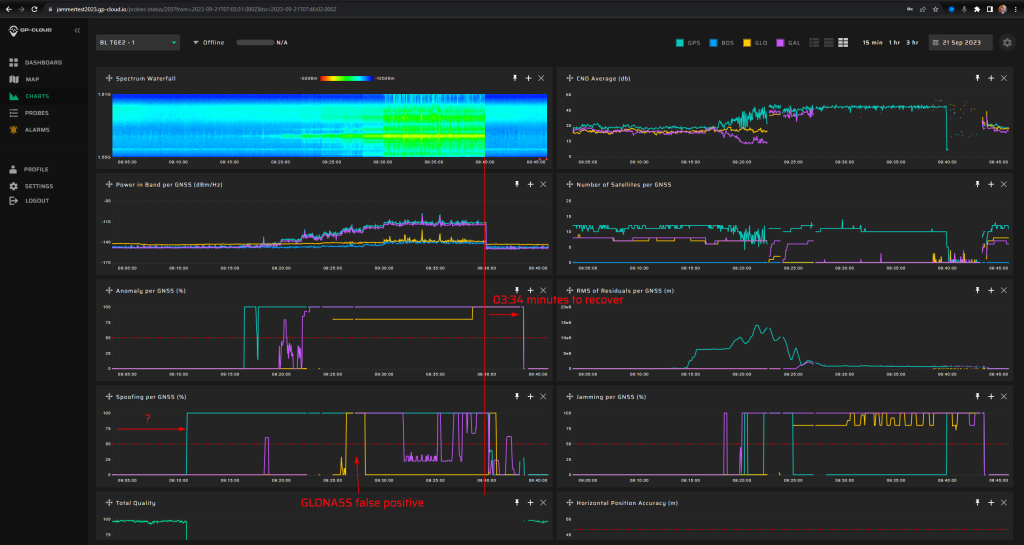
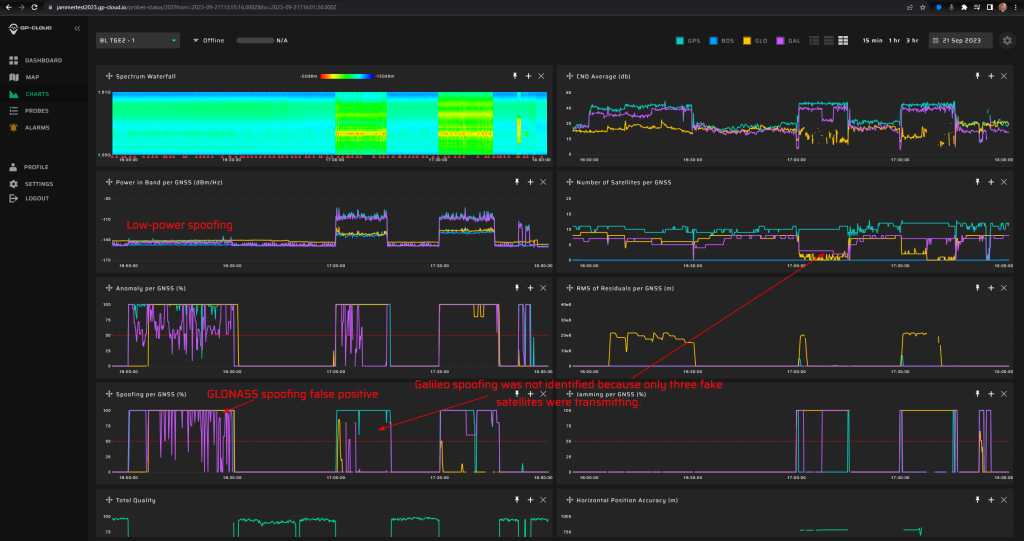
18.1.2 Test: Time offset 15 minutes from real time
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
No jamming.
Fixed spoofed position: 69.27547832, 15.96832496, 35 m hae.
Time offset is + 15 minutes (900 seconds), so “into the future”.
Spoofing power ramp –35 dBm to +15 dBm in steps of 5 dB every two minutes.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
? |
✓
? |
03:34 | The latency of spoofing and anomaly detection cannot be determined since the generation started with very minor power. During the scenario, there was a false positive GLONASS spoofing alarm. A failure in the recovery algorithm caused the long recovery time after the spoofing. |
Screenshot from GP-Cloud:
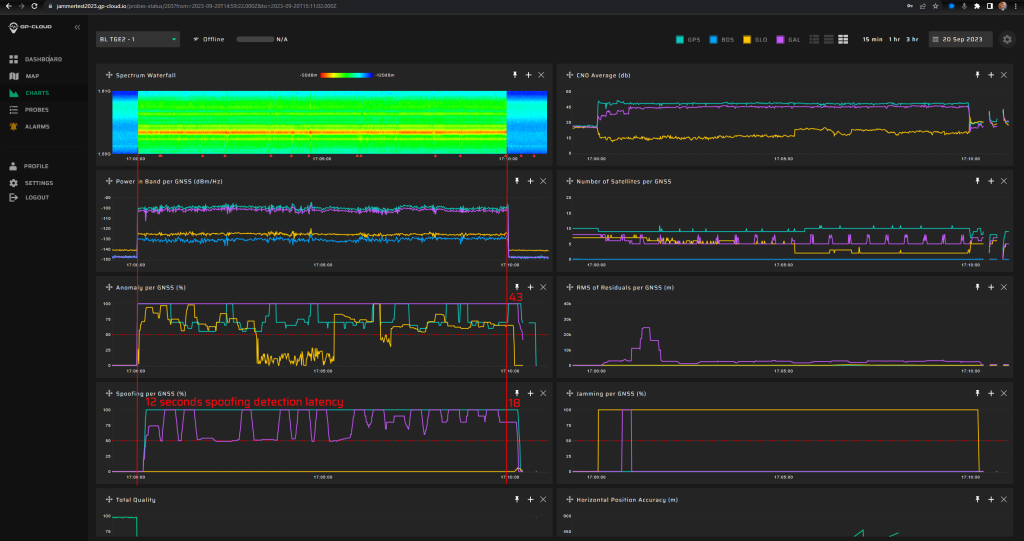
18.1.3 Test: Time offset -3 minutes from real time
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5
No jamming.
Fixed spoofed position: 69.27547832, 15.96832496, 35 m hae.
Time offset is – 3 minutes (180 seconds), so “back into the past”.
Spoofing power will start at -20 dBm and be stepped up to 15 dBm in one step.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
53 |
✓
17 |
73:110 | During the scenario, a GLONASS spoofing alarm of significant duration was registered. Long recovery time. |
Screenshot from GP-Cloud:
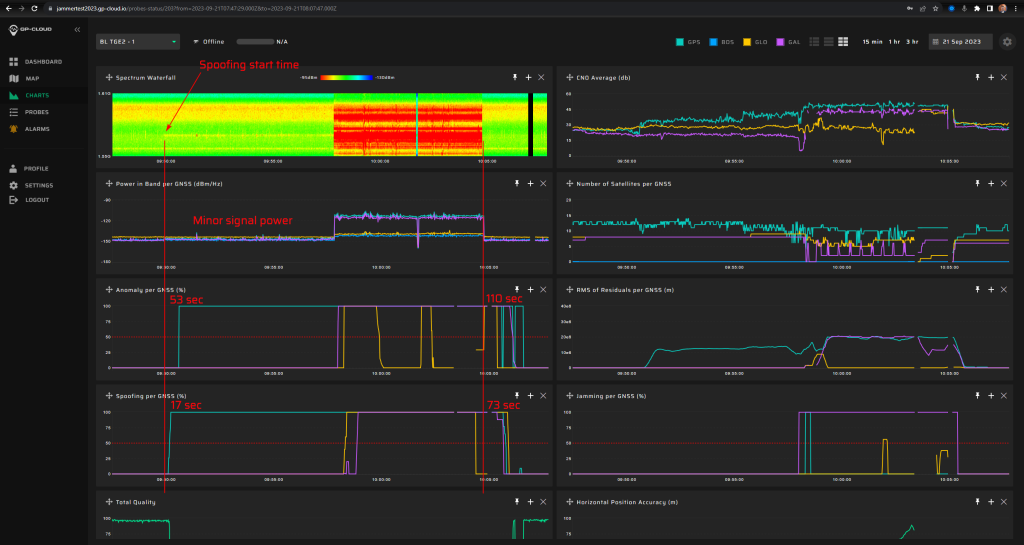
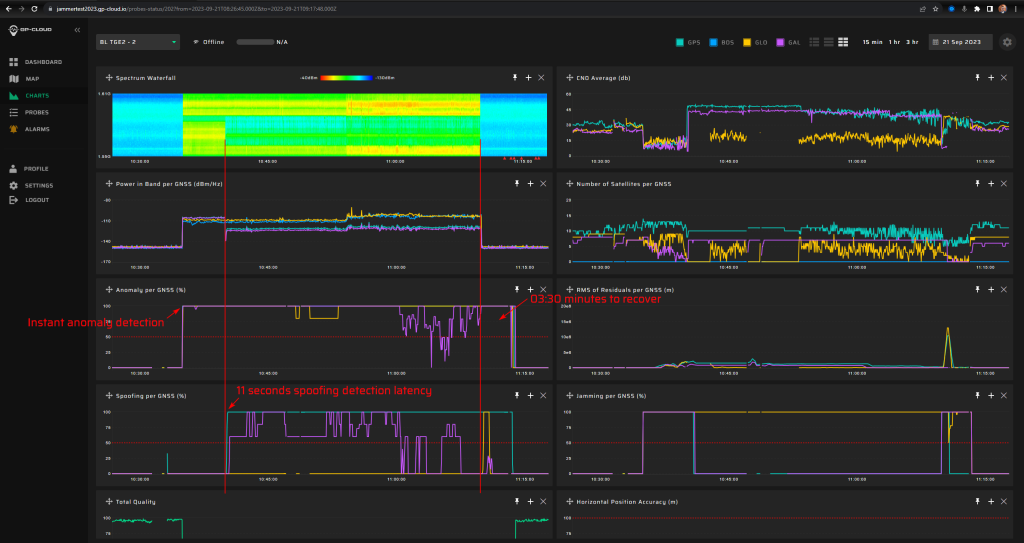
18.1.5 Test: Static + Frequency step (spoofing signal transmission rate change)
Signals:
- GPS L1 C/A
- Galileo E1
5 minutes of initial jamming (L1, G1, B1l, L2, E5b, L5 with 2 W) prior to spoofing transmission.
Fixed spoofed position: 69.27547832, 15.96832496, 35 m hae.
Spoofing power will be at 0 dBm.
Frequency steps are added (10 ns/s) and starts five minutes after the spoofing starts.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
11 |
03:30 | A failure in the recovery algorithm caused the long recovery time after the spoofing. |
Screenshot from GP-Cloud:
19 Coherent time spoofing from stationary spoofer using broadcast(true) ephemerides
Simulated signals will be transmitted from a stationary antenna near Bleik community house. Generated spoofing scenarios will use broadcast satellite ephemeris data. Simulated signals may use one or more constellations and one or more signal bands.
Initial positions are True (target location at Bleik community house). Initial time is True ( < 100 ns timing error for a receiver at target location). Some test scenarios may be started with jamming (5 min, one or several signal bands). Some spoofing scenarios may be accompanied by continuous jamming (one or several signal bands).
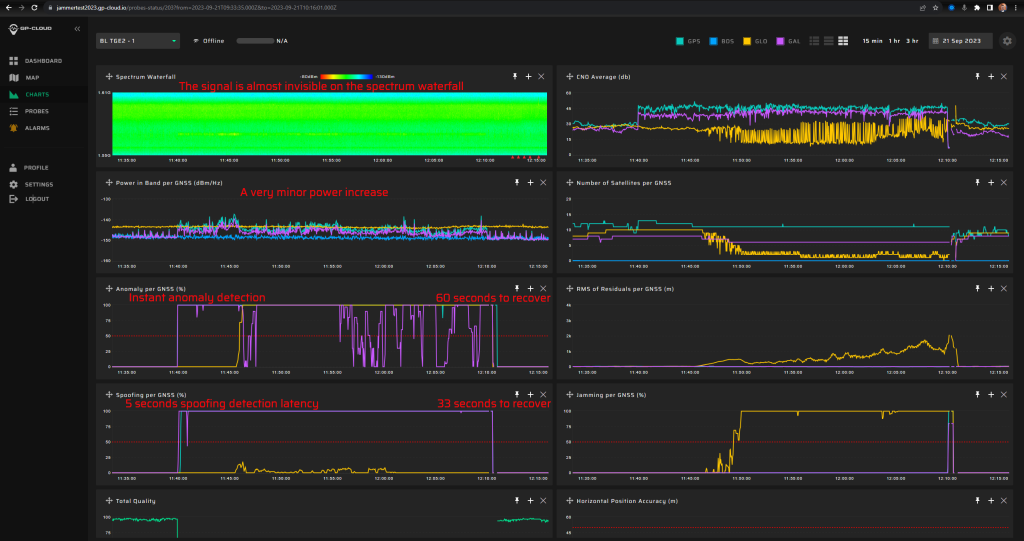
19.1.1 Test: Static + Frequency step (spoofing signal transmission rate change)
Signals:
- GPS L1 C/A
- Galileo E1
No jamming.
Fixed spoofed position: 69.27547832, 15.96832496, 35 m hae.
Frequency steps are added (10 ns/s), and start five minutes after the spoofing starts.
Spoofing power will be at -20 dBm.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
5 |
33/60 |
Screenshot from GP-Cloud:
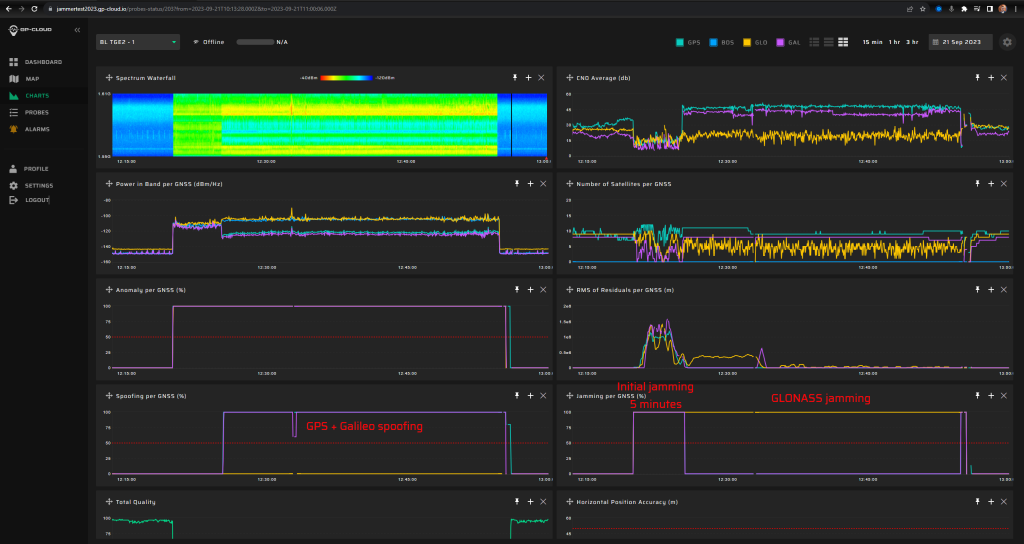
19.1.2 Test: Static + Frequency step (spoofing signal transmission rate change)
Signals:
- GPS L1 C/A
- Galileo E1
5 minutes of initial jamming (L1, G1, B1l, L2, E5b, L5 with 2 W) prior to spoofing transmission, then continuous on other bands than the ones spoofed.
Fixed spoofed position: 69.27547832, 15.96832496, 35 m hae.
Frequency steps are removed (10 ns/s) and start five minutes after the spoofing starts.
Spoofing power will be at 0 dBm.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
5 |
65 |
Screenshot from GP-Cloud:
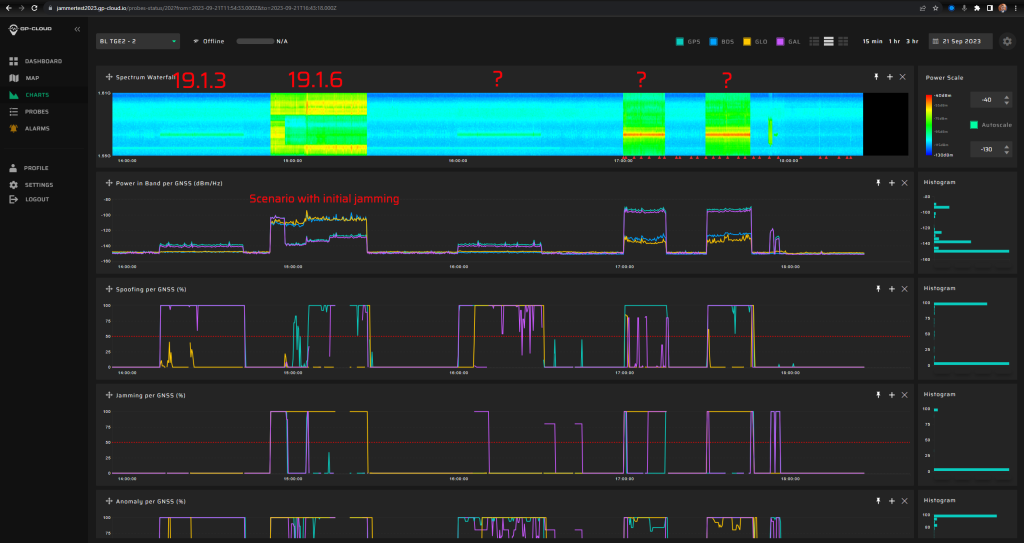
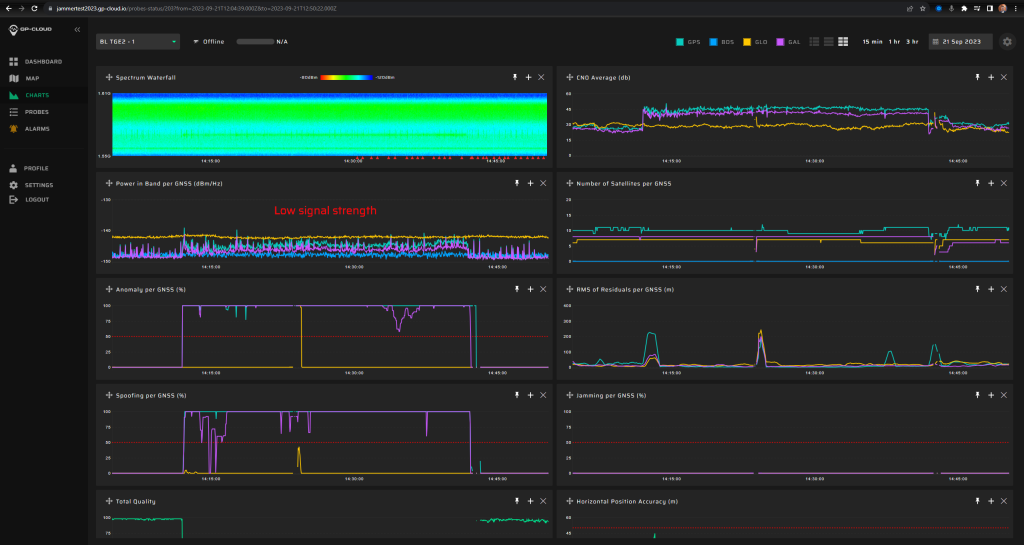
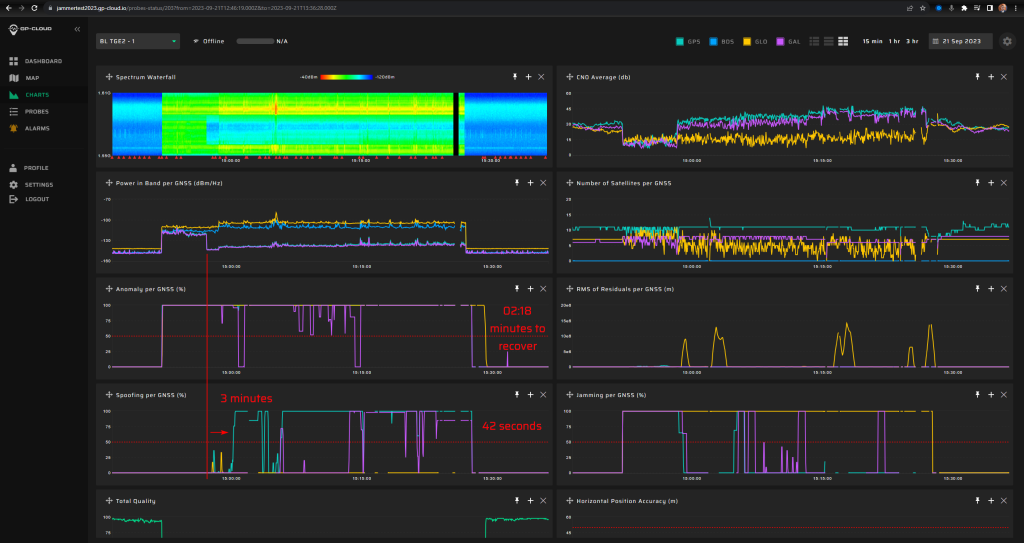
Signals:
- GPS L1 C/A, L2C, L5
- Galileo E1, E5.
5 minutes of initial jamming (L1, G1, B1l, L2, E5b, L5 with 2 W) before spoofing transmission.
Fixed spoofed position: 69.27547832, 15.96832496, 35 m hae.
Spoofing power will be at -20 dBm.
Spoofing says that back in 2016, there were 19 leap seconds instead of 18.
Measurement results:
| Anomaly Detection and Latency (s) | Spoofing Classification and Latency (s) | Recovery Time (s) | Comments |
| ✓
0 |
✓
3 minutes |
42 seconds to reset the spoofing flag.
2 minutes 18 seconds to reset the anomaly flag. |
This was the most difficult spoofing scenario to detect. Long latency for GPS spoofing detection. Galileo’s spoofing signatures were only detected in the second part of the scenario. But in any case, anomalies are detected instantly. Long recovery time. |
Screenshots from GP-Cloud:
Testing Outcomes
Anomaly Detection Latency
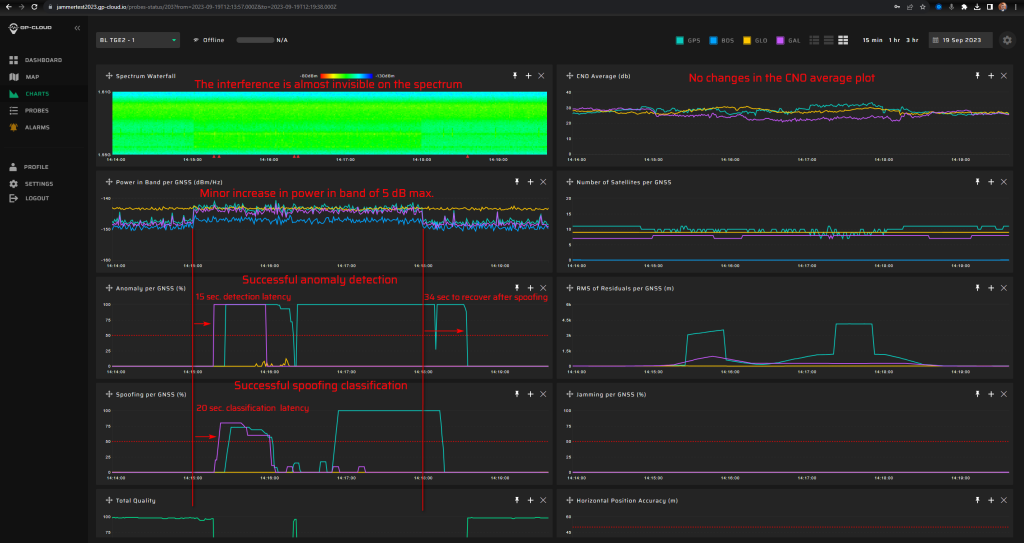
The system was able to detect anomalies in GNSS signals within a few seconds (in most cases instantly) for all test scenarios except four: 11.1.1, 15.1.1, 18.1.2, 18.1.3. These scenarios involved incoherent spoofing attacks with very low initial signal strength.
Incoherent spoofing with low power is not dangerous for a GNSS receiver that is tracking actual satellites, as such incoherent signals are perceived as noise. For an incoherent attack to succeed, it must significantly increase in power, causing the target receiver to lose track of the real satellites and switch to search mode. Therefore, a slightly increased anomaly detection delay in these cases is not critical.
This outcome is considered very positive. The reaction speed of the system is critically important since there is only a 15-second window to respond to spoofing attempts and protect critical infrastructure. The urgency and significance of a high-speed response for such systems are further elaborated in the article available at The Significance of Low GNSS Spoofing Detection Latency.
Spoofing Classification Latency
In assessing the response to incoherent attack scenarios, the following statistics were observed for the delay in classifying interference as spoofing:
- Minimum Delay: 3 seconds
- Average Delay: 13.4 seconds
- Maximum Delay: 26 seconds
*Statistics for coherent attacks exclude scenarios where the attack began with minor spoofing strength.
Statistics for coherent attacks:
- Minimum Delay: 6 seconds
- Average Delay: 14 seconds
- Maximum Delay: 51 seconds
*Statistics for coherent attacks exclude meaconing and item 19.1.6.
Spoofing Classification Accuracy
Spoofing classification algorithms worked perfectly in almost all episodes except the following:
- 15.1.1 Test: Large position and time jump, gradually increasing signal strength.
Low sensitivity to Galileo spoofing signatures. - 18.1.2 and 18.1.3 Tests.
Galileo spoofing signatures were only detected in the second half of the scenario with higher fake signal strength. - 18.1.5 Test: Static + Frequency step (spoofing signal transmission rate change)
Low sensitivity to Galileo spoofing signatures in the last third of the scenario - 19.1.6 Test: Static + UTC-parameter navigation data manipulation.
Long latency of Galileo’s spoofing detection due to the complexity of the stack scenario.
In certain instances of GPS and Galileo experiencing incoherent spoofing, the system incorrectly flagged GLONASS for spoofing as well. This is a result of the algorithm’s intentional design. When the system cannot verify the authenticity of signals from any one constellation and simultaneously detects spoofing on others, it will indicate a spoofing alert across the board. This is a safety measure to ensure the protection of critical infrastructure, even if it means accepting some false positives.
In scenarios 16.1.5 and 17.1.4, spoofing detection stopped 12-14 minutes after the attack started due to a simple bug in the algorithms 🙂
Recovering From Spoofing
In all cases, the system successfully recovered the tracking of real signals after spoofing using built-in algorithms without external assistance. The statistics on recovery times are as follows:
- Minimum recovery time: 25 seconds
- Average recovery time: 69.9 seconds
- Maximum recovery time: 214 seconds
Some longer recovery times were due to errors in the system’s recovery process in cases 11.1.6, 11.1.7, 15.1.2, 15.1.4, 15.1.5, 18.1.2, 18.1.3, 18.1.5, 19.1.6. These errors are being fixed in the next update of the GP-Cloud software. If we do not take into account the cases listed above, the recovery time statistics will be as follows:
- Minimum recovery time: 25 seconds
- Average recovery time: 50.6 seconds
- Maximum recovery time: 71 seconds
Improvement Plans
Our experience at JammerTest2023 demonstrated the effectiveness of our GNSS interference detection and classification system, while also highlighting areas for improvement. In our forthcoming GP-Cloud update, we aim to:
- Enhance the detection sensitivity for Galileo spoofing attempts.
- Reduce false positives for GLONASS spoofing when other constellations are being spoofed.
- Fix identified issues within our recovery algorithms.
- Resolve additional bugs found in our classification algorithms.
Despite these areas for improvement, we are confident that our system stands out in the market for its comprehensive functionality, rapid response capability, and precise classification. We believe in transparency about our system’s limitations because we have clear strategies for addressing them.
Our commitment is to continually advance our technology to provide the most dependable protection against GNSS threats to critical infrastructure.
Access to Recorded Data
Book an online meeting with the GPSPATRON team to perform a joint analysis of recorded data in the GP Cloud.