Intro
From 19 to 23 September 2022, the Norwegian Public Roads Administration, the National Communications Authority, and the Norwegian Defense Research Institute hosted “JammerTest2022” in northern Norway. In our opinion, this is the biggest civilian GNSS jamming/spoofing testing we know about and where we participated.
Over five days, a wide range of GNSS interference was generated to test GNSS equipment resilience. From basic L1 jamming to sophisticated spoofing scenarios.
GPSPATRON’s team has recorded all the interference in the GP-Cloud database and is making it open to the community!
Key Facts
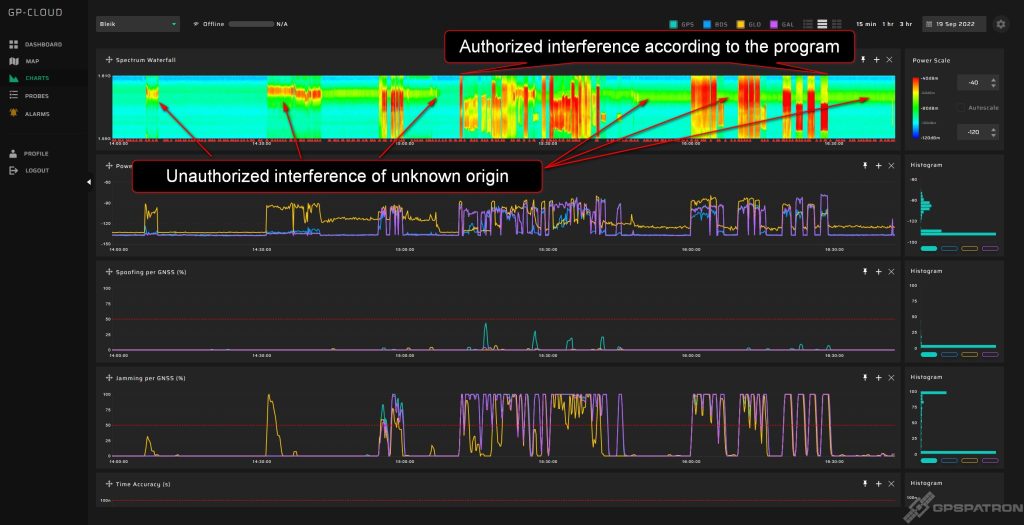
- Unauthorized long-term jamming on the first day of testing was detected.
- Under the influence of a certain type of jamming, a GNSS receiver can produce coordinates with errors of tens of kilometers. What should we call spoofing or jamming?
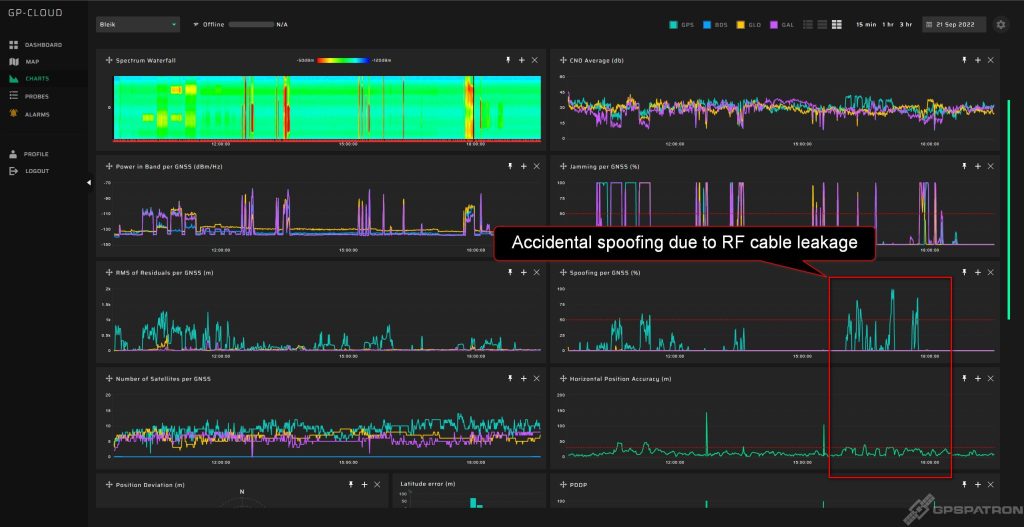
- At the end of the third day, unauthorized spoofing was detected. The guys from the Norwegian Metrology Service were practicing before the upcoming spoofing tests with their GNSS simulator with conducted connection to the DUT. However, improper RF accessories led to fake signal leakage.
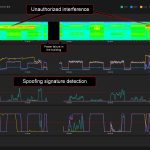
- Our system successfully detected all spoofing scenarios! Our method with 3 antennas and spatial signal processing demonstrated excellent performance.
GPSPATRON Equipment Used
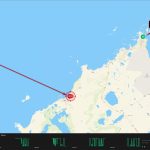
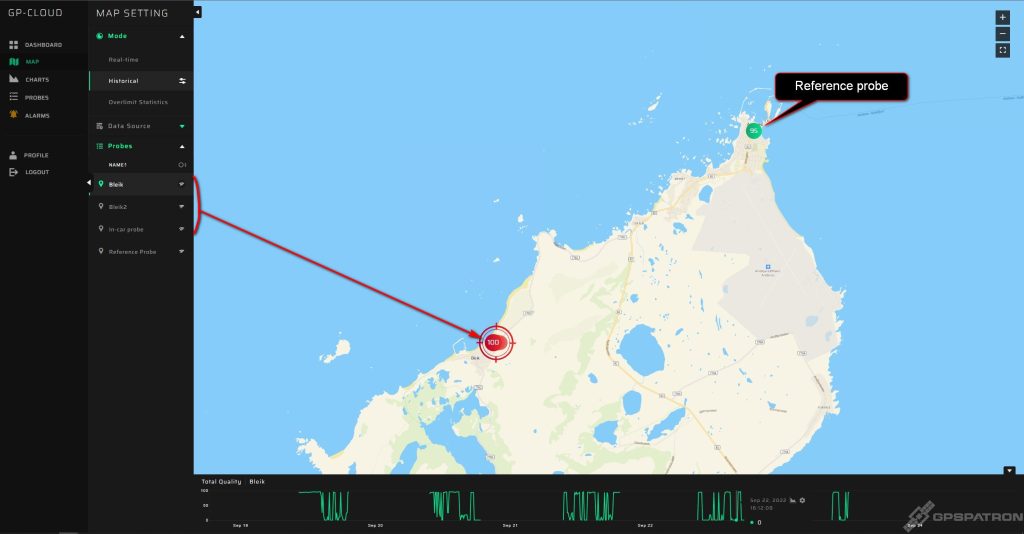
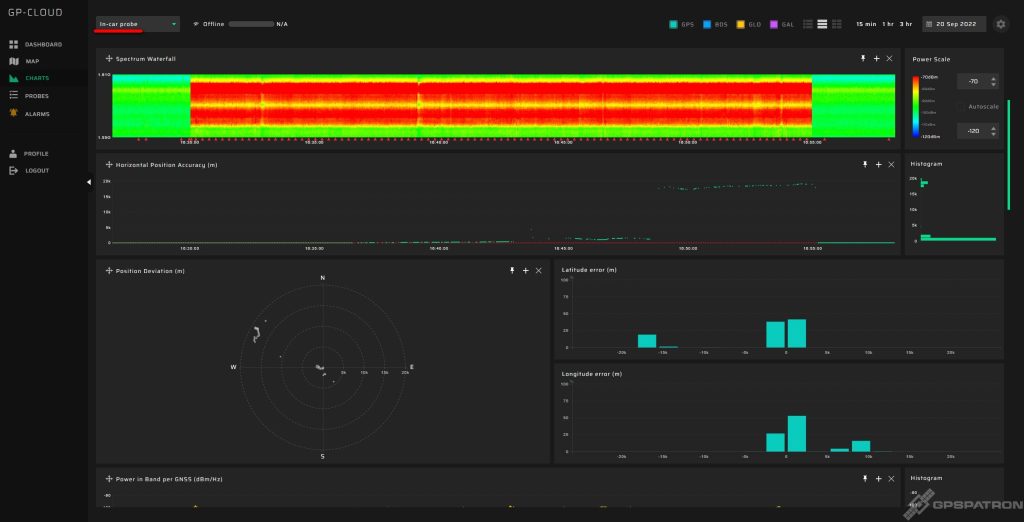
We installed 3 GP-Probe TGE2 in the testing area and one probe in a nearby town as a reference. The probes streamed real-time data to GP-Cloud.
| Probe name | Operating time |
| Reference Probe | Nonstop from September 18 to September 23 |
| Bleik | Five days during the testing. Usually from 9 a.m. to 6 p.m. |
| Bleik2 | The last two days during the spoofing tests. |
| In-car Probe | It was turned off from time to time. |
The system supports two modes of interference detection optimization. The “Bleik2” sensor was in “Low Latency Optimisation” mode. Other sensors were in the “False Positive Optimisation” mode. The “Low Latency Optimisation” mode triggers faster and is more sensitive, but demonstrates a higher false-positive detection rate.
To detect jamming, the system can analyze power in band or degradation of signal-to-noise ratio and number of visible satellites. The first option is too simple, so all probes were configured for SNR analysis. However, this analysis requires a 24-hour pre-calibration for better performance.
All probes were connected to the Internet via the built-in 4G modem. In the middle of the fourth day, there was a connection failure and we lost some data.
Testing Program
The event was conducted within five days. Jammers were launched the first three days, then there were different spoofing scenarios.
The links below provide the official testing program and technical specifications of the GNSS jammers used.
Day 1. Part 1. Commercial jammers
Test time from 14:00 to 15:30
Testing began with commercially available jammers:
Our findings and observations:
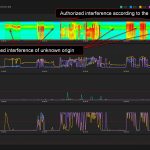
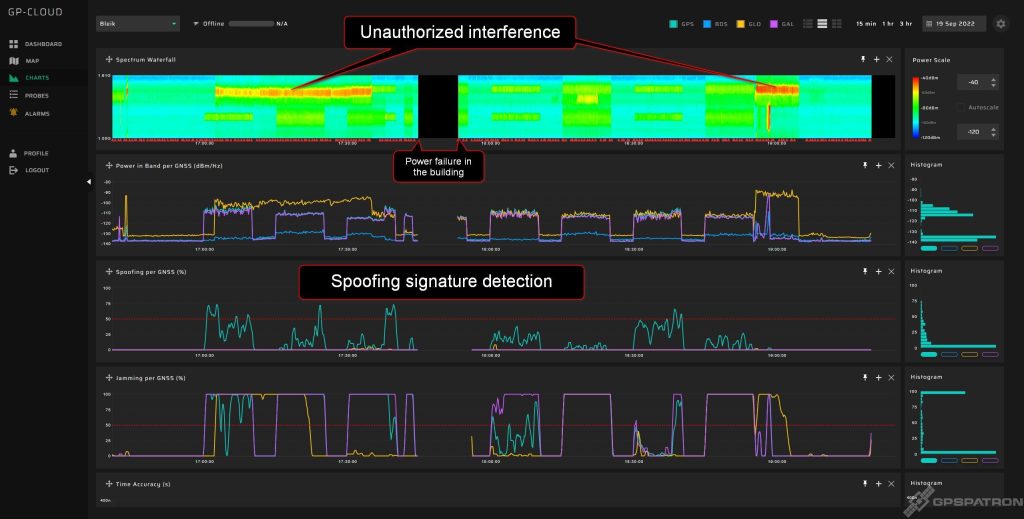
Our system detected the unauthorized interference about 40 minutes before the official tests started. The interference was active during the entire test. The power of the interference was constantly changing, which may indicate that the jammer was placed in a car. The interference spectrum is quite strange. The center frequency is around 1601 MHz. Pulse modulated signal.
Day 1. Part 2. High Effect Jammer
Test time from 16:00 to 17:30
The High Effect Jammer with a directional antenna was installed about 600 meters from the test site:

Our findings and observations:
- We observed the same interference as in the first part.
- There was a power outage in the building for a few minutes and we have a loss in data 🙁
- The system detected some spoofing signatures under jamming. But nevertheless, the incidents were correctly classified as jamming in the incident list. At first, we were confused but then we saw a serious increase in residuals and degradation of accuracy. We use many metrics to classify interference into spoofing and jamming. But there is one common approach. If the interference only degrades the signal-to-noise ratio, it is labeled as jamming. If the interference significantly degrades position or time accuracy, it is labeled as spoofing. Look at the second day’s data to see why we think this is the right approach.
Day 2. Part 1. High Effect Jammer. Power Ramp
Test time from 09:00 to 13:00
The same set of equipment was used as on the first day. The only difference is that the interference power increased in steps.
We found nothing interesting except the same interference of unknown origin as on the first day.
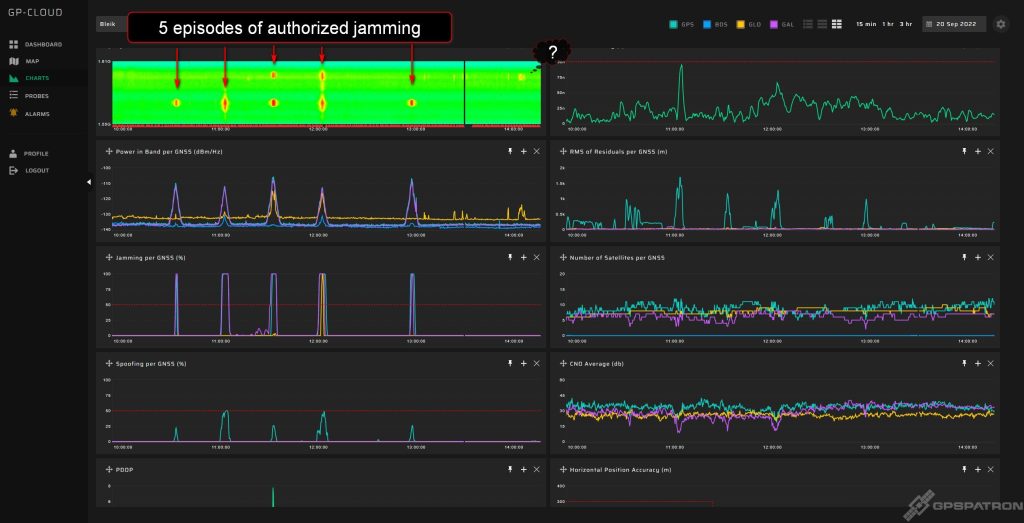
Day 2. Part 2. Long Time High Effect Jammer
Test time from 14:00 to 18:00
PPS input of the probe called “Bleik” was connected to the time reference provided by the Justervesenet (Norwegian Metrology Service).
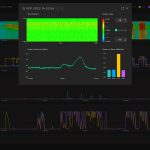
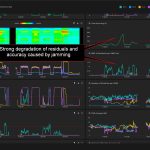
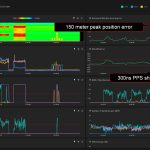
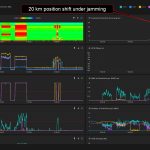
Our system detected spoofing signatures under jamming, just like in the previous testing sessions. The probe “Bleik” showed degradation of position accuracy in the peak up to 150 meters and a decrease in PPS phase accuracy up to 300 ns. At the same time, the probe called “In-car” showed a dramatic jump of 20 kilometers. And here arises a critical question of the correct classification of interference into spoofing and jamming.
Day 3. Different Jamming Scenarios
Test time from 09:00 to 18:00
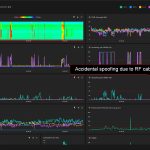
Nothing interesting happened on the third day of testing except an accidental leak of a fake GNSS signal. Our probes, GNSS antennas, and RF cables were located near the GNSS simulator owned by the Justervesenet (Norwegian Metrology Service). The guys were practicing for tomorrow’s tests. Although the GNSS receiver under test was connected to the simulator by cable, there was an RF signal leak. The power of the fake signal was really insignificant. Only several GPS satellites were overpowered. However, this led to some degradation in the accuracy of the position
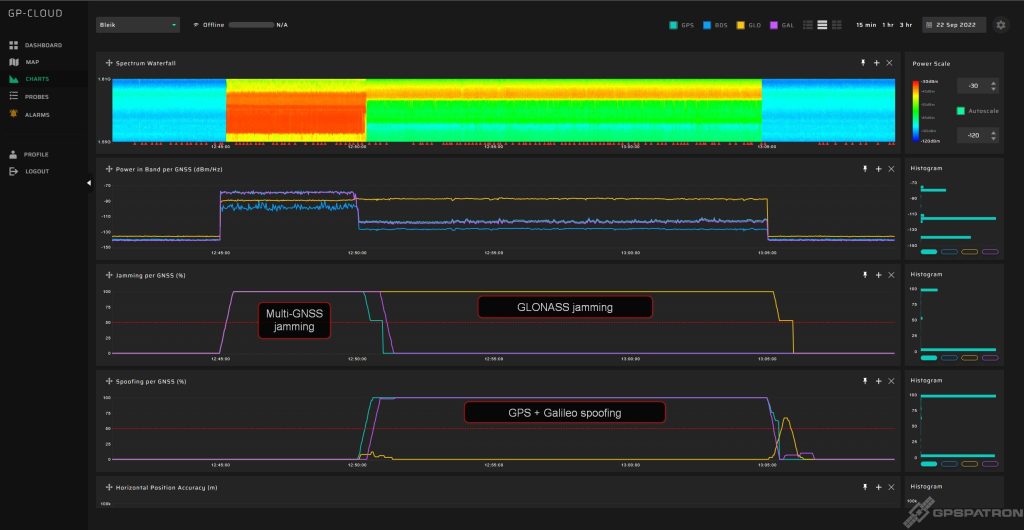
Day 4. Part 1. Simple GPS and Galileo Spoofing
Test time from 09:00 to 13:00
The guys from the Justervesenet (Norwegian Metrology Service) were responsible for spoofing. They were heavily restricted by the regulator. It was allowed to generate a fake signal covering no more than 100 meters in radius. Everyone who is familiar with spoofing understands that it is extremely difficult to implement in practice. The coverage area depends on the attack scenario, the received power of the real signals, the terrain, and other conditions of signal propagation. Therefore, it was decided to gradually increase the power of the fake signal up to the appropriate level.
In the first part, asynchronous (non-coherent) attacks were launched with incorrect coordinates, time, and ephemeris. Only the GPS and Galileo constellations were simulated. GLONASS was suppressed with a jammer. Before each spoofing, all systems were suppressed for about 5 minutes. As you can see, “simple spoofing” is not so simple 🙂
At the very end of the first part, the guys apparently forgot to turn off the spoofer between tests.
There were multiple 4G connection failures around noon. So we lost some data.
Day 4. Part 2. Advanced GPS and Galileo Spoofing
Test time from 14:00 to 18:00
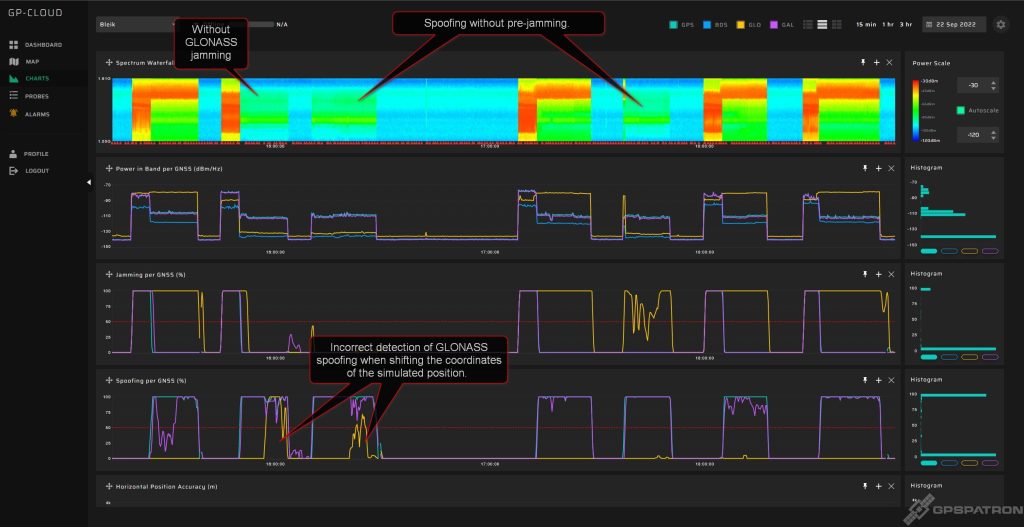
In the second part, coherent scenarios were run with true time, coordinates, and ephemeris.
We faced with the following: when shifting the coordinates of the synthetic GPS and Galileo signals, our system detects anomalies in the GLONASS signal and classifies this as spoofing.
We have already figured out how to fix it 🙂
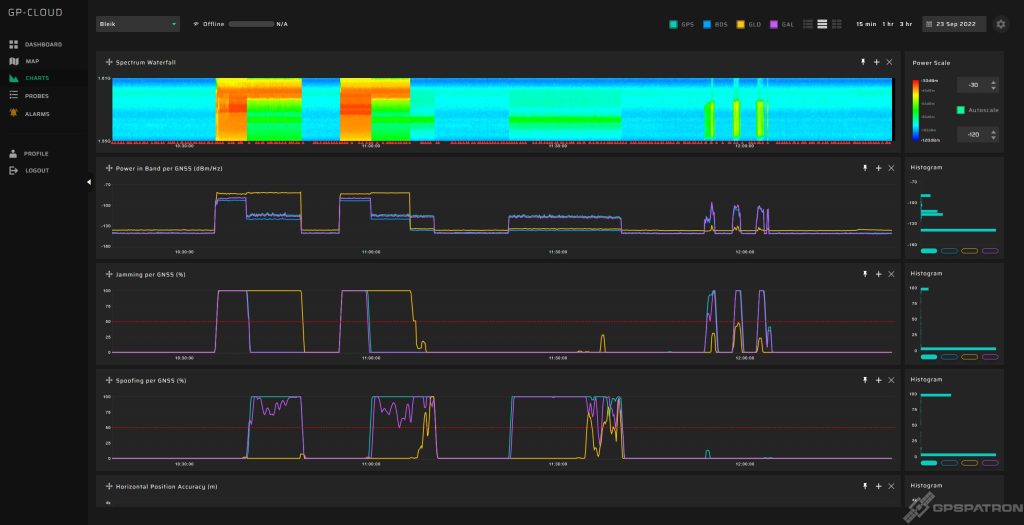
Day 5. Advanced Spoofing + Jamming
Test time from 09:00 to 13:00
On the last day, three spoofing and jamming scenarios were run. Nothing interesting.
How to Get Access to GP-Cloud
To access the database of recorded interference, please watch the video tutorial below and then fill out the google form.