In this post, we collect the different types of GNSS interference that we detect around the world. We are going to update this post from time to time and possibly change the classification of interference in the future.
For timely updates, follow GPSPATRON on Twitter and LinkedIn. You will find fresh attack scenarios there.
We demonstrate only basic screenshots from our GP-Cloud software, such as spectrograms, power spectrum, spectrum waterfall, and basic parameters of GNSS signals.
If you are interested in accessing more detailed data please leave a message on the contact page.
GNSS Jamming
GNSS jammers vary in output power, modulation types, and spectrum width. Below we have collected and categorized the most popular jammers.
High-Quality Jammer
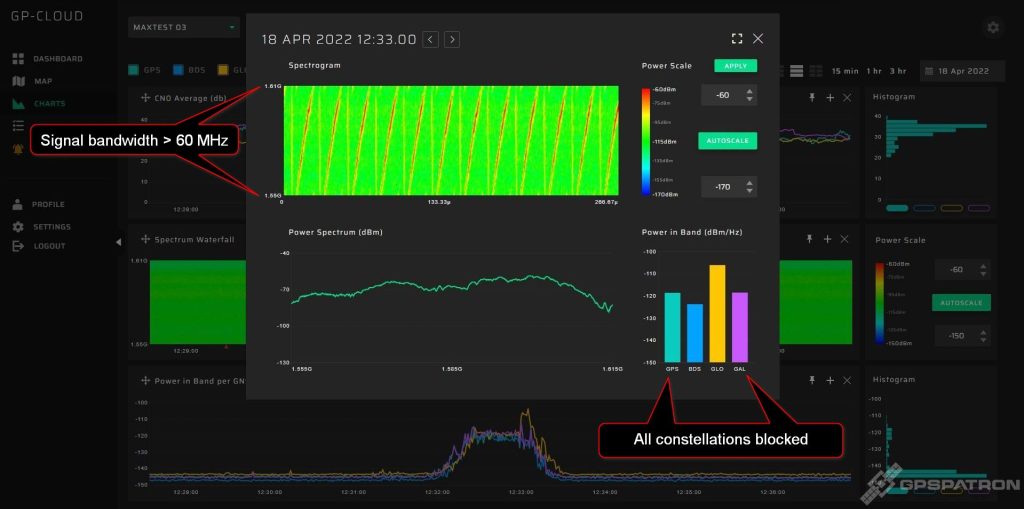
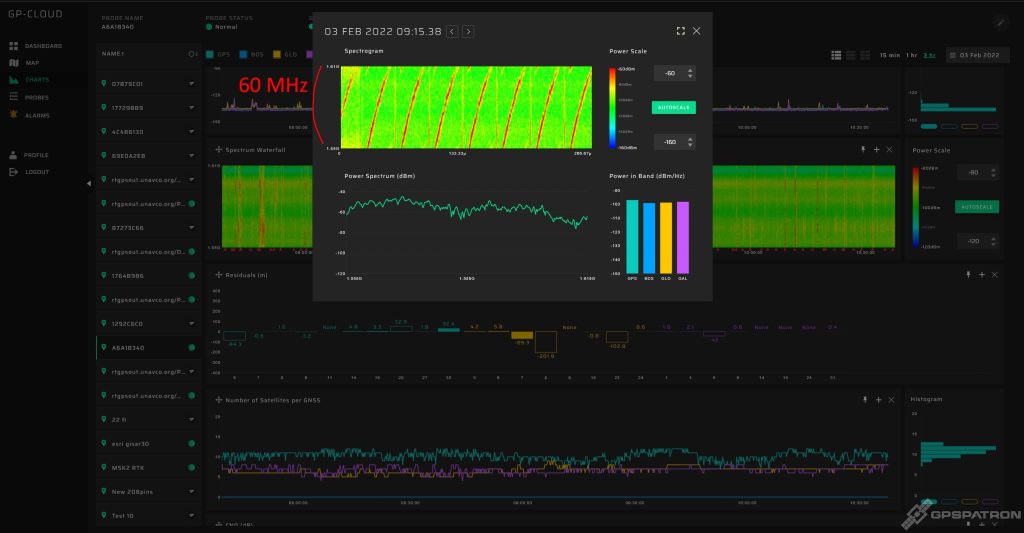
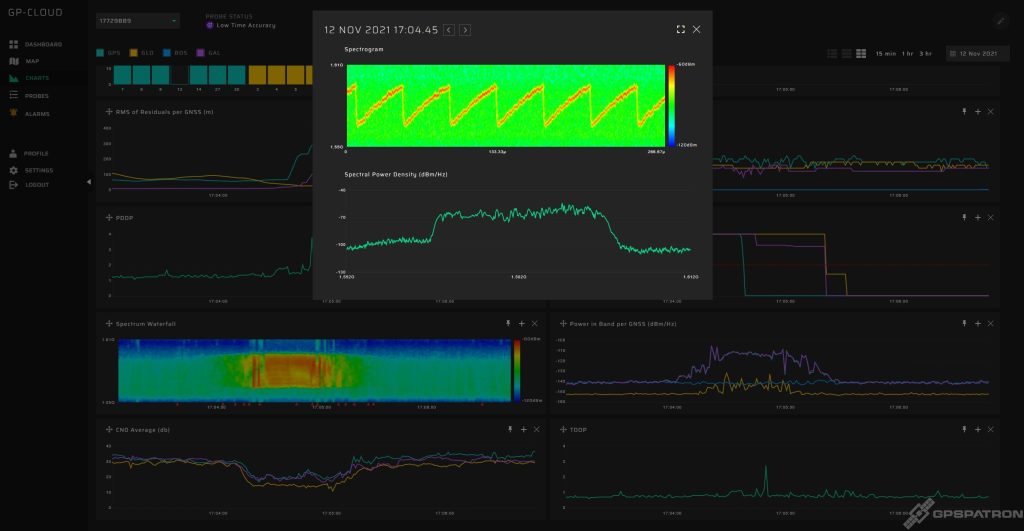
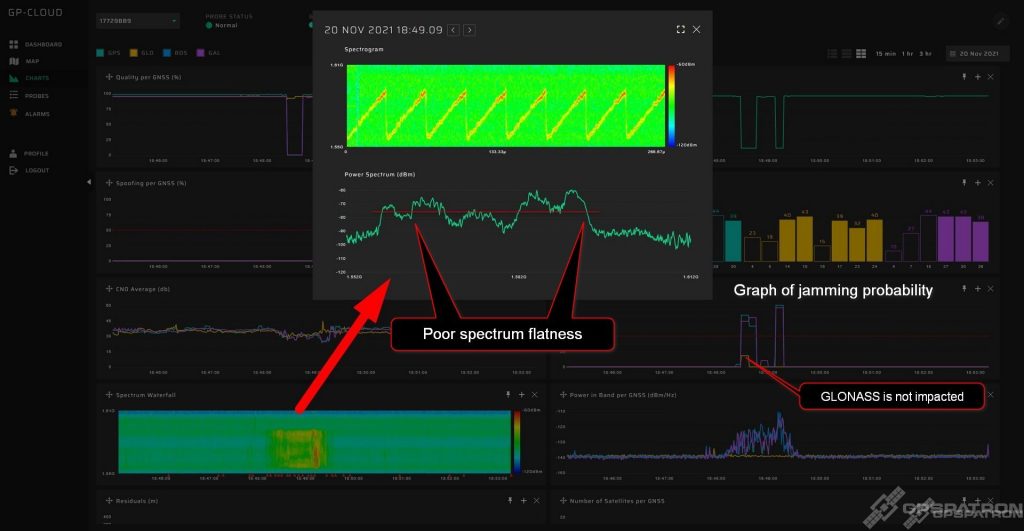
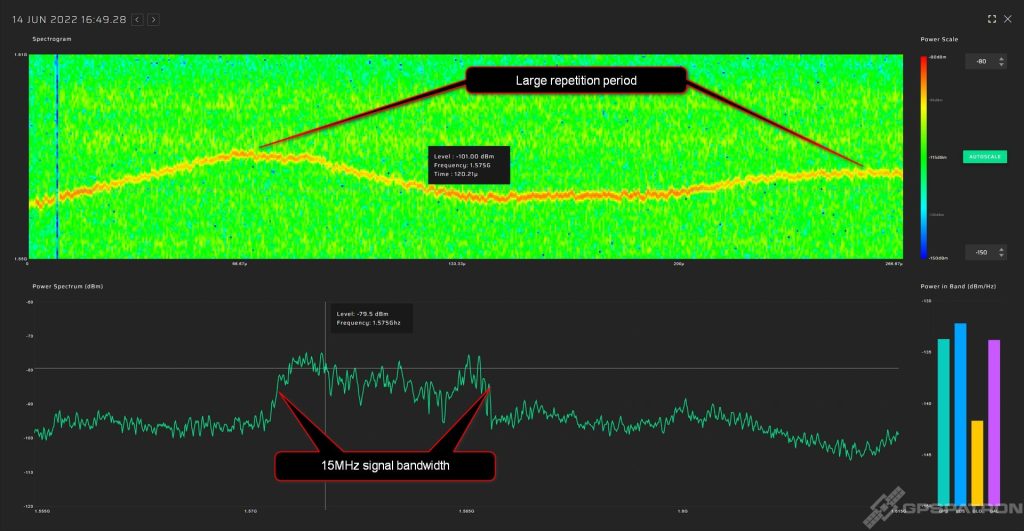
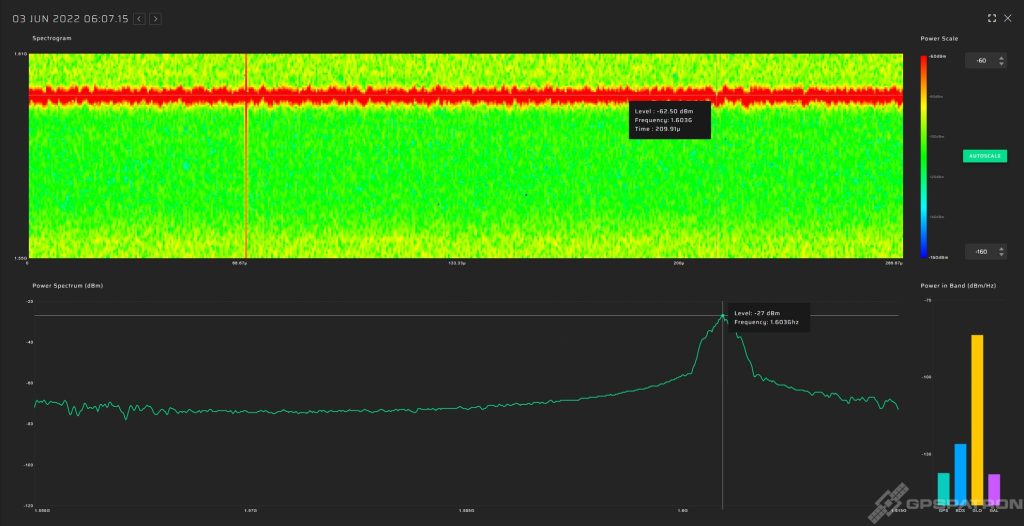
This is quite a rare beast. It’s really wideband – over 60 MHz. This particular sample is perfectly calibrated for center frequency and has pretty good spectrum flatness for that kind of device.
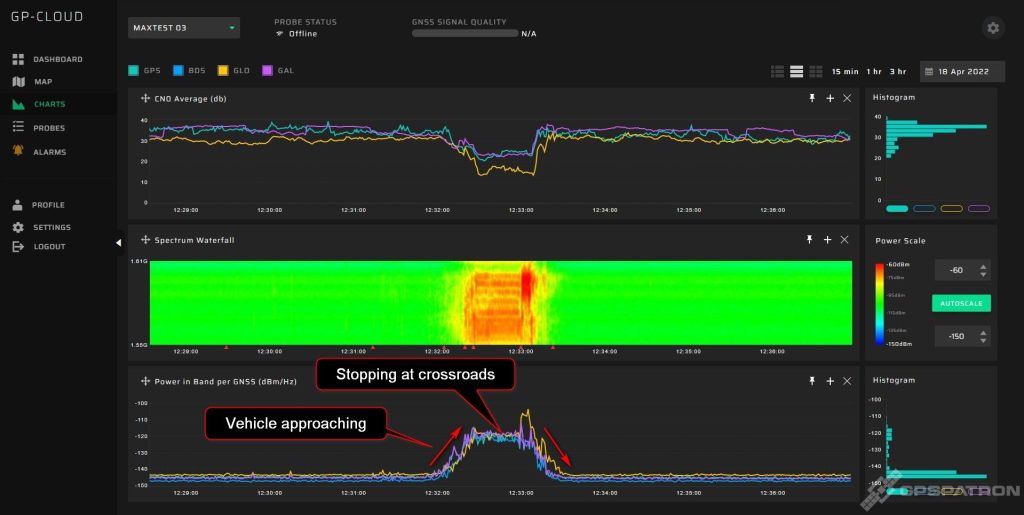
We caught him at a crossroads. Obviously, the jammer is installed in a car. This is evident from the smoothly increasing and decreasing power. In fact, 97% of all the jammers we have detected are installed in cars.
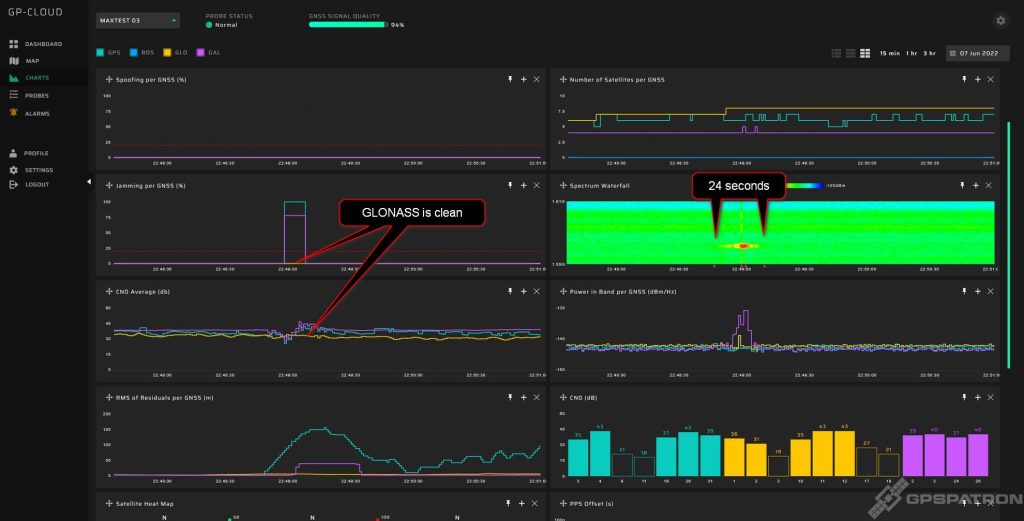
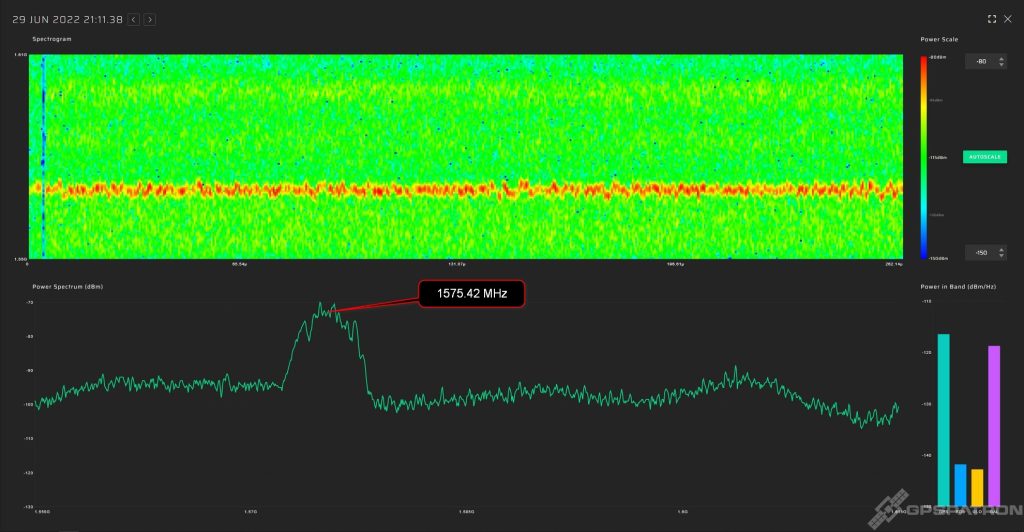
Note that GLONASS is suppressed even better than GPS and Galileo. You rarely see that. In most cases, GLONASS does not suffer so much, because the RF spectrum of most jammers is shifted towards GPS L1 1575.42 MHz.
Here is another example of a spectrogram of such a jammer:
Average Quality Jammers
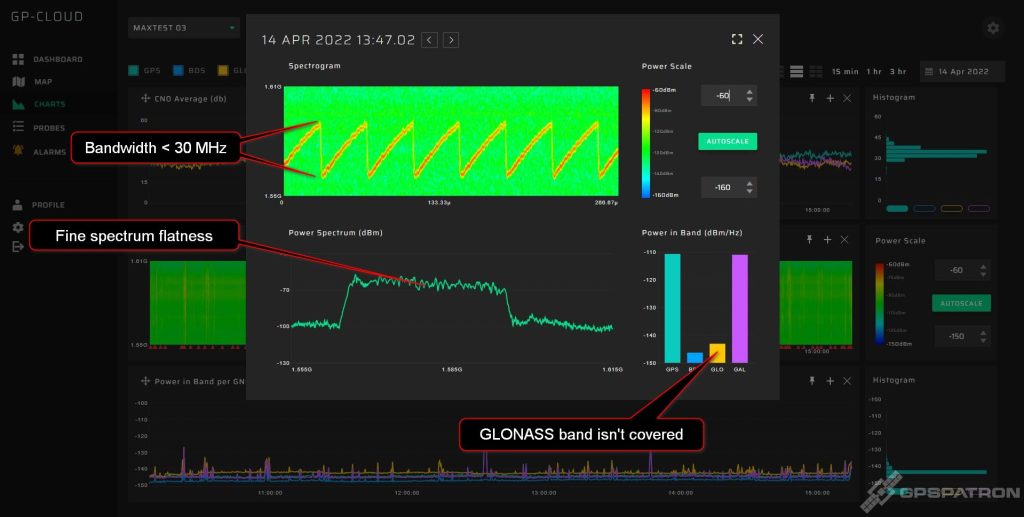
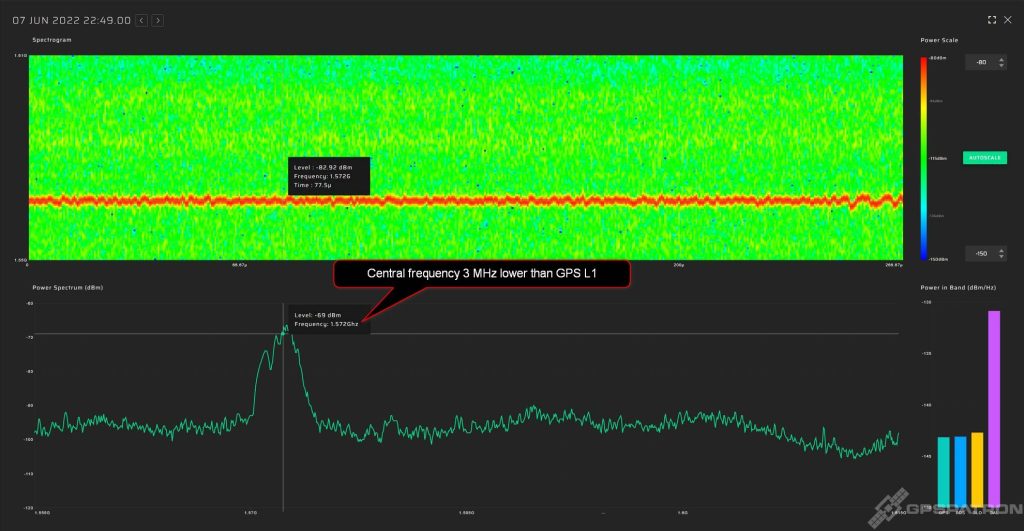
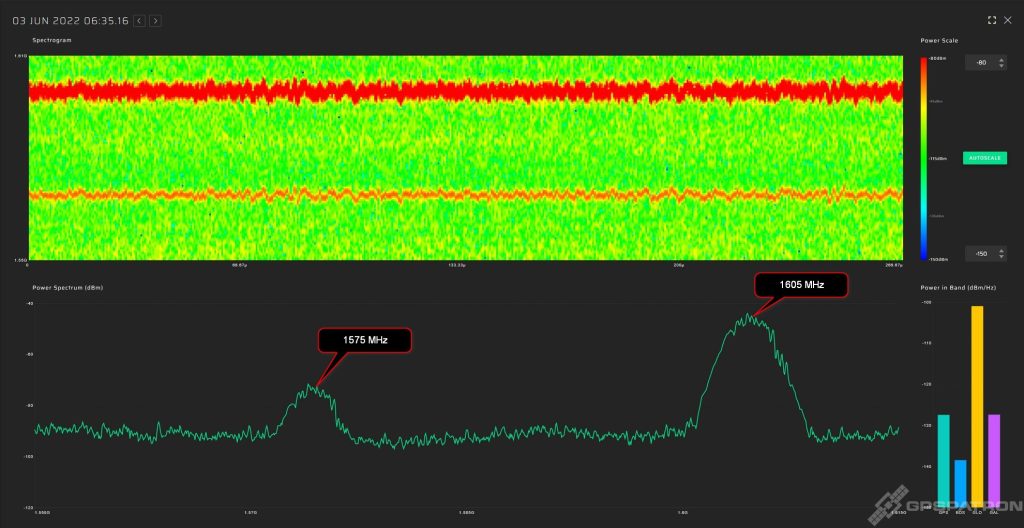
Here we have collected medium-quality devices. We classified them this way because of the narrower frequency bandwidth. Nevertheless, the center frequency is not badly calibrated and in-band spectrum flatness is good. Such jammers usually do not block the reception of GLONASS signals.
Example of a signal with a more accurately adjusted center frequency:
Worst-Performing Jammers
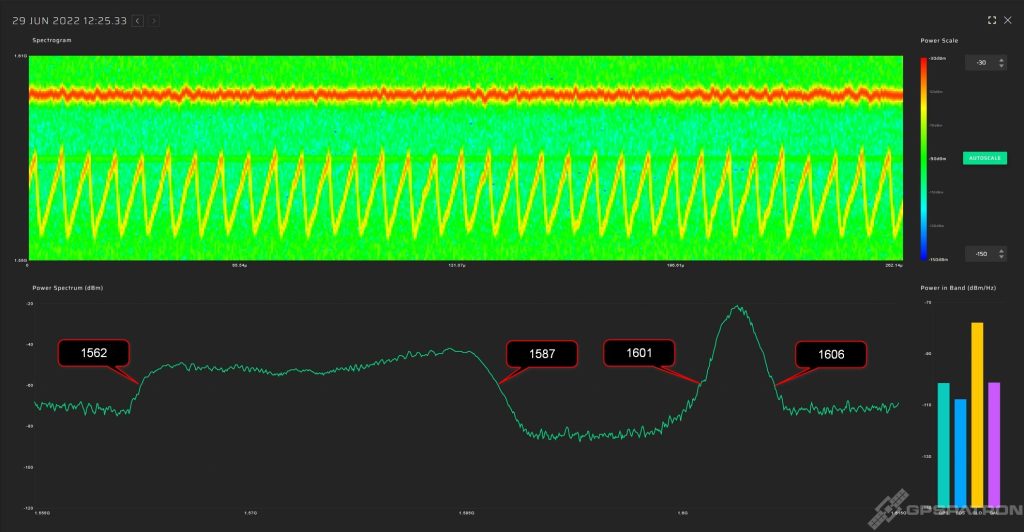
This section holds jammers with a purely sinusoidal signal, and simple pulse modulation.
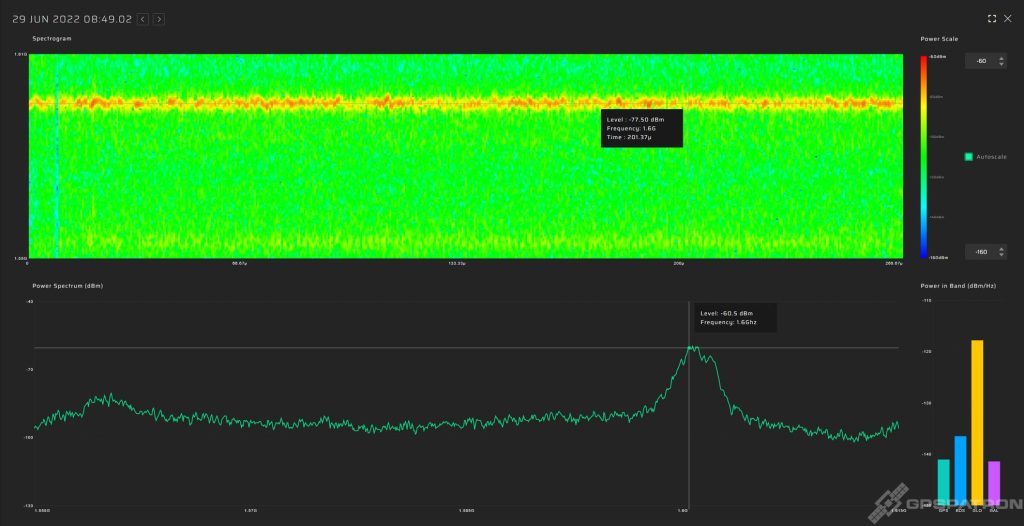
The spectrum looks like this:
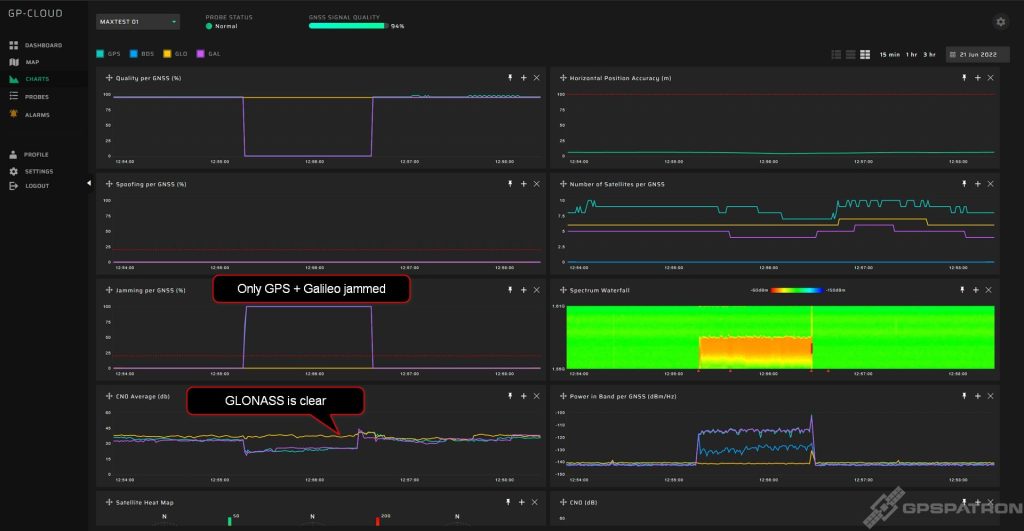
Such jammers suppress only the GPS and Galileo. We caught this signal from a fast moving car:
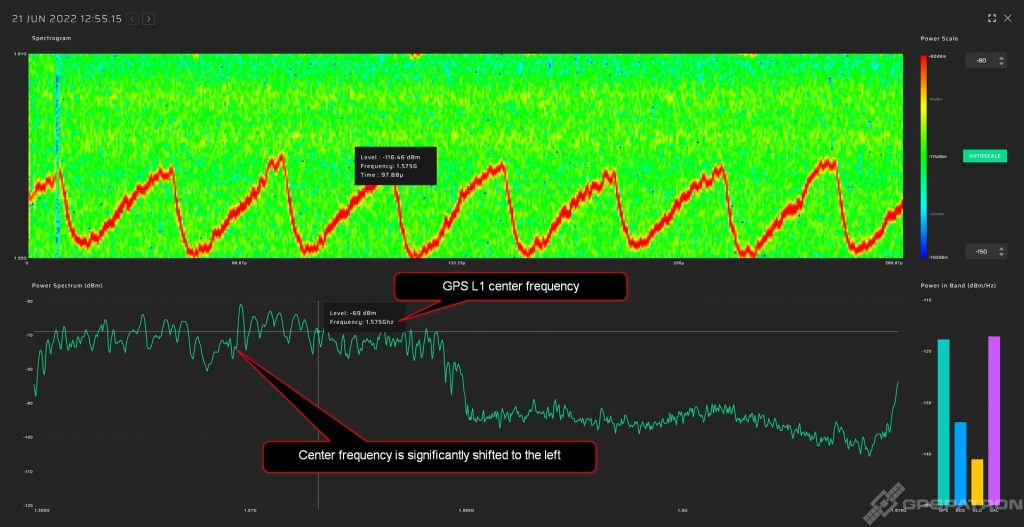
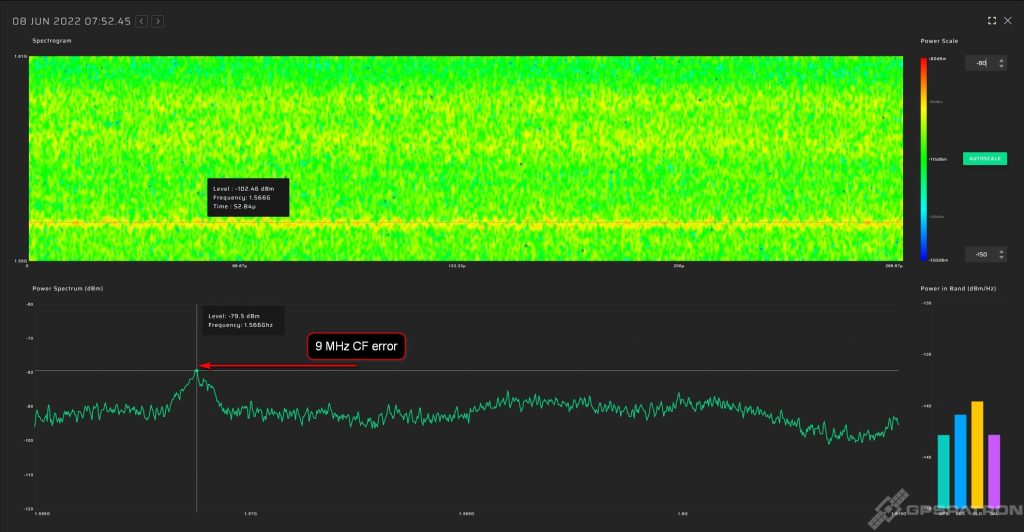
Here is an example of a jammer with a large frequency error:
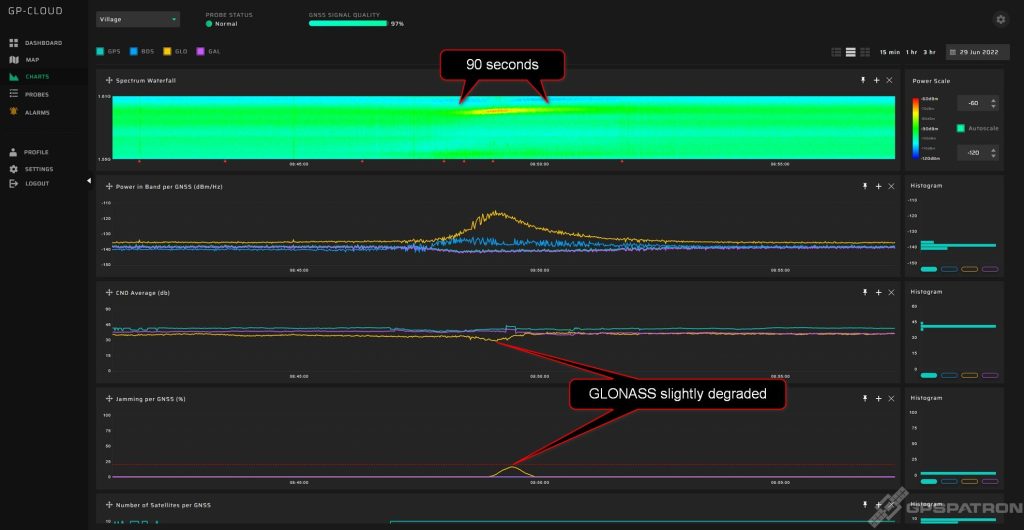
The 90-second interval of sine wave interference with 1600 MHz center frequency. Only the GLONASS was affected:
Long-Term Jamming Incidents
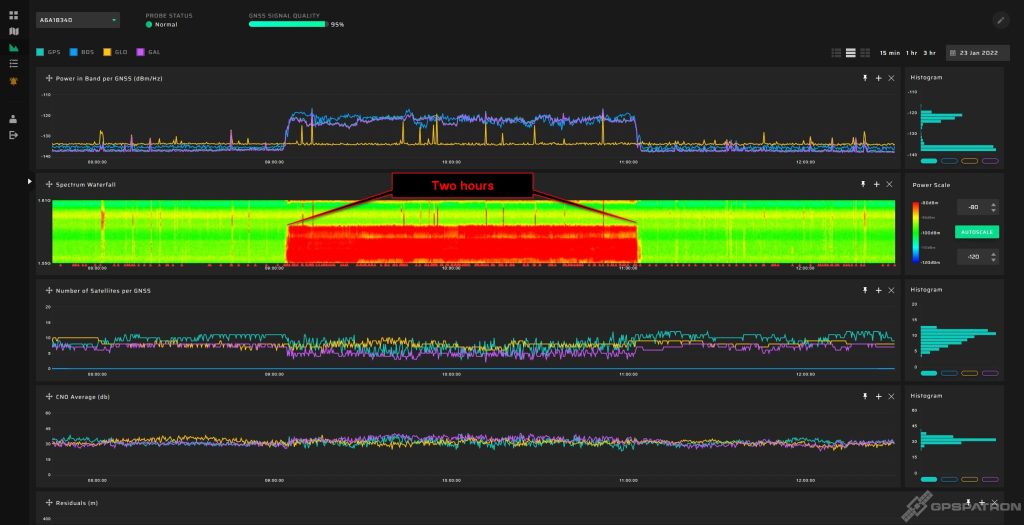
Most jamming incidents are very short. Cars arrive and leave quickly. However, this is not the case if you have a GNSS receiver located near a commercial vehicle parking area. This two-hour long incident we detected not far from a store. The driver did not turn off the jammer while unloading goods.
Learn more here about in-car jammers: https://gpspatron.com/in-car-jammers-are-killing-gnss-integrity/
Military Grade Jamming
Here we have compiled a collection of interference that we believe was generated by government authorities, rather than private players.
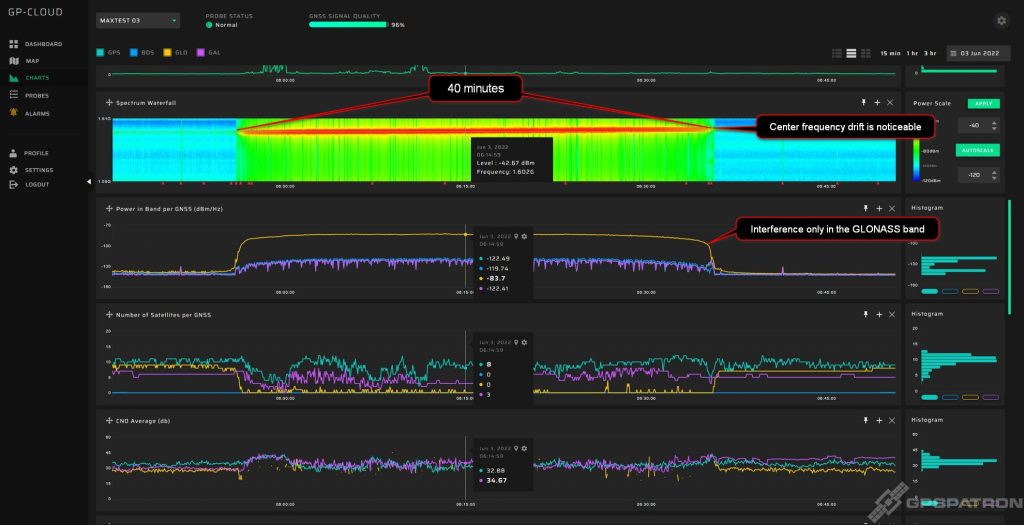
An example of GLONASS signal suppression. The equipment is not of high quality, as a significant drift of the central frequency over time is clearly visible.
The signal is quite wideband. Some kind of spread spectrum modulation is obviously applied.
Here is an example of a combination of GLONASS and GPS interference:
Wideband interference in the GLONASS band and a frequency-modulated signal in the GPS L1 band.
GNSS Spoofing
We encounter GNSS spoofing all over the world with different attack scenarios intended for different missions.
GNSS Spoofer in Anti-Drone Systems
This is the most common application of GNSS spoofing. The anti-drone system simulates the coordinates of the nearest airport. The commercial drone is either landing or trying to fly to the takeoff point.
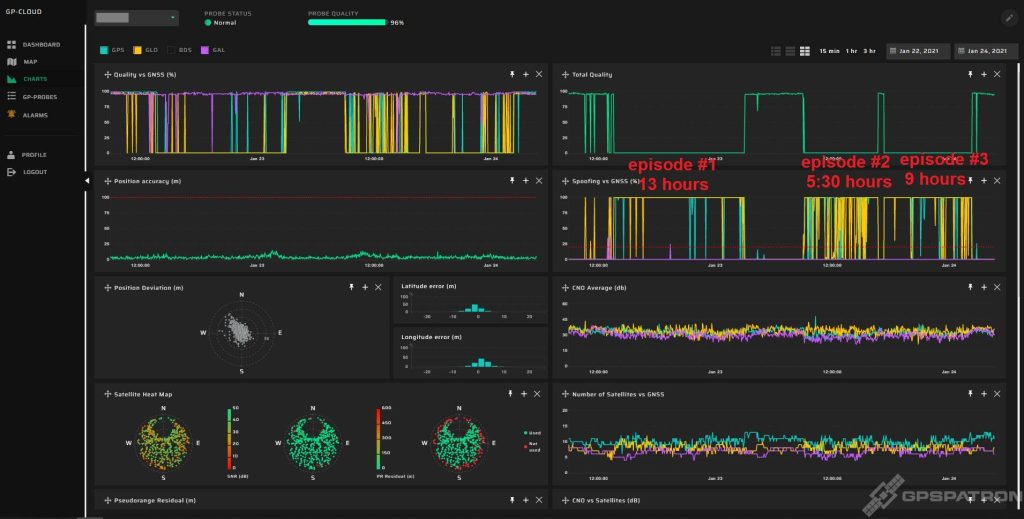
There are different usage scenarios here. Sometimes only GPS is spoofed, and the other constellations are blocked. Sometimes GLONASS + GPS are spoofed.
There are also different scenarios in terms of the duration of use. Automatic systems generate a fake signal within minutes. Sometimes a spoofer is activated for many hours.
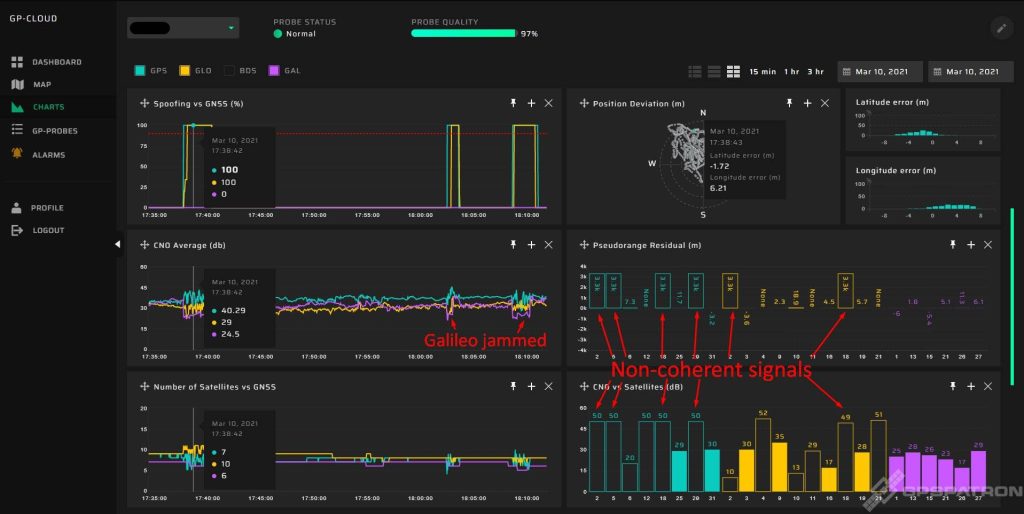
Non-coherent Spoofing
During a non-coherent or otherwise asynchronous spoofing, the GNSS signal is generated with false coordinates, time, and other parameters. If the receiver already acquires real signals, a non-coherent signal is perceived as noise. Therefore, for a successful attack, it is necessary to force a receiver to lose track of the real signals. This can be done in a number of ways. You can learn more about attack scenarios here:
https://gpspatron.com/async-spoofing-attacks/
https://gpspatron.com/spoofing-attacks-chapter-2/
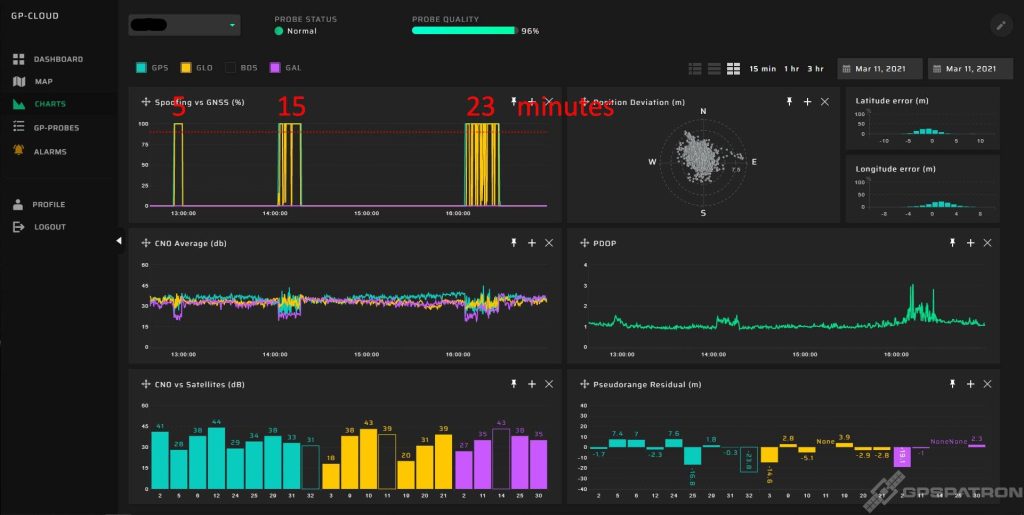
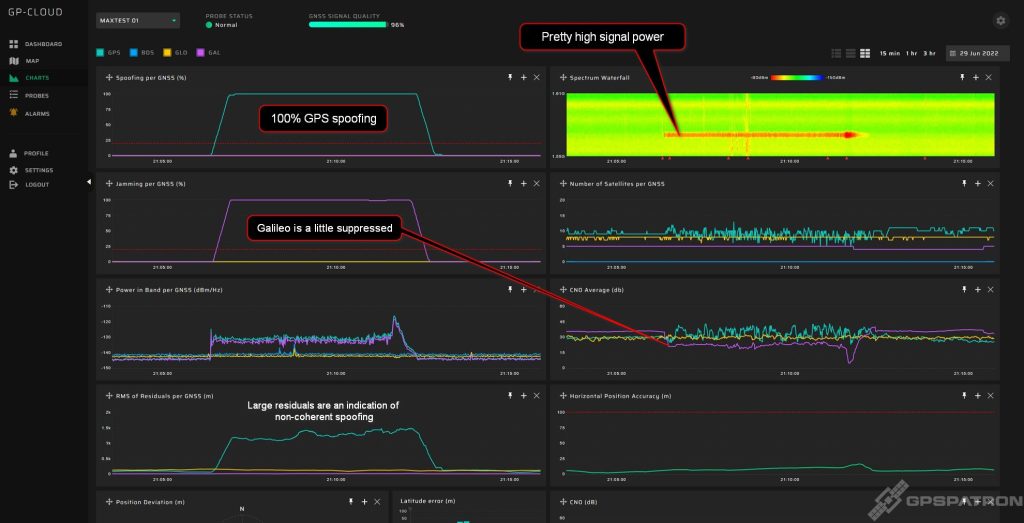
Here below you see an incident that lasted a few minutes. Our system detected GPS spoofing with 100% probability. The interference power was quite high, 15 dB higher than the system’s noise level. The signal is clearly visible on the spectral waterfall. Since the center frequency of GPS L1 and Galileo L1 coincide, the reception of Galileo signals slightly suffered.
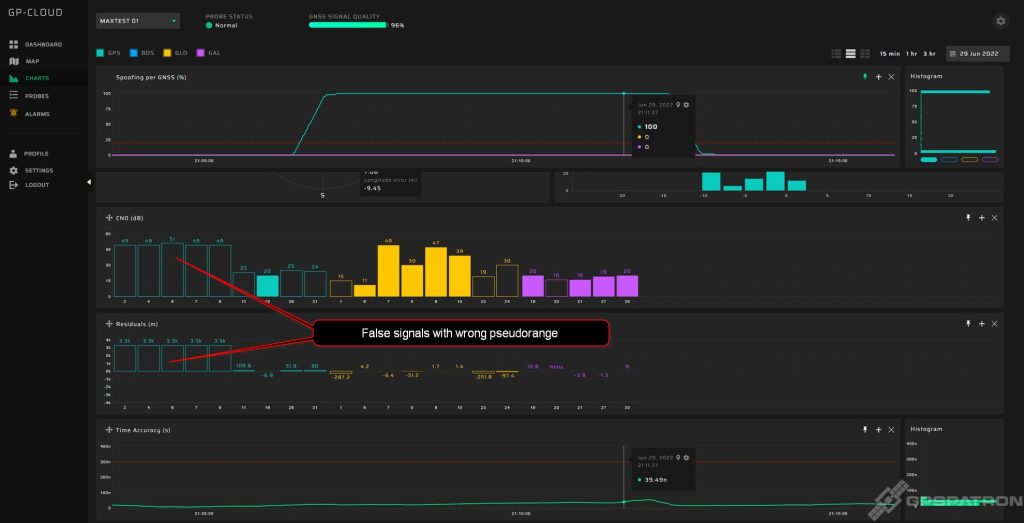
A distinctive sign of a non-coherent attack is the presence of signals with a huge residual and high SNR:
Signal spectrogram:
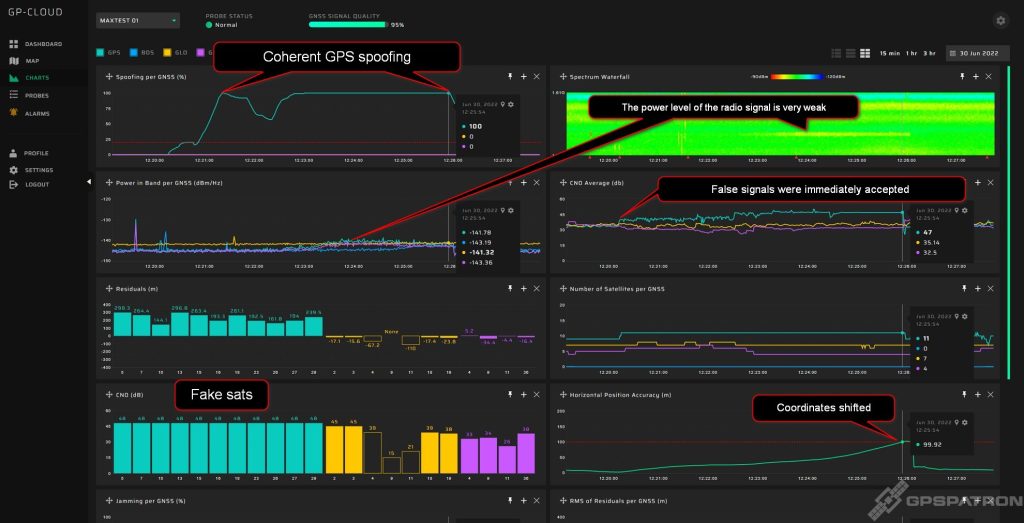
Сoherent Spoofing
Coherent spoofing is always intentional! The attacker needs to know the coordinates of your GNSS antenna precisely enough to simulate a signal completely identical in all parameters to the real one. Watch the video at the link to learn more about coherent attack:
https://gpspatron.com/types-of-gnss-spoofing-explainer-video/
Below you see an example of intentional coherent spoofing that our system detected. Spoofing started with a low power signal, which gradually increased until the signals of real GPS satellites were completely overlapped. Then an attempt to shift the coordinates.