In Chapter 1 of our “Types of GPS Spoofing Attacks” article series, we provided empirical and theoretical arguments on why GNSS spoofing is becoming an insistent problem for all types of time-dependent entities and infrastructures. We also described potential methods of execution, as well as the prevention of asynchronous spoofing attacks. Chapter 2 of the series is intended to look into synchronous spoofing attacks, their methods of implementation and available prevention solutions.
Please NOTE that the arguments provided, described and discussed in this article are applicable mainly to stationary time servers.
Before proceeding to the description of synchronous attacks, we would like to clarify the difference between synchronous and asynchronous attacks. In an asynchronous attack, the spoofer generates a signal that differs from the original in a variety of parameters: simulated coordinates, time, almanac and ephemeris, the power of satellites’ signals, etc. Moreover, the most important aspect is that during an asynchronous attack the fake signal does not get into the receiver’s correlation analysis window. Thus, it implies that at the first stage, the receiver perceives the fake signal as noise.
To execute a successful attack, a powerful enough signal has to be generated to overwhelm the genuine satellite signals. The suppression is possible due to the limited dynamic range of the receiver. When the fake signal becomes large enough, the correlation peak of the legitimate signal is concealed under its noises.
To sum up, simulating the coordinates and time difference from the prototype does not imply the dissimilarity between asynchronous and synchronous attacks. The main variance is that in the case of the asynchronous spoofing the fake signal does not get into the receiver’s correlation analysis window.
Synchronous Spoofing Attacks
Synchronous spoofing attacks pose a significant threat for time-dependent entities and infrastructures due to their stealth and ability to apply smooth and gradual time shifts.
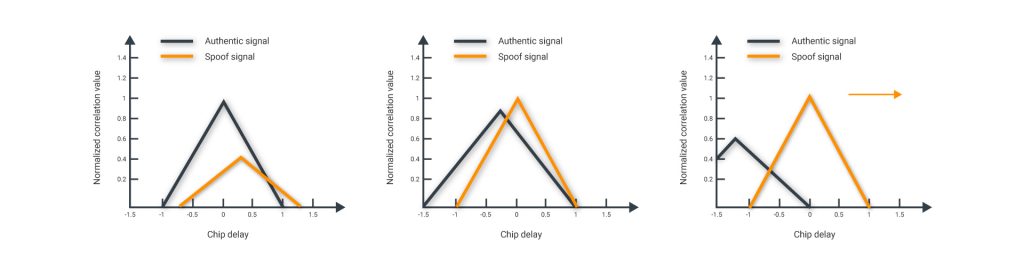
Synchronous spoofers imply a smooth-take-over or a soft-take-over by means of generating a signal identical to the authentic one in terms of time, coordinates (pseudo-range) and Doppler shift (where the correlation peak of the spoofed signal is within the tracking window of the receiver). Therefore, when the power of the spoofing signal is higher than the original, by design, the GNSS receiver locks onto the spoofing signal [2][3]. Thus, the GNSS receiver identifies the synchronous signal as genuine. In this case, the receiver produces the same time, coordinates, as well as the PPS signal.
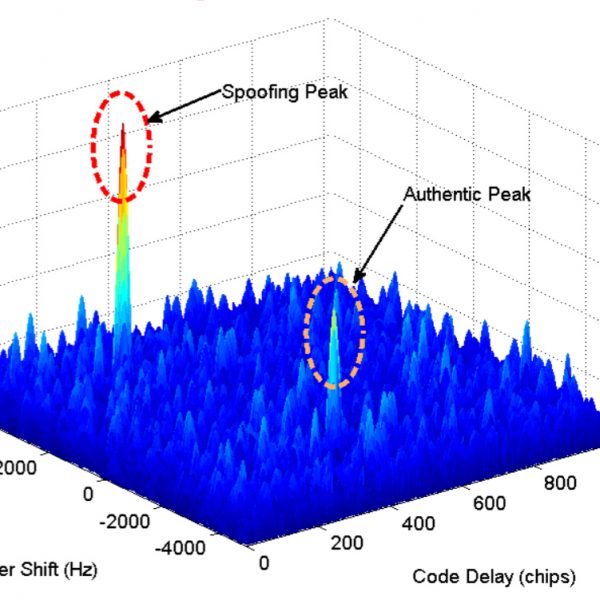
The chart above displays the stages of a synchronous attack. At the first stage, it generates a signal that falls into the correlation analysis window. Then, the signal power is elevated. To capture the correlation loop, the power of the counterfeit signal needs to be at least 4 dB higher than the prototype. At the third stage, the pseudo-range of each satellite is diverted to change the coordinates or time.
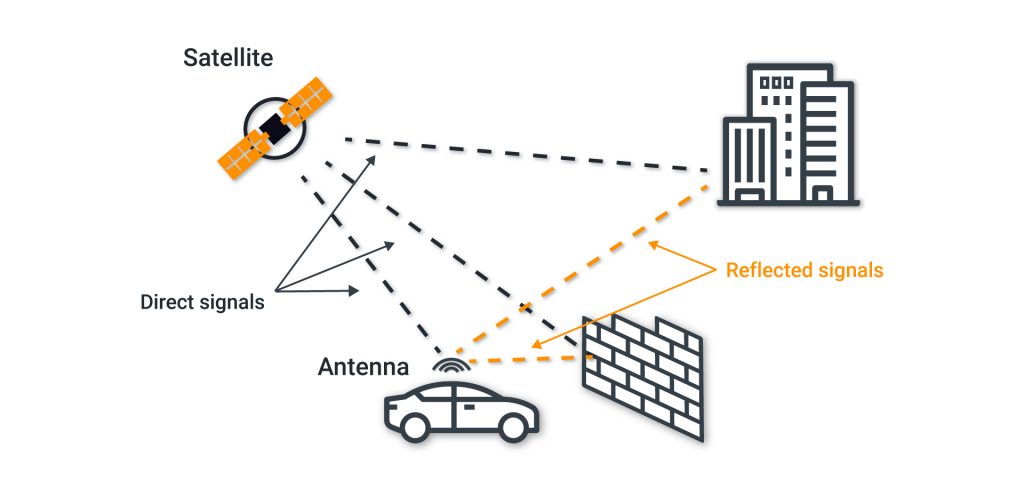
The presence of several correlation peaks can be explained by signals- some that are reflected from buildings- as well as spoofing.
Reflection of the signals may introduce surplus errors into the pseudo-ranges. For example, an additional 500 meters would denote an error of 1.6 us in determining the time.
In cities with many tall buildings, it is challenging for a receiver to tackle the multipass conditions. Since the forged signal and the reflected one look identical on the correlator, then, in our opinion, all research dedicated to analyzing the form of the correlation response [3] for detecting spoofing is not encouraging. In particular, considering such an analysis upsurges the cost of expanding the number of correlators in the utilized hardware.
Methods of Implementation/Execution
To carry out a synchronous spoofing attack, the spoofer requires the following information: receiver’s location, time synchronization, current almanac and ephemeris, and relative satellite’s signal power.
Strengths
- The same cheap hardware as in the case of an asynchronous attack can be used, with a single addition of the navigation module to collect current data from satellites;
- It is not possible to detect spoofing using the parameters drift monitoring. This is due to the fact that the generated signal fully corresponds in all parameters to the current signal, including the power;
- It is possible to apply a smooth shift of coordinates or time, which is very dangerous for time servers;
- The values of the satellites ephemeris can be replaced, which will allow the introduction of a controllable error in calculating the coordinates and time;
- The behavior of the receiver under a synchronous spoofing attack corresponds to the behavior when working in multipath conditions.
Weaknesses
- High accuracy of signal synchronization is necessary (around 500 ns);
- The coordinates of the victim’s phase center antenna must be calculated with accuracy;
- No open-source projects with similar functionalities are available.
Detection Algorithms/Methods
All methods from Chapter 1 are suitable for detecting synchronous spoofing attacks, except for the first – “Parameters Drift Monitoring.”
Let’s discover the reasons why in more detail. The list of parameters that can be monitored for detecting spoofing [5] [6] [7] [8] [9]:
- AGC Monitoring, Absolute Power Monitoring, and other methods based on estimating the signal power. A spoofing countermeasure method based on monitoring the receiver’s AGC gain level or absolute power. That is because the presence of spoofing signals increases the power content of the received signal set and this changes the AGC level, perhaps modifying it to an abnormal value. Pursuant to the analyses provided by [10], AGC monitoring is a powerful measure for detecting the presence of spoofing signals especially if their power level is greater than the authentic.
Cons
Since there is no need to generate high power in synchronous spoofing, this method will not work. It is not difficult to calculate the necessary power of the spoofer signal in the phase center of the victim’s antenna, taking into account the distance and sidelobe level of the receiving antenna.
- C/N0 Monitoring. Most GPS receivers employ C/N0 measurements as a parameter that characterizes the received signal quality. In open sky conditions, only satellite movement and ionosphere variations can cause gradual, smooth changes in the received signal power. However, when a higher power spoofer misleads a GPS receiver, the received C/N0 may experience a sudden change that can indicate the presence of a spoofing signal. The anti-spoofing receiver can monitor the C/N0 and track unusual variations that can be a sign of a spoofing attack.
Cons
With asynchronous spoofing, it is possible to measure C/N0 for each satellite and generate the same signal.
- Coordinates monitoring for stationary receivers. Altered coordinates of a stationary receiver indicate the presence of spoofing. In this case, a simple method can be applied. If the current coordinates from the navigation module are outside the set limit, then you are being spoofed. Albeit, due to various effects [4] in the ionosphere, the precision of determining the coordinates can be diminished. A larger threshold will have to be set.
Cons
A synchronous spoofer is capable of generating the same coordinates while distorting time.
- PPS monitoring with time server. This is the most compromise-based method for timeservers. Each server has a built-in reference signal generator of good quality that is capable of implementing the correct method for detecting spoofing by comparing the internal time and the time determined by the navigation module. A severe jump can point to the presence of spoofing.
Cons
A synchronous spoofer can shift the time with little effort, for example, 500 ns in 1 hour.
For amateurs to GNSS spoofing field, we recommend reading a master’s thesis of Leonardo Chiarello from Università degli Studi di Padova: “Security Evaluation of GNSS Signal Quality Monitoring Techniques against Optimal Spoofing Attacks.” [5] This work elaborates on attack types and their detection methods in a user-friendly language.
References
- Ali Broumandan, Ali Jafarnia Jahromi, Saeed Daneshmand, Gérard Lachapelle. GNSS Vulnerability to Spoofing Threats and a Review of Anti-Spoofing Techniques
- Shafiee, E & Mosavi, M & Moazedi, Maryam. (2017). Detection of Spoofing Attack using Machine Learning based on Multi-Layer Neural Network in Single-Frequency GPS Receivers. Journal of Navigation. 71. 1-20. 10.1017/S0373463317000558
- M. R. Mosavi, Z. Nasrpooya and M. Moazedi. Advanced Anti-Spoofing Methods in Tracking Loop
- Glenn MacGougan, Gerard Lachapelle, Rakesh Nayak. OVERVIEW OF GNSS SIGNAL DEGRADATION PHENOMENA
- Leonardo Chiarello. Security Evaluation of GNSS Signal Quality Monitoring Techniques against Optimal Spoofing Attacks
- Esteban Garbin Manfredini – Politecnico di Torino and Colorado University at Boulder; Dennis M. Akos – Colorado University at Boulder; Fabio Dovis – Politecnico di TorinoOptimized. GNSS spoofing detection using commercial receivers Field Data and Experimental Trials. Presentation
- Van der Merwe, Johannes & Zubizarreta, Xabier & Lukcin, Ivana & Rügamer, Alexander & Felber, Wolfgang. (2018). Classification of Spoofing Attack Types. 10.1109/EURONAV.2018.8433227
- Broumandan A., Jafarnia-Jahromi A., Daneshmand S., Lachapelle G. Effect of Tracking Parameters on GNSS Receiver Vulnerability to Spoofing Attack; Proceedings of the 29th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2016); Portland, OR, USA. 12–16 September 2016
- Dehghanian V., Nielsen J., Lachapelle G. GNSS spoofing detection based on signal power measurements: Statistical analysis. Int. J. Navig. Obs. 2012;7:1–8. doi: 10.1155/2012/313527
- D. M. Akos, “Who’s afraid of the spoofer? gps/gnss spoofing detection via automatic gain control (agc)”, Navigation, vol. 59, no. 4, pp. 281–290, 2012.