This article is an overview of available publications on the vulnerability of power grids to spoofing attacks.
It is in accordance with the “GALILEO for TIMING and SYNCHRONISATION APPLICATIONS” article:
In the future, grid systems will require sub-microsecond level accuracy at power substations to implement automatic network management and protection relay functions, and to support fault detection and performance measurements. Today grid systems rely on GNSS clocks as time reference sources and atomic clocks as a backup in case of outages. GNSS receivers are low-cost, reliable, high-precision timing sources that can be implemented in a large number of intelligent grid sensors (i.e. Phasor Measurement Units), to enable real-time automatic control of the grid. The rapid detection of intentional and unintentional time anomalies was identified by several utilities as a key near-term requirement. Due to the criticality of the power system and the likelihood of future smart grid reliance on high-precision timing, resilience of the GNSS signals to interference, and increasingly to jamming and spoofing, is crucial.
1. “Going Up Against Time: The Power Grid’s Vulnerability to GPS Spoofing Attacks” by Daniel P. Shepard, Todd E. Humphreys, and Aaron A. Fansler, 2012.
The first research on the vulnerability of power grids to spoofing attacks were conducted by Daniel P. Shepard, Todd E. Humphreys, and Aaron A. Fansler in 2012. The article “Going Up Against Time: The Power Grid’s Vulnerability to GPS Spoofing Attacks” provides an example of a successful trial of a spoofing attack on phasor measurement units (PMU).
Two experiments were conducted: “Cable-only” and “Over-the-air” spoofing attacks. The used spoofer was an advanced version of the spoofer reported in “Assessing the Spoofing Threat,” GPS World, January 2009.
Authors came to the conclusion that both cable-only and the over-the-air spoofing attacks can be realized by means of a civil-grade and easily accessible spoofer that can compromise the PMU phase measurements. The spoofer is capable of introducing a time offset in the time reference receiver, which provides the timing signal for a phasor measurement unit without physical access to the corresponding receiver. Thus, the phase offset can be produced in the synchrophasor data coming from the phasor measurement unit. In the tests, it was validated that a phasor measurement unit can violate the IEEE C37.118 Standard for synchrophasors within 11 minutes from the outset of a spoofing attack. As a result, civil spoofers are capable of causing control schemes to falsely trip generators, which can potentially lead to corresponding power faults and blackouts.
Image # 3 illustrates a plot of the phase angle difference between the reference and the spoofed PMUs:
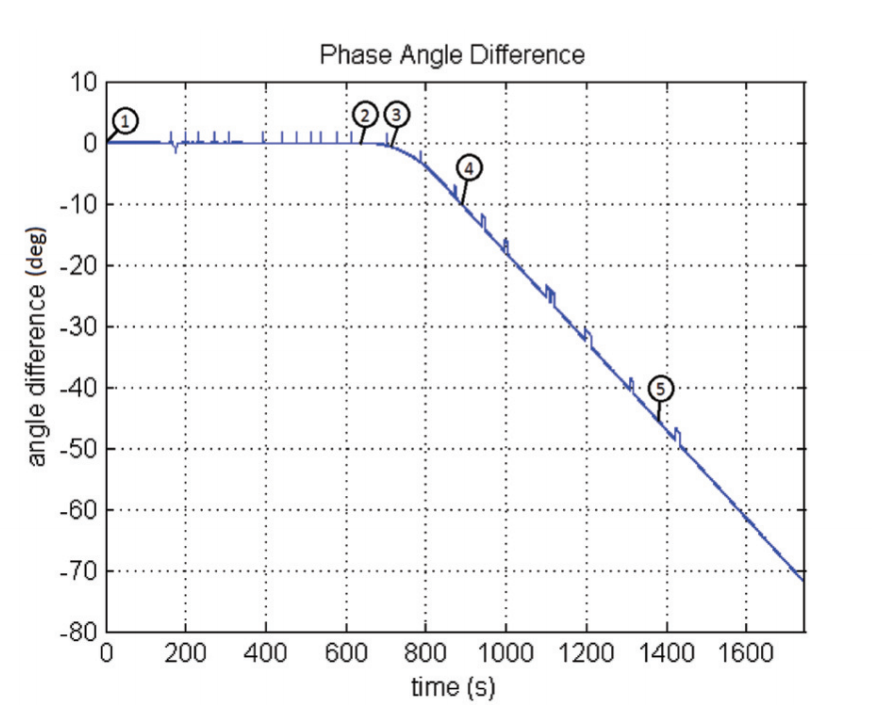
Generally, the phase angle difference would be almost zero in the absence of a spoofing attack. Point 1 marks the start of the test. Point 2 marks the point at which the spoofer has completely captured the victim’s receiver. Point 3 demonstrates the IEEE C37.118 Standard has been broken. Point 4 indicates where the spoofer-induced velocity has reached its maximum value for the test. Point 5 establishes when the spoofed signal was removed.
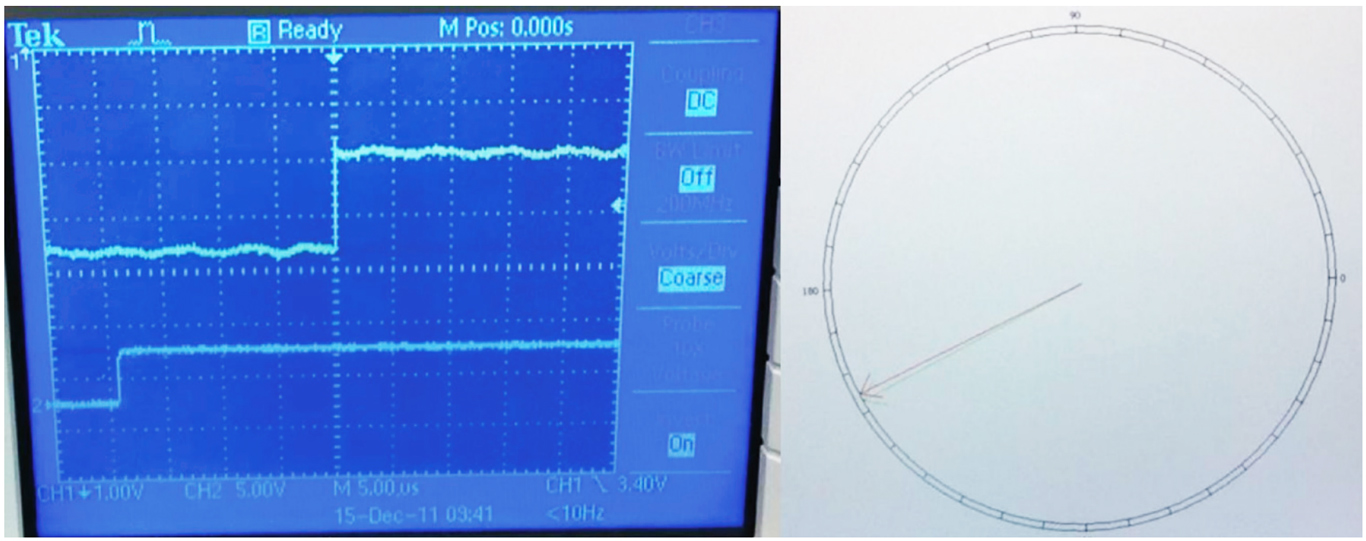
The authors explain the offset of the PPS and phase shift that happened during the attack in image #6.
In the article, the authors also describe the consequences of a successful spoofing attack on the example of Chicoasen-Angostura transmission link in Mexico.
This transmission line links together large hydroelectric generators in Agostura to large loads in Chicoasen through two 400-kV transmission lines and one 115-kV transmission line. If a fault occurs in which both of the 400-kV lines are lost, then the hydroelectric generators may experience angular instability. In order to prevent this, a PMU was set up at each end of the transmission lines with a direct communications link between them.
PMU could be spoofed, which can cause cascading faults across the corresponding grid.
We also recommend watching a video of the experiment conducted by Daniel Shepard and Todd Humphreys:
They demonstrate a spoofing attack against a phasor measurement unit designed to synchronize the power grid.
2. Time Synchronization in the Electric Power System NASPI Technical Report
In May of 2017, a group of authors published a 54-page report “Time Synchronization in the Electric Power System”. Thetestimony , provides substantial arguments on the importance of high-quality requirements to the measurement of synchronization precision and how to obtain it.
In the preface, the authors describe the Synchrophasor technology that requires precise timing:
Synchrophasor technology is being used for wide-area monitoring and situational awareness, verification of grid models, event analysis, and for analysis of a variety of grid phenomena. Because the effective operation of synchrophasor technology requires highly precise, fully reliable, and secure monitoring, timing, and communications systems, it embodies the timing and synchronization challenges involved for successful deployment and coordination of the distributed networks in the Smart Grid and Internet of Things.
Within five years, synchrophasor technology could become mission-critical for bulk power system operation and be at the early stages of use at the electric distribution level.
The authors show some key power system timing uses in relative terms:
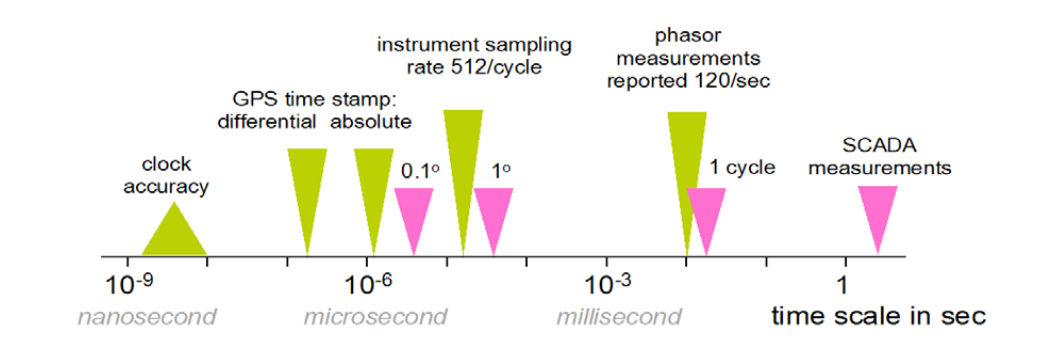
Image source: “Time Synchronization in the Electric Power System NASPI Technical Report”
PMUs do high-speed grid monitoring, time-synchronized to UTC with microsecond accuracy, and are used mostly at the transmission level. They now sample at 30 to 120 samples/sec; timing must be accurate within 1 μs. When timing delivery mechanisms become more reliable, synchrophasor technology can become a mission-critical tool.
Timing errors from the time source – or between the time source and the point of time- stamping – can create incorrect synchrophasor data, and lead to missing data and/or the failure to create data frames. The failure to deliver data to concentrators and applications within acceptable latency periods causes data gaps that could obscure early warning information about dynamic grid conditions. Timing errors can create false analytical conclusions, and in the future could drive undesirable and possibly dangerous automated grid operations with synchrophasor-based controls.
Taking into account the importance of PMU synchronization precision, the authors describe numerous variants of alternative timing sources and options in chapter 5:
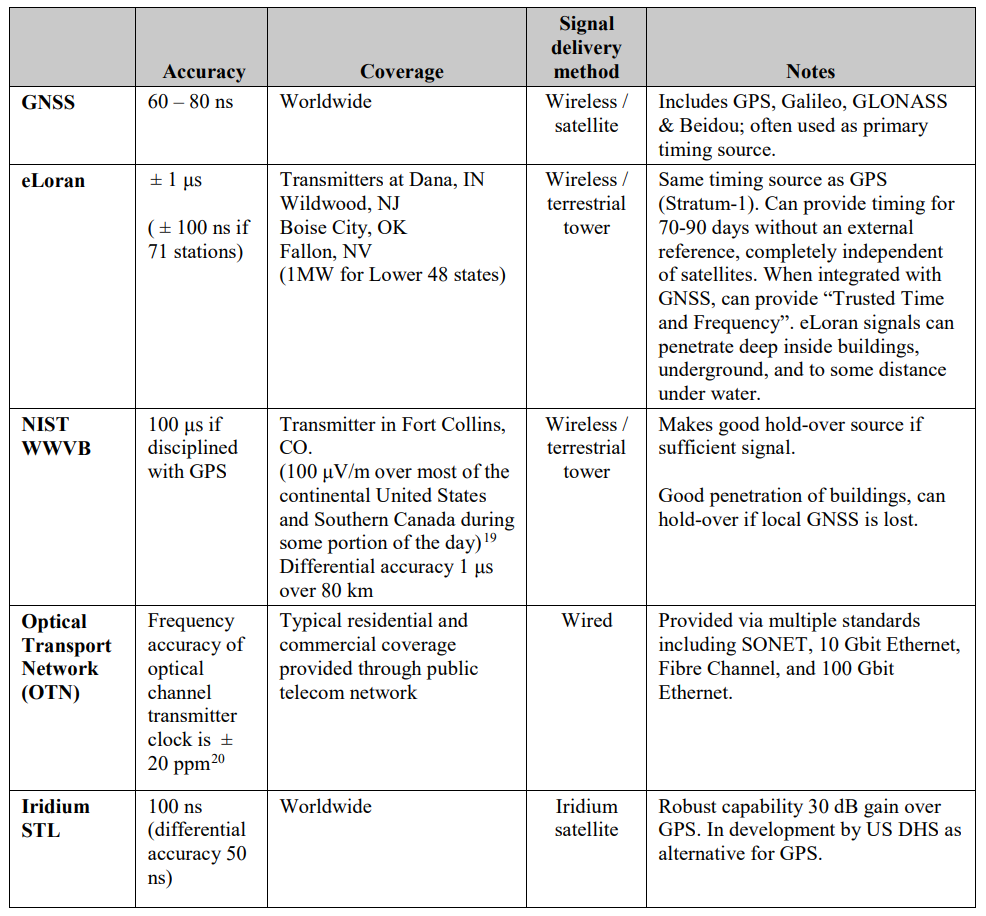
Evidently, only GNSS signals can ensure low-cost and precise synchronization.
In chapter 6, the authors describe Timing Problems, Anomaly Detection, and Mitigation. Examples of timing precision distortion of GPS systems are presented as follows:
• From space
– GPS signal-in-space anomalies
– Ionospheric fluctuations, including solar storms, sunspots
and geomagnetic disturbances
– Tropospheric issues
– Signal fading due to moisture
– Events – satellite constellation changes• On-site at the point of GNSS receiver installation and use
– GPS receiver – poor quality, software bugs, no firmware updates, bad location, local jamming or spoofing or other radio interference, lost wire to the PMU, no correction for PNT broadcast problems, leap second and leap year processing
– PMU – poor interoperability with GPS receiver, slow firmware patches, lost wire to GPS receiver, sloppy program for time-handling, no detection of timing problems, no back-up time source
– In substation timing delivery (rare) – problems with cabling or Ethernet distribution of time signal to slave clocks• PDCs and applications – inadequate detection of timing anomalies or gaps and computational errors resulting from those problems.
Paragraphs 6.2 and 6.3 are dedicated to GNSS Cyber-security issues:
DHS identifies three sets of threats to GNSS signals. As summarized in a 2012 presentation, those threats are:
• Unintentional
– Interference – includes out-of-band emissions from other radio sources or in-band emissions from other systems, such as … other satellite navigation systems• Intentional
– Jamming – the deliberate drowning out of legitimate Positioning, Navigation and Timing and Frequency (PNTF) signals using higher power signals to cause loss of satellite lock and to prevent reacquisition
– Spoofing – the deliberate emitting of legitimate-appearing false signals to shift the computed position or time of a victim’s receiver• Naturally occurring – Space Weather – variable conditions on the sun and the space environment that can influence the performance and reliability of space and ground-based systems.
A spoofing attack can introduce time error in a victim PMU, which in turn produces proportional phase angle error in the synchrophasor data originating from it. Such attacks can be easily accomplished by using Universal Software Radio Peripheral (USRP) devices, which are inexpensive and widely available. This type of attack is stealthy in nature, and most of the civilian GPS receivers available today lack any effective countermeasures.
In chapter 7, the authors provide general recommendations for improving the precision of synchronization measurements in power grids.
3. “Distributed Estimation of Power System Oscillation Modes Under Attacks on GPS Clocks” by Yongqiang Wang, João P. Hespanha
In their article “Distributed Estimation of Power System Oscillation Modes Under Attacks on GPS Clocks” published in ”IEEE Transactions on Instrumentation and Measurement” authors Yongqiang Wang; João P. Hespanha propose a distributed real-time wide-range oscillation estimation approach that is robust to GPS spoofing on PMUs and their associated phasor data concentrators.
Phasor Measurement Units (PMUs) are widely regarded as one of the most important measurement devices in a power system. By receiving highly accurate time information from the Global Positioning System (GPS), spatially distributed PMUs enable synchronized phasor measurements of voltages and currents from widely dispersed locations in power systems to monitor and control power system dynamics in real-time.
The authors review various attack scenarios on diverse power grid architectures. As an example, the authors analyze the performance of a distributed architecture for a 4-area power system network under a spoofing attack:
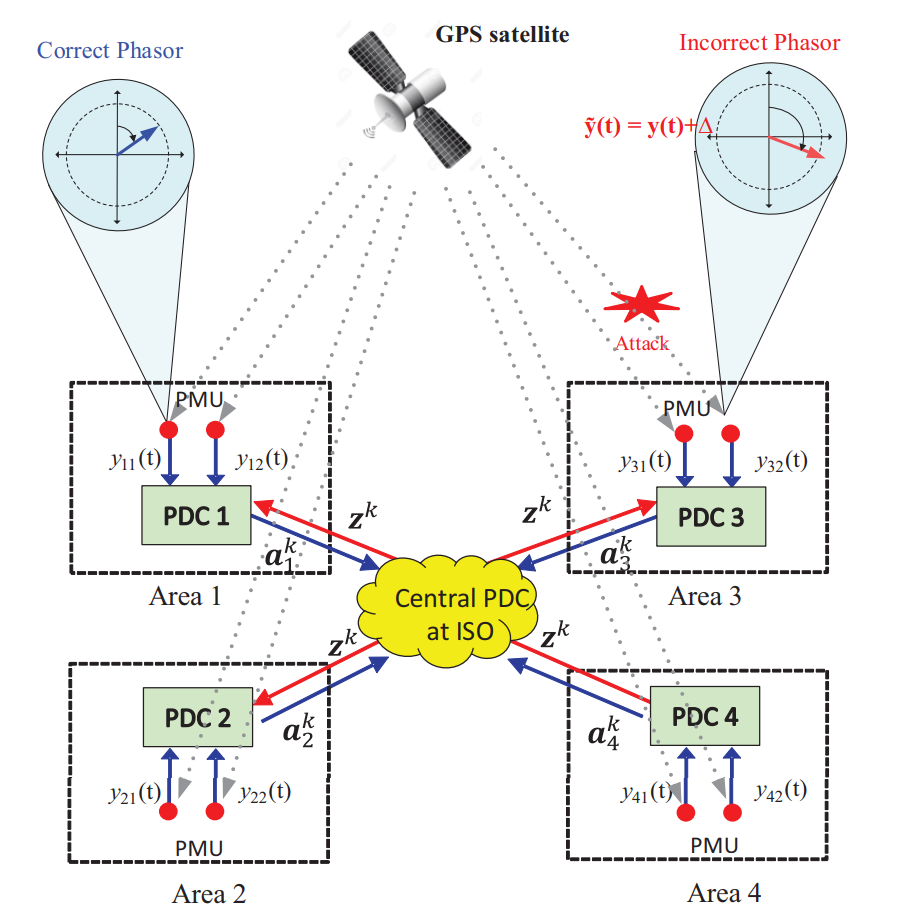
The authors propose a mathematical detection method of the attacked PMU, based on the analysis of the data from the entire network. If the algorithm shows that one of the PMUs provides suspicious measurements, then it is excluded from further system monitoring. The authors conducted a numerical simulation on the example of IEEE 68-bus system to verify the proposed approach.
However, the realistic application of the provided algorithms is ambiguous, due to the fact the authors conducted mathematical modeling with properly functioning network elements. Thus, it is not entirely clear what the developed algorithms will display under emergency circumstances.
4. “Vulnerability Analysis of Smart Grids to GPS Spoofing” by Paresh Risbud, Nikolaos Gatsis, Ahmad Taha
In the article, the authors build on the novel measurement model developed by P. Risbud, N. Gatsis, and A. Taha, in the paper “Assessing power system state estimation accuracy with GPS-spoofed PMU measurements” to formulate an optimization problem to identify the most vulnerable PMUs in the network.
GPS spoofing is caused by transmitters mimicking the GPS signal with the intention of altering the GPS time estimated by the PMU’s GPS receiver. These attacks maliciously introduce erroneous time stamps, thereby inducing a wrong phase angle in the PMU measurements.
The Electric Power Research Institute, in collaboration with the National Electric Sector Cybersecurity Organization Resource, has published a technical report recognizing the vulnerability of PMUs to GPS spoofing under its scenario WAMPAC.12: GPS Time Signal Compromise. This paper considers the effects of GPS spoofing attacks on power grids.
As in the above mentioned publication, the authors expect to detect the attacked PMU with “ordinary” mathematical data processing 🙂
5. “Vulnerability of Synchrophasor-based WAMPAC Applications’ to Time Synchronization Spoofing” by Dr. Luigi Vanfretti
We recommend a humoristic presentation of Dr. Luigi Vanfretti, which illustrates the vulnerability of power grids to various attack types:
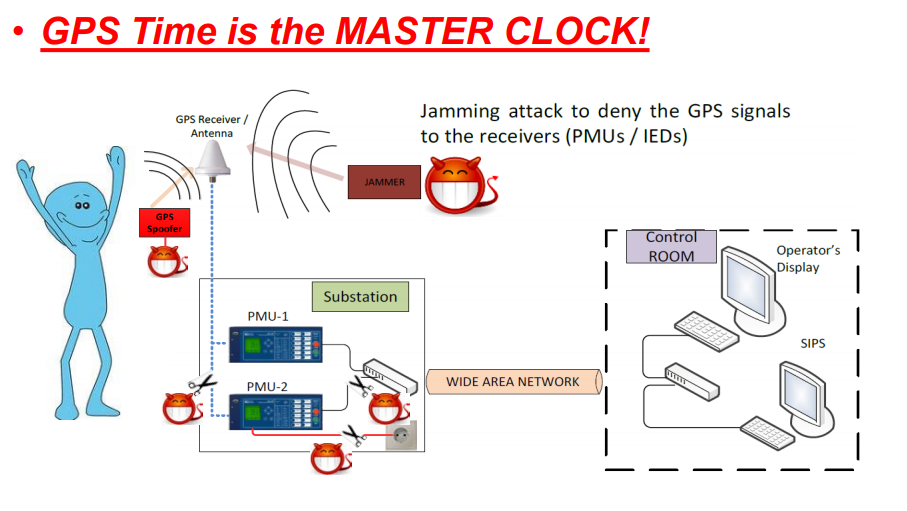
Loss/Spoofing of time-synchronization signal results in corrupted power system monitoring results, delayed/faulty protection activation, and degradation of WAPOD controls
If the provided materials are not sufficient for estimating the magnitude of the dangers that spoofing attacks pose for power grids, you can learn more from the following articles and publications:
- J. Liang, L. Sankar, and O. Kosut, “Vulnerability analysis and consequences of false data injection attack on power system state estimation,” IEEE Trans. Power Syst., vol. 31, no. 5, Sept. 2016.
- P. Gao, M. Wang, J. H. Chow, S. G. Ghiocel, B. Fardanesh, G. Stefopoulos, and M. P. Razanousky, “Identification of successive “unobservable” cyber data attacks in power systems through matrix decomposition,” IEEE Trans. Signal Process., vol. 64, no. 21, Nov. 2016.
- S. Kumar, M. Soni, and D. Jain, “Cyber security threats in synchrophasor system in WAMS,” Int. J. Comp. Appl., vol. 115, 2015.
- A. Jafarnia-Jahromi, A. Broumandan, J. Nielsen, and G. Lachapelle, “GPS vulnerability to spoofing threats and a review of antispoofing techniques,” Int. J. Navi. Obs., vol. 2012, 2012.
- D. Schmidt, K. Radke, S. Camtepe, E. Foo, and M. Ren, “A survey and analysis of the GNSS spoofing threat and countermeasures,” ACM Comput. Surv., vol. 48, no. 4, May 2016.
- X. Jiang, J. Zhang, B. J. Harding, J. J. Makela, and A. D. DominguezGarcia, “Spoofing GPS receiver clock offset of phasor measurement units,” IEEE Trans. Power Syst., vol. 28, Aug. 2013.
- Z. Zhang, S. Gong, A. D. Dimitrovski, and H. Li, “Time synchronization attack in smart grid: Impact and analysis,” IEEE Trans. Smart Grid, vol. 4, no. 1, Mar. 2013.
- P. Risbud, N. Gatsis, and A. Taha, “Assessing power system state estimation accuracy with GPS-spoofed PMU measurements,” in Proc. 7th IEEE Conf. Innovative Smart Grid Technologies, Minneapoils, MN, Sept. 2016.
- Y. Fan, Z. Zhang, M. Trinkle, A. D. Dimitrovski, J. B. Song, and H. Li, “A cross-layer defense mechanism against GPS spoofing attacks on PMUs in smart grids,” IEEE Trans. Smart Grid, vol. 6, no.6, Nov. 2015.
- A. Arvani and V. S. Rao, “Cyber security of smart grid systems using intrusion detection methods,” in Proc. Int. Conf. Computer Security and Digital Investigation, 2014.
- D.-Y. Yu, A. Ranganathan, T. Locher, S. Capkun, and D. Basin, “Short paper: Detection of GPS spoofing attacks in power grids,” in Proc. ACM Conf. Security and Privacy in Wireless & Mobile Networks, July 2014.
- X. Fan, L. Du, and D. Duan, “Synchrophasor data correction under GPS spoofing attack: A state estimation based approach,” IEEE Trans. Smart Grid
