There are tons of methods, mathematical models, and approaches to detect GNSS spoofing described in existing scientific articles/papers. Apparently, there are no fundamental barriers to reliable spoofing detection.
However, most studies focus on improving false-positive/false-negative rates and demonstrating the novelty and beauty of the proposed method. This article will confirm that spoofing detection latency is even more vital, especially for time server protection.
How much time do we really have?
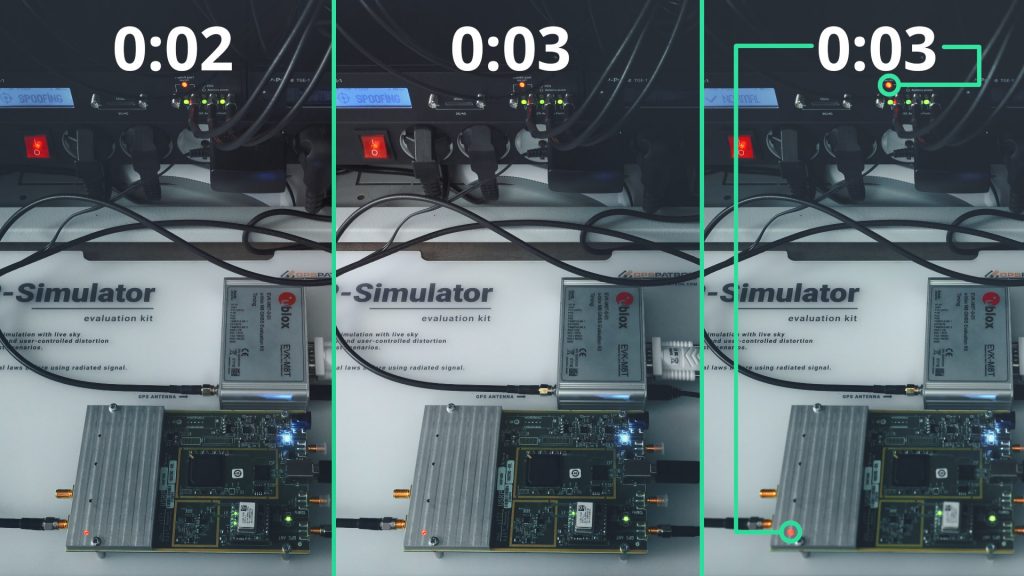
Here we will try to answer how quickly you should detect spoofing and respond to protect a time server. In this video, we showed how much time a GNSS receiver takes to move its clock under a non-coherent attack:
We had a target and reference GNSS receivers both connected to a GNSS antenna to receive genuine signals. A GPS spoofer was connected to the target receiver with an RF directional coupler.
We conducted a non-coherent scenario, which can be characterized with the following steps:
- spoofer generates fake signals with a significant power level, usually 30-50 dB higher than the original one
- target receiver loses signals and switches to non-fix mode
- receiver switches to search mode and finds signals with better signal strength
- receiver tracks fake signals and gathers data
- receiver provides time and positioning based on fake signals.
To know more about the different spoofing scenarios, check this video.
We made 20 attempts and measured the time between when the spoofer switches on and when the PPS signals shift. To understand when the PPS signals shift, we measured the PPS phase difference between the reference and target GNSS receivers with an oscilloscope.
Results table:
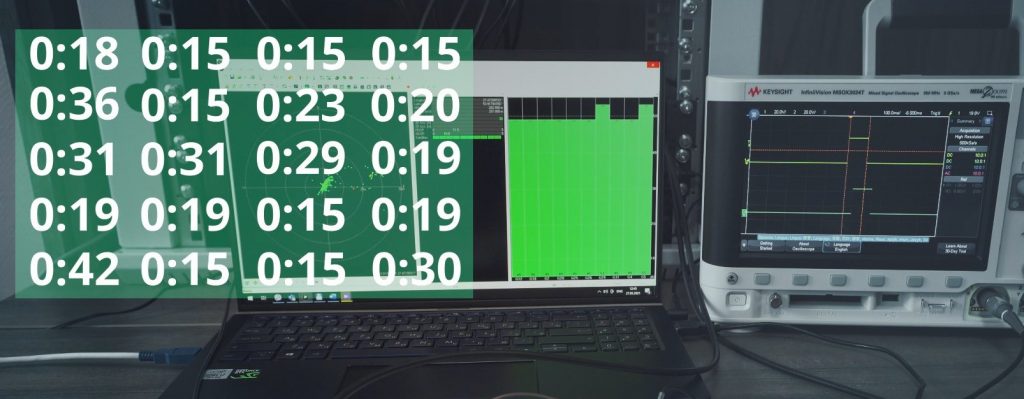
Here you see that in just 15 seconds after an attack begins, your GNSS receiver can shift the PPS phase or/and coordinates.
How quick GPSPATRON works
In the second part of the mentioned video, we demonstrated the performance of our solution live. We had a GP-Probe connected to three GNSS antennas on a roof and the GPS spoofer connected to a TX antenna on the same office roof. The probe measured the signal parameters of all visible satellites and sent raw GNSS data to the GP-Cloud every second. The GP-Cloud processed data stream, detected, and classified anomalies in spatial parameters of GNSS signals. Data analysis results were displayed on GP-Probe’s user interface:
We made some attempts and proved that our system detects spoofing in less than 3 seconds. It’s 100% enough to protect any time servers:
This particular probe was connected to the cloud deployed in Germany. We used a regular office network for internet connection. So, we did not try to improve system performance with unfair methods, thereby creating ideal lab conditions. Therefore, this is 100 percent true performance that our users enjoy. Obviously, with a self-hosted server and a dedicated link, the latency was even better.
Conclusion
Why do we care to highlight that spoofing detection time is crucial?
- We have observed numerous actual incidents in multiple locations where a customer’s time server has had its clock shifted in 15 seconds under the influence of non-coherent spoofing.
- We face customers who believe in simple spoofing detection algorithms like SNR/coordinates/time error monitoring. These methods can obviously detect spoofing only when the target receiver is already successfully attacked and produces incorrect data.
We have accumulated significant experience defending against GNSS spoofing in many “special” regions of the world. It is imperative to detect an attack as early as possible so you would have ample time to take protective measures, such as switching to a backup synchronization source.