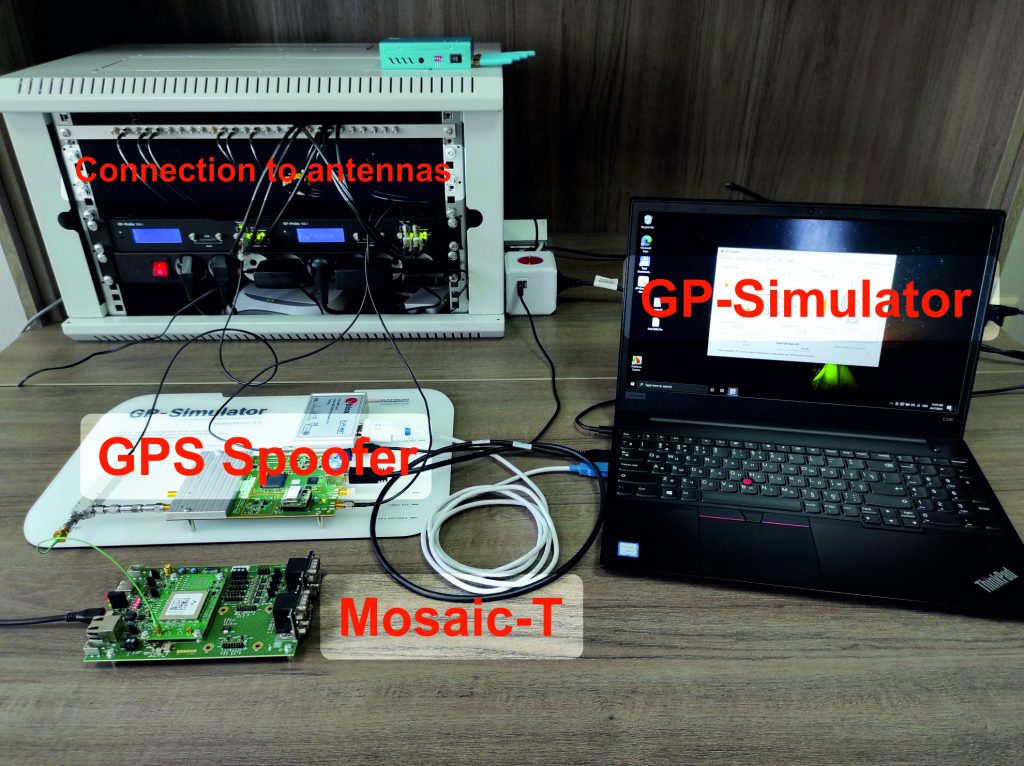
Key facts about Mosaic-T:
- This is the first chipset that we can’t hack using GPS-SDR-SIM and SDR.
- It amazingly suppresses single-tone, FSK, and wideband interference.
- It has good resistance to non-coherent GNSS spoofing attacks.
Introduction
Recently we got a Mosaic-T Evaluation Kit (FW version 4.8.2) from Septentrio. It is a multi-band, multi-constellation GNSS receiver explicitly designed for timing applications. We thought it would be another easy target for GNSS spoofing… However, we were wrong.
We were so impressed by the performance of the AIM+ technology that we decided to write a detailed review.
“AIM+ advanced anti-jamming, anti-spoofing technology with unique interference monitoring and mitigation” Septentrio.
All the findings provided below are based purely on the results and observations made during extensive testing.
When running the same scenario multiple times, the receiver behaves differently. In this article, we have included only those attempts that characterize the pros and cons of the receiver.
Test Stand
For the spoofing vulnerability test, we use a HackRF One in combination with a GPS-SDR-SIM and a GP-Simulator evaluation kit:
The fake GPS signal was injected into the antenna path through an RF coupler:
In real life, the L2 and L5 bands are always blocked during GNSS spoofing. We did not want to waste time on more complex testbeds with RF generators/jammers. Therefore, we used an antenna with only the L1 band.
The GP-Simulator was carefully calibrated with a spectrum analyzer:
All power levels given in this article refer to the receiver’s input port.
Mosaic-T Configuration
All the constellations were active:
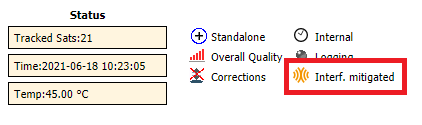
In the web interface, we were interested in this flag specifically, which can be denoted as “Spectrum Clean”, “Spoofing”, or “Interference Mitigated”:
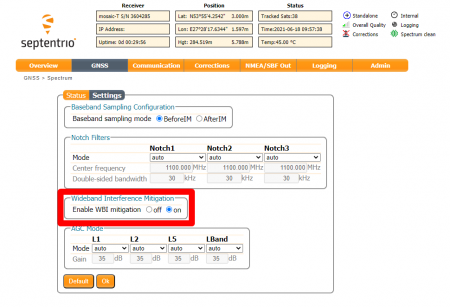
Be sure to enable the Wideband Interference Mitigation option:
To monitor the receiver parameters under tests, we used both the embedded Web interface and RxControl software from Septentrio:
Test 1. HackRF One with GPS-SDR-SIM
We spent a lot of time and effort to make at least one successful attack with GPS-SDR-SIM software and HackRF One — we were unsuccessful.
The scenarios we tried:
- simulation of identical coordinates and almost identical timing
- different combinations of spoofer output power
- a combination of a spoofer and a jammer similar to the setup in this video: https://youtu.be/Ya_B7tqA-X8
- the receiver in GPS-only mode
- receiver resetting under spoofing.
No matter how hard we tried, all our attempts were unsuccessful!
The connection scheme was the same as for the GP-Simulator:
Immediately after activating the spoofer, the receiver lost GPS satellites and stopped providing a navigation solution:
Findings:
- the receiver still saw 10-15 GLONASS/BeiDou satellites under GPS spoofing but did not provide a navigation solution. Galileo L1 shares the same frequency band as GPS L1, so it was blocked.
- the receiver did not indicate “Spoofing”. Instead, it showed “Interference Mitigated”
- the key thing is that the receiver was not spoofed
We then faced a strange behavior from the receiver after resetting under GPS spoofing. When we reset the receiver under spoofing, it did not use the fake signals. And that was truly remarkable:
Then we turned off the spoofer and observed that the receiver did not accept the original signals as well and did not provide a navigation solution until we reset it again:
The spoofer was already disabled in that video. However, the receiver saw only GLONASS and BeiDou satellites and did not provide a navigation solution.
The receiver performed almost flawlessly in this test except for the following:
- did not show “spoofing” status during the obvious non-coherent scenario
- did not provide a solution under spoofing, even when GLONASS and BeiDou were visible
- did not see genuine satellites and did not provide a solution when reset under spoofing.
The last point is the most important. Because the following user story could happen:
- The operator notices that one of the receivers has stopped producing a navigation solution.
- On the receiver’s web interface, the user sees an RF spectrum of the interference and the status “Interference Mitigated”. This is quite a confusing situation because the receiver still sees GLONASS and BeiDou, interference seems to be suppressed, but the coordinates are not defined for some reason.
- The user may decide to reset the receiver because they think it is a glitch.
- Resetting does not help.
- If the interference disappears at this point, the situation becomes even stranger. The receiver would show the “Spectrum clean” status, but the GPS satellites would not be tracked, and the position would not be defined.
Test 2. Non-Coherent Spoofing
In this test, we used the GP-Simulator in non-coherent mode. Differences between the GP-Simulator and the GPS-SDR-SIM + HackRF One:
- true almanac and ephemeris
- accurate LO with better phase noise
- calibrated power level.
We made many attempts to perform non-coherent spoofing. Sometimes the attack was successful, and sometimes it wasn’t. In each attempt, the receiver behaved slightly differently. This section gives a detailed description of only one attempt, which we believe best characterizes the receiver.
In this test, we ran the spoofer with a power level of -100 dBm. This is the power level at the antenna input of the receiver. The typical signal power level of genuine satellites after an antenna’s preamplifier is around -120 dBm. Then we incrementally increased the power up to -30 dBm.
We wanted to show not only the receiver’s tolerance to non-coherent spoofing but also the excellent performance of AIM+ for interference suppression.
Why do we need such a high power level as -30 dBm?
Well, we simulated only the GPS constellation. Other systems should be blocked to spoof the receiver. It can be done using a GNSS jammer or done with a high power level of a spoofer. The high power forces the embedded AGC to decrease gain. Hence, all real signals will be invisible. Moreover, we wanted to demonstrate the AIM+ in action.
Multi-constellation GNSS simulators are still expensive, and in real life, we face a common scenario with a GPS spoofer and GNSS jammer (it is very affordable and effective).
In the table below, we have described all the steps and observations performed:
| Step # | Description | Time | Observation |
| 1 | Spoofer enabled. Input power level is – 100 dBm |
t0 | GPS SNR of genuine sats degraded. No spoofing detection flag. The receiver showed “Spectrum clean” status. The spoofer signal is already visible on the spectrum graph. |
| 20s | Fake GPS signals accepted. No PVT. RxControl showed PVT Error: Outlier. “Spectrum clean” status. |
||
| 2 | – 90 dBm | 2.5m | SNR of the fake signals increased. No PVT. PVT Error: Outlier. “Spectrum clean” status. The fake signal is clearly visible on the spectrum graph. |
| 3 | – 80 dBm | 5.5m | The receiver changed status from “Spectrum clean” to “Interference Mitigated” (AIM+ activated). SNR of the fake signals decreased due to AIM+. PVT Error: Outlier or No Measurements. GLONASS, Galileo, and BeiDou are still visible (28 satts total). |
| 4 | – 70 dBm | 12m | Average SNR of the fake signals is 45 dB. PVT Error: No Convergence. Galileo is blocked. No spoofing detection flag. The receiver showed “Interference Mitigated” status. |
| 5 | – 50 dBm | 18m | No spoofing detection flag. PVT Error: Outlier. The receiver still saw GLONASS (9 satts) and BeiDou (9 satts) thanks to an excellent AIM+ technology. |
| 6 | – 30 dBm | 22m | Successful spoofing!!! All systems except GPS are blocked And no spoofing detection flag. |
| 7 | Spoofer off | 23m | All constellations are perfectly visible. PVT Error: Outlier. No PVT. |
| 8 | Receiver reset | 27m | The receiver restored the tracking of the genuine signals |
Watch a video of the experiment:
Is a high power level of -30 dBm really required? Of course not.
A successful non-coherent attack can also be performed with a power level of -100 dBm under the following scenarios:
- the receiver in GPS-only mode
- multi-constellation spoofer
- GPS spoofer in combination with a GNSS jammer.
Findings:
- In this test, we showed a successful attack. But not all our attempts were successful during the research.
- In the presence of non-coherent spoofing, the receiver stops providing a navigation solution but does not show the “Spoofing” flag. It shows PVT Error: Outlier. So, the receiver saw the inconsistency of the data but did not classify it correctly. We believe that the Septentrio engineers will improve their algorithms.
- AIM+ technology demonstrated excellent performance. With a -50 dBm interference power level, the receiver is able to track GLONASS and BeiDou constellations. In addition, this technology significantly improves protection against spoofing in a spoofing+jamming attack scenario.
- The receiver does not classify a non-coherent fake signal as spoofing.
- If the receiver was successfully attacked, then after disabling the spoofer, the receiver would not track real signals and would not provide a solution. This is a by-effect of receiver protection technology against spoofing. The receiver does not want to switch to new GNSS signals if their parameters are significantly different from the old ones.
Let me remind you that in this and all other tests we assume that the signals in the L2 and L5 bands are completely blocked by jammer.
Test 3. Reset Under Non-Coherent Spoofing
In the first test, we already showed that the receiver does not perceive the original signals after a reset under spoofing. In this test, we showed the effect of the reset under the GP-Simulator.
Test scenario:
| Step # | Description | Time | Observation |
| 1 | Spoofer enabled. Input power level is – 30 dBm |
t0 | All constellations were blocked. No spoofing detection flag. The receiver showed “Interference Mitigated” status. No PVT. |
| 30s | Fake GPS signals were tracked. No PVT. RxControl showed PVT Error: No Measurements. |
||
| 3m | The receiver fixed a navigation solution for a few seconds; then, it indicated an error: No Measurements. The statuses were changing every few seconds. The receiver saw a few GLONASS and BeiDou satellites. No spoofing detection flag. The receiver showed “Interference Mitigated” status. |
||
| 2 | Receiver reset | 5m | The fake GPS satellites were well visible and tracked. Successful PVT “Interference Mitigated” status. GLONASS and BeiDou were totally blocked. |
| 3 | Smooth shift of coordinates to the north by 2000 meters | 6m | Coordinates successfully shifted. No errors or warnings |
| 4 | Spoofer disabled | 8m | All genuine constellations were well defined, but no PVT. The receiver indicated PVT Error: Outlier. “Spectrum Clean” status. |
| 5 | Receiver reset | 10m | The receiver restored the tracking of the genuine signals |
Check out the video of the experiment:
In this experiment, we demonstrated partially successful spoofing. The receiver produced an unstable navigational solution. We showed again what happens if the receiver is reset or turned on under non-coherent spoofing. After disabling the spoofer, the receiver tracks the original signal but does not provide a solution.
Test 4. Coherent Spoofing. The Receiver in GPS-Only Mode
In this experiment, we showed what a deliberate coherent attack with coordinate shift might look like. Since we simulated only GPS signals, we switched the receiver to GPS-only mode. Precisely the same results can be obtained for the receiver in multi-GNSS mode if you use a multi-constellation GNSS simulator.
We used a very simple scenario:
- First, we generated a signal with parameters identical to the real one with a power level of just -100 dBm.
- Then, we moved the coordinates of the simulated point 200 meters to the north.
Watch a video of the experiment:
The receiver was successfully spoofed, and the coordinates shifted. The receiver did not display any errors or warnings. In the first step, the receiver instantly accepted the fake signals. During the attack, the receiver saw a mix of fake and real satellites. When the coordinates shifted, the signals of the real satellites were no longer used in the navigation solution.
There is only one method of detecting such a scenario. This is the spatial signal analysis with multiple antennas.
Test 5. Coherent Spoofing. The Receiver in Multi-Constellation Mode. Power Level: -100 dBm
Here we showed the receiver’s response to GPS spoofing when the receiver saw all the constellations. The scenario is exactly identical to the previous test.
Watch a video of the experiment:
Exactly like in the previous test, the receiver instantly switched to fake signals. But when we started shifting coordinates, the receiver stopped providing a navigational solution and indicated a PVT error: Outlier. In this attempt, the receiver did not show the spoofing flag. But during preparation, we repeatedly encountered successful detection of a spoofing attack when the coordinates were shifted.
We suppose Septentrio engineers have implemented an algorithm to compare the parameters of the GNSS with each other. And when significant deviations are detected, an error is generated. Therefore, other constellations must be blocked for successful spoofing.
Test 6. High-Powered Coherent Spoofing
Unlike the previous test, this one employs a very high power of the GPS spoofer to suppress other constellations. In the rest, the attack scenario was the same.
Watch a video of the experiment:
When the spoofer was activated, the receiver instantly switched to fake signals. Then we applied a shift of coordinates by 2 km. The receiver successfully changed its position.
The receiver failed to detect spoofing even though GLONASS and BeiDou satellites were slightly visible. The receiver classified the spoofer signal as interference and showed the status “Interference Mitigated”.
If the same scenario is repeated with a -50dBm input power level, coordinates shift will not be successful due to the AIM+ technology.
Findings
1.
The receiver demonstrated an excellent ability to resist non-coherent spoofing in all the tests with GPS-SDR-SIM. We conducted many unsuccessful attempts with different scenarios.
2.
The AIM+ technology not only protects against interference but also dramatically improves the receiver’s resistance to spoofing+jamming attack scenarios. Multi-constellation spoofing is still expensive. So, in real-life attacks, combining GPS spoofing and GNSS jamming are widespread.
3.
The receiver stopped generating a navigation solution in the presence of non-coherent GPS spoofing, even with minor power. At the same time, there was no detection of spoofing. This is strange behavior because:
- other GNSS constellations were clearly visible.
- in the presence of even very powerful jamming, the receiver demonstrated a perfect performance.
4.
The embedded spoofing protection algorithms have by-effects:
- If the receiver was successfully attacked, then after disabling the spoofer, the receiver would not track real signals and would not provide a solution. Look at Test 2.
- the same situation when the receiver was turned on or reset under non-coherent spoofing. Look at Test 1 and Test 3 to find out more.
The receiver does not switch to new GNSS signals if their parameters are significantly different from the old ones. Do not reset or turn on the GNSS receiver if spoofing is suspected!
5.
Do not expect the receiver to reliably report spoofing. But it is worth noting that spoofing detection is not the main task of the GNSS receiver. Its primary function is the ability to resist interference!
We observed successful spoofing detection for some scenarios, but we couldn’t find any scenarios with regular and predictable spoofing detection.
Non-coherent counterfeit signals with high power (30-40dB more than the authentic ones) are always classified as interference. Non-coherent signals with low power are invisible to the receiver (and are not a threat to it unless you reboot the receiver at this point).
6.
The receiver cannot resist coherent GNSS spoofing. Yet, it cannot be otherwise. For successful detection of a coherent attack, data from a single antenna is not enough. Check out these links to understand why:
https://youtu.be/5Mw-NKy1BOM
https://youtu.be/Ws76xfJc1Pg
https://gpspatron.com/types-of-gnss-spoofing/
Nevertheless, we saw successful detection of coherent spoofing under the following condition:
- Spoofing only GPS constellations
- The receiver sees the other constellations with a sufficient quality level.
- After the simulated position coordinates shift.
The detection was not stable, and we could not document it properly.
We suppose that the chipset compares the parameters of the constellations/bands, and if it finds a significant difference, it indicates a spoofing flag. This is a good approach. But in real life, we face the following attack scenarios:
- all constellations are spoofed on L1. L2/L5 are jammed.
- GPS L1 and GLONASS L1 are spoofed. GPS L2/L5, GLONASS L2/L5. Galileo L1/L2/L5, BeiDou L1/L2/L5 are jammed.
- Only GPS is spoofed, but the power level is high enough to block an embedded preamplifier of a receiver, so other constellations are suppressed.
We tested the chipset with FW version 4.8.2. We believe that the receiver hardware platform has the potential to improve software algorithms for spoofing detection. We hope that in future FW version many of the found issues will be fixed (Especially issues 3 and 5).
Disclaimer
In our publications, we are in no way trying to discredit any GNSS chipset vendor. We reckon that Septentrio has done a great job in anti-spoofing and interference mitigation.