Introduction
In this article, we will evaluate the prevailing types of GNSS spoofing, methods, and tools for conducting spoofing attacks, as well as the techniques for their detection.
According to the classification adopted in most scientific publications [1], the following types of GNSS spoofing can be defined:
- Asynchronous attacks;
- Synchronous attacks;
- Synchronous attacks with multiple transmitters;
- Meaconer (attack with repeater).
The prime variances are in the types: synchronous, asynchronous and an attack with a meaconer, since the methods for generating satellite signals fluctuate.
Asynchronous and Synchronous Attacks
The fundamental dissimilarity in synchronous and asynchronous attacks is whether the generated signal falls into the correlation analysis window of the GNSS receiver or not.
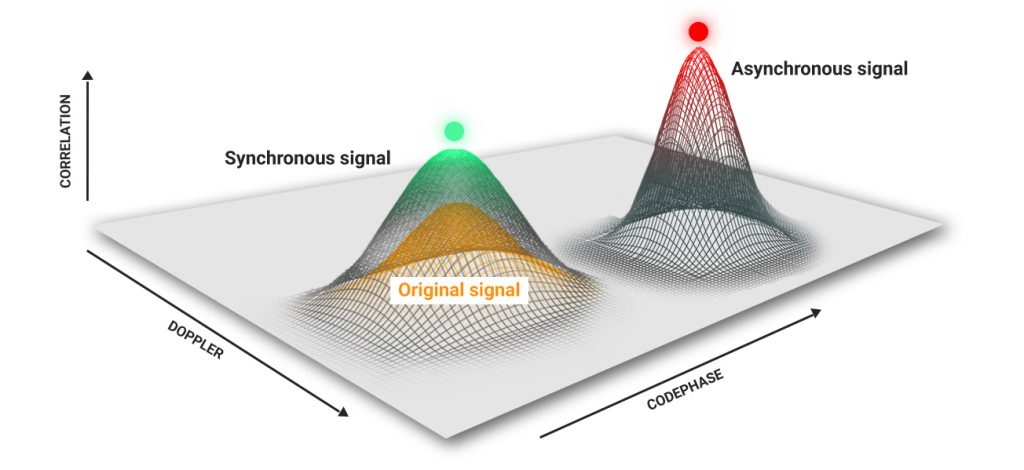
When turned on, the navigation module is in satellite signal search mode. When signals are identified, the receiver enters the tracking mode. The receiver classifies it as interference if the spoofing signal does not fall into the correlation analysis window by the code phase or Doppler.
To perform an effective asynchronous attack, it is necessary, at the first stage, to disrupt the receiver’s tracking of the genuine signals. As a rule, this is accomplished by increasing the power of the spoofer. Consequently, the power of the generated signals in the phase center of the receiver antenna is 40-50 dB higher than the signals of the authentic satellites. After failing to track the signal, most receivers go into search mode and lock onto the counterfeit signals.
In a synchronous attack, the signals of the spoofer are identical to the signals of the satellites in-phase and Doppler, so the receiver switches to the imitation signals without disrupting the signal tracking. In a synchronous attack, the power of the spoofer should be 4 dB higher than the power of the satellite signals.
Thus, simulating identical time and coordinates is not a validation of a synchronous attack.
Execution Methods
An asynchronous attack is the easiest to implement. It is enough to have any SDR (soft-define radio) card: ADALM-Pluto, bladeRF, HackRF or USRP and download an open-source software for generating GPS satellite signals on the Internet, for example, github.com/osqzss/gps-sdr-sim. You can also utilize any laboratory equipment manufactured by Spirent, Rohde & Schwarz or NI with GNSS toolkit for Labview.
To instigate an asynchronous attack, it is enough to generate satellite signals with the correct modulation and frame structure. You can simulate any time and coordinates.

A synchronous attack is more complex. Execution of such an attack requires accurate synchronization with the satellite signals. The phase center of the GNSS receiver antenna needs to simulate signals with the exact same phase of code, Doppler shift, coordinates, and timestamp. The generated signals must contain equivalent almanac and ephemeris data.
At the first stage of a synchronous attack, signals are analogous to the legitimate ones, with a small power level. Then the power is increased to be at least 4 dB higher than the power of the genuine signals. Thus, the “capture” of the correlator occurs. Then a smooth movement of coordinates and/or time can be applied.
Synchronous Attacks with multiple TX
Synchronous attacks with one TX can be detected by the RF signal’s estimation’s angle of arrival. If all satellite signals come from one direction, they are counterfeit. In the case of multiple TX, that detection method doesn’t work.
Performing a synchronous attack with multiple transmitters requires several accurately synchronized spoofers. Each has to generate a signal from only one satellite. Generators should be placed around the “target”. This method complicates the attack detection algorithms.
If drones that will follow the satellites have signals placed from the generators of the “bogus” signals, then it is possible to conduct an etalon (reference) attack (subject to accurate synchronization in time, phase, Doppler and power). To conduct a reference attack on all navigation systems, it is necessary to use at least 30-35 drones with synchronized spoofers, with its proper inertial navigation system and a large reserve of energy. No precedents exist as to whether this type of attack has ever been successfully conducted.
Meaconer
To execute this type of attack, it requires to record the signals of the navigation satellites and reproduce them. It is feasible to conduct an attack both in synchronous and asynchronous scenarios. Available SDR cards can be utilized for the execution of the breach.
On the Internet, there are mentions of the devices with a receiver, transmitter, and FPGA. FPGA is used to distort the received signal in real-time. The main advantage of this technique is the ability to attack receivers that use signals with cryptographic protection. The main disadvantage is that time can only be changed “into the past,” along with the intricacies of coordinate distortion.
Comparative Attack Analysis
- Asynchronous;
- Synchronous;
- Synchronous with multiple transmitters;
- Synchronous with multiple transmitters on drones;
An attack with a repeater will not be considered, since it is a special case of an asynchronous attack, although there is evidence that it is possible to carry out synchronous attacks if the signals are adjusted in real-time.
| Parameter | 1 | 2 | 3 | 4 |
| Availability of open software and instructions on the Internet | + | – | – | – |
| The minimum cost of the equipment (USD) | 300 | 5k | 100k | 2M |
| Tracking disruption when switching to the fake signals | + | – | – | – |
| Requires significant amounts of energy | + | – | – | – |
| Detection Methods:
− SNR monitoring − coordinate monitoring − monitoring of time (timestamp) and phase 1PPS − comparison of data from different GNSS − correlation function analysis − angle-of-arrival estimation − neural network based anomalies detection |
+\- 1 +\- 2 + +\- 3 + + + |
– – – +\- +\- 4 + + |
– – – +\- +\- +\- 5 + |
– – – +\- – +\- +\- |
Notes:
- Since the GNSS receiver cannot measure the absolute power level of the satellite’s signals, only the signal-to-noise ratio can be used to detect spoofing. However, the signal-to-noise ratio can be simulated. Experience shows that with “actual” spoofing in Moscow, the SNR goes down.
- Even with asynchronous spoofing, the coordinates may not change if a deliberate attack on your infrastructure transpires.
- When executing a “real” spoofing attack on GPS and Glonass, other systems are usually jammed.
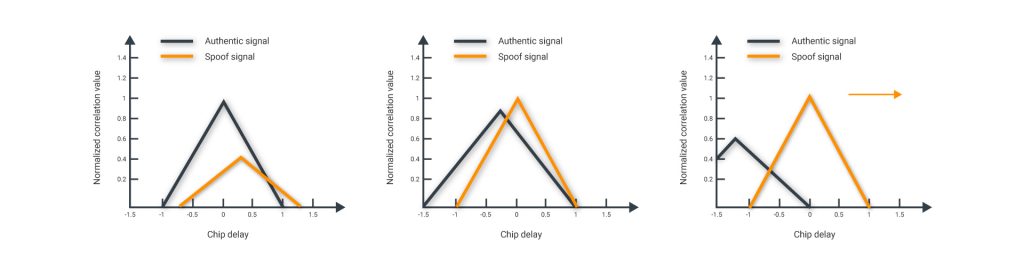
- With a synchronous attack, it is possible to analyze the correlation function to identify surplus “replicas” of the signal. Nonetheless, due to multipath, there is a glitch with the differentiation of the signals of the spoofer and signals reflected from buildings.
- The likelihood of detecting synchronous spoofing with multiple transmitters depends on the precision of the synchronization of the generators and their alignment relative to the target.
Sources
- Van der Merwe, Johannes & Zubizarreta, Xabier & Lukcin, Ivana & Rügamer, Alexander & Felber, Wolfgang. (2018). Classification of Spoofing Attack Types. 10.1109/EURONAV.2018.8433227
- Ali Broumandan, Ali Jafarnia Jahromi, Saeed Daneshmand, Gérard Lachapelle. GNSS Vulnerability to Spoofing Threats and a Review of Anti-Spoofing Techniques
- Shafiee, E & Mosavi, M & Moazedi, Maryam. (2017). Detection of Spoofing Attack using Machine Learning based on Multi-Layer Neural Network in Single-Frequency GPS Receivers. Journal of Navigation. 71. 1-20. 10.1017/S0373463317000558
- Radin D.S., Swaszek P.F., Seals K.C., Hartnet R.J. GNSS Spoof Detection Based upon Pseudoranges from Multiple Receivers; Proceedings of the 2015 International Technical Meeting of the Institute of Navigation; Dana Point, CA, USA. 26–28 January 2015
- Zhang Z.J., Zhan X.Q. GNSS Spoofing Network Monitoring Based on Differential Pseudorange. Sensors. 2016;16:1771 doi: 10.3390/s16101771
- Zhang, Zhenjun & Zhan, Xingqun. (2018). Statistical analysis of spoofing detection based on TDOA: SPOOFING DETECTION BASED ON TDOA. IEEJ Transactions on Electrical and Electronic Engineering. 13. 10.1002/tee.22637
- Broumandan A., Jafarnia-Jahromi A., Lachapelle G. Spoofing detection, classification and cancelation (SDCC) receiver architecture for a moving GNSS receiver. GPS Solut. 2015;19:475–487. doi: 10.1007/s10291-014-0407-3
- Psiaki M.L., O’ Hanlon B.W., Bhatti J.A., Shepard D.P., Humphreys T.E. GPS spoofing detection via dual-receiver correlation of military signals. IEEE Trans. Aerosp. Electron. Syst. 2013;49:2250–2267. doi: 10.1109/TAES.2013.6621814
- Wang W.Y., Chen G., Wu R.B., Lu D., Wang L. A low-complexity spoofing detection and suppression approach for ADS-B; Proceedings of the Integrated Communications Navigation and Surveillance (ICNS) Conference; Herdon, VA, USA. 21–23 April 2015
- Psiaki, M.L. & Powell, S.P. & O’Hanlon, B.W.. (2013). GNSS spoofing detection: Correlating carrier phase with rapid antenna motion. 24. 53-58
- Tao H.Q., Li H., Lu M.Q. A Method of Detections’ Fusion for GNSS Anti-Spoofing. Sensors. 2016;16:2187 doi: 10.3390/s16122187.
- Ke Liu, Wenqi Wu, Zhijia Wu, Lei He, and Kanghua Tang. Spoofing Detection Algorithm Based on Pseudorange Differences
