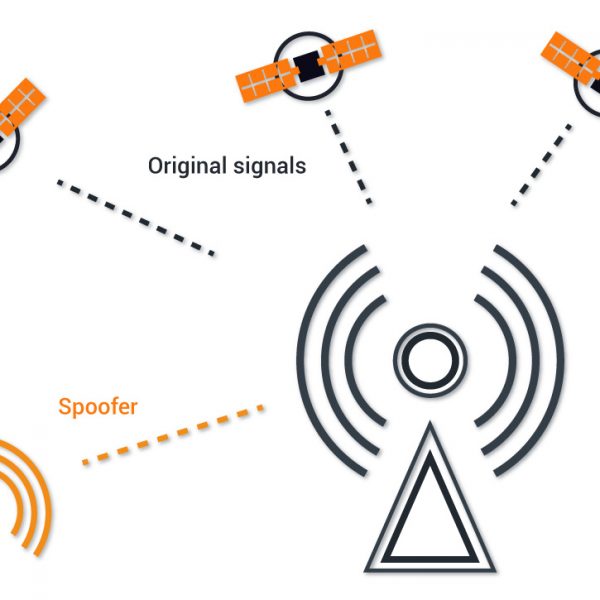
The extensive distribution of low-cost software-defined radio (SDR) platforms, in addition to an assortment of open-source projects for the simulation of GPS signals (i.e., GPS-SDR-SIM), have amplified the number of GNSS spoofing attacks that can range from small to nationwide.
An effective GNSS spoofing attack can cause massive financial and operational damages, in particular for time-critical infrastructures and systems. Timeservers with GNSS synchronization are sourced in banking operations, cellular communication networks, power grid systems, nuclear reactors, digital video broadcasting, and many more. Therefore, even the smallest time shift in one of the system nodes can lead to data corruption and unpredictable consequences.
Due to the trivial amount of testing in the field and absence of substantial precedents, we have insufficient data as to what kind of damages can transpire by GNSS spoofing attacks on large-scale organizations (i.e., banking systems, distributed networks, etc.). This leads to the conclusion that the existing software is not proficient in handling such scenarios without undesired economic and infrastructural losses, leaving most systems and infrastructures vulnerable to potential spoofing attacks.
This paper intends to launch a series of articles aimed at reviewing and discussing various types of GPS spoofing attacks:
- Asynchronous;
- Synchronous;
- Synchronous with multiple transmitters;
- Synchronous with multiple transmitters on drones;
- Repeater.
All our findings in the corresponding articles are valid and applicable regarding unencrypted civilian signals. In this series of articles, we describe and review various types of spoofing attacks, potential scenarios of their implementation, as well as available methods of detection. We will elaborate on complex processes and technical issues in a candid language, making simplifications from the point of academic science.
Asynchronous Spoofing Attacks
An asynchronous spoofing attack is one of the simplest attack forms that imply a power-take-over or a hard-take-over strategy through the transmission of a non-time synchronized signal(s). [1]
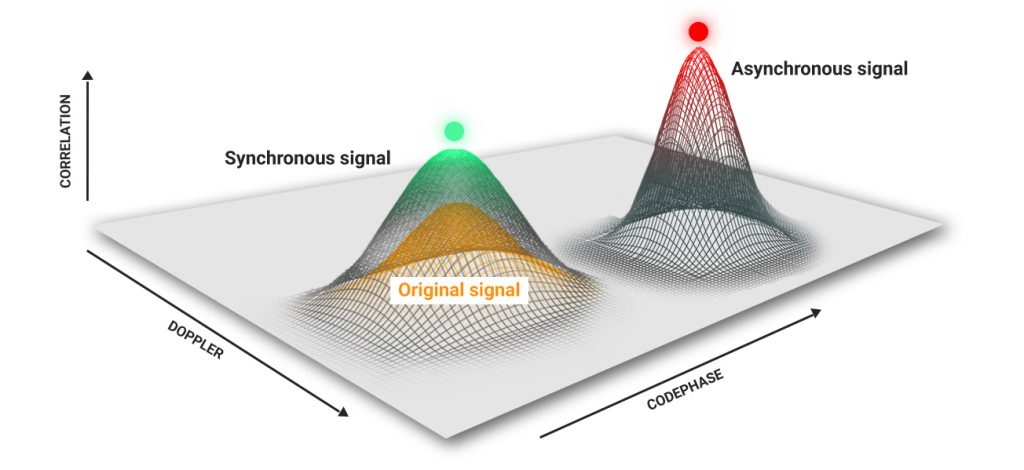
First, let us look into the difference between synchronous and asynchronous spoofers. In the case of an asynchronous attack, a spoofer transmits stronger false signals than the legitimate, causing the receiver to lose track of the satellites and lock onto the dominating spoofing signal(s). Conversely, synchronous attacks imply transmitting signals synchronize with the original ones and then overriding the latter.
Synchronous spoofers imply a smooth-take-over or a soft-take-over by means of generating a signal identical to the prototype in terms of time, coordinates (pseudo-range) and Doppler shift (where the correlation peak of the spoofed signal is within the tracking window of the receiver). The time difference between the original and the spoofing signals should not exceed 500 nanoseconds. Therefore, when the power of the spoofing signal is higher than the archetype, by design, the GNSS receiver locks onto the spoofing signal. Consequently, the GNSS receiver identifies the synchronous signal as genuine. In this case, the receiver produces the same time, coordinates, as well as the 1PPS signal.
Alternatively, in asynchronous attacks, the signal does not align with the prototype in terms of time and Doppler shift. At first, the asynchronous signal is identified by the receiver as an interference. For the receiver to lose the original signal (caused by interference), the power of the spoofing signal has to be amplified (by at least 30 dB) compared to the power of the first. When the receiver loses the authentic signal and, like most receivers, goes into Signal Acquisition Mode, it may identify and lock onto the stronger spoofing signal. [2] Nonetheless, some receivers may wait for the true signal within the expected time and Doppler shift zone without locking onto the spoofing signal. For more insight on the corresponding difference, refer to this article. [3]
Methods of Implementation/Execution
To carry out an effective asynchronous spoofing attack, numerous open-source projects from GitHub can be utilized with no additional modifications (i.e., such SDRs as ADALM-Pluto, bladeRF, HackRF One, or USRP, and more).
With such a large number of the corresponding projects and platforms, their statuses, as well as numerous materials and discussions on specialized forums GPS spoofing is gaining popularity within the field. To view more examples and existing open-source solutions, explore this link.
At present, open-source and convenient software is capable of simulating any time, coordinate, and even moving scenarios. The corresponding software allows loading almanac and ephemeris data, triggering poor PVT solutions or altering the position. As an example, broadcast ephemeris data can be obtained from various sources such as link-1 or link-2.
In the case of asynchronous spoofing attacks, the increment of power produced by the letter makes this form of breach evident (i.e., by signal-to-noise ratio monitoring). Asynchronous attacks are considered brute-force infringements because they do not entail the target’s receiver position.
Advantages
- Economical: GPS spoofers are available for as little as 5$ apiece;
- Easy-to-use/install: Download the corresponding software from one of the sources and follow the step-by-step instructions;
- It does not require high, if any, technical training, knowledge, or skills.
Disadvantages
- Mandates high power generation. However, since the satellite signal on the Earth’s surface is approximate to 155 dBW, it does not pose a significant problem. USRP without an external amplifier is capable of working within the 50-meter range;
- Tracking of true signals can be disrupted and lost when switching to spoofing signals;
- While in tracking mode, most modern chipsets are prone to lose the signal instead of switching to the spoofing signal(s);
- For stationary objects such as time servers, this type of spoofing attack is measurable by simple algorithms that monitor the signal-to-noise ratio, as well as coordinate and timestamp shifts.
Nevertheless, with trivial software upgrades, an intruder can imitate a bona fide signal-to-noise ratio, existing coordinates, and the corresponding timestamp.
As for moving objects (i.e., self-driven cars), even a simple spoofer can pose a great security threat. For more details on this issue, see article [4].
Detection Algorithms/Methods
At present, numerous algorithms for detecting spoofing have been developed. Most of them are theoretical; however, certain algorithms are based on empirical evidence. Due to the variety and differences in application, each algorithm has its benefits and shortcomings. More detailed and well-presented examples of the types of spoofing, as well as its detection measures, are proposed in article [5].
We can divide the corresponding algorithms/methods into several groups:
Parameters drift monitoring (SNR, coordinates, timestamp, 1PPS)
[6][7][8]
This group of algorithms is the easiest to implement and the most frugal. The commercial receiver’s data can be applied in post-processing. Some chipsets (i.e., u-blox M8 modules) already contain parameters drift monitoring.
Data comparing method
[9][10][11]
Coordinates, time, and velocity parallel the GPS, GLONASS, BeiDou, Galileo GNSS systems, along with inertial navigation systems, cellular networks, Wi-Fi, etc.
Processing data from multiple receivers with spaced antennas
[12][13][14]
This technique is for the simple reason that a spoofer is not competent in simulating accurate coordinates for spaced points.
Correlation function distortion monitoring
[15][16]
This method involves such big-ticket equipment as a soft-defined receiver and plenty of computing power for a detailed analysis of the correlation function. It is uncertain how to distinguish a spoofer signal from the original signal reflected from a building since both the reflected and spoofing signals look the same way.
RF signal angle-of-arrival estimation with an antenna array or a moving antenna
[17][18]
Implementation of this system requires intricate and costly equipment. The corresponding process also implies accurate determination of the signal(s) direction arriving from satellites. Since we know the satellites’ location, we can authenticate them. Even so, this method has similar complications as the analysis of the correlation peak. No details explain how to separate the spoofing signal and the veritable one reflected from the buildings.
Combined methods
[19]
For the detection of single-channel asynchronous spoofing, all the methods mentioned above are effective, although, the first two seem to be less efficient. The parameters drifting monitoring does not guarantee that an aggressor can replicate the same coordinates, timestamp, along with the signal-to-noise ratio for each satellite. The data comparing method can be implemented if the attack is only on one of the systems, for example, GPS. Nonetheless, since the field is evolving and new solutions emerge, all techniques are precarious and should be acknowledged as such.
We recommend reading the article [20], which provides more detailed and technical insight into the mentioned attack methods, as well as the corresponding detection methods.
References:
- Van der Merwe, Johannes & Zubizarreta, Xabier & Lukcin, Ivana & Rügamer, Alexander & Felber, Wolfgang. (2018). Classification of Spoofing Attack Types. 10.1109/EURONAV.2018.8433227
- Broumandan A., Jafarnia-Jahromi A., Daneshmand S., Lachapelle G. Effect of Tracking Parameters on GNSS Receiver Vulnerability to Spoofing Attack; Proceedings of the 29th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+ 2016); Portland, OR, USA. 12–16 September 2016
- Shafiee, E & Mosavi, M & Moazedi, Maryam. (2017). Detection of Spoofing Attack using Machine Learning based on Multi-Layer Neural Network in Single-Frequency GPS Receivers. Journal of Navigation. 71. 1-20. 10.1017/S0373463317000558
- Kexiong (Curtis) Zeng, Shinan Liu, Yuanchao Shu, Dong Wang, Haoyu Li, Yanzhi Dou, Gang Wang, Yaling Yang, Virginia Tech; University of Electronic Science and Technology of China; Microsoft Research. All Your GPS Are Belong To Us: Towards Stealthy Manipulation of Road Navigation Systems
- Esteban Garbin Manfredini – Politecnico di Torino and Colorado University at Boulder; Dennis M. Akos – Colorado University at Boulder; Fabio Dovis – Politecnico di TorinoOptimized. GNSS spoofing detection using commercial receivers Field Data and Experimental Trials. Presentation
- Dehghanian V., Nielsen J., Lachapelle G. GNSS spoofing detection based on signal power measurements: Statistical analysis. Int. J. Navig. Obs. 2012;7:1–8. doi: 10.1155/2012/313527
- Jafarnia-Jahromi A., Broumandan A., Nielsen J., Lachapelle G. Pre-despreading authenticity verification for GPS L1 C/A signals. Navig. J. Inst. Navig. 2014;61:1–11. doi: 10.1002/navi.50
- Wen H.Q., Huang P.Y.-R., Dyer J., Archinal A., Fagan J. Countermeasures for GPS Signal Spoofing; Proceedings of the 18th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS 2005); Long Beach, CA, USA. 13–16 September 2005
- Groves P.D. Principles of GNSS, Inertial, and Multisensor Integrated Navigation Systems. Artech House; Boston, MA, USA: 2013. Navigation Processor; pp. 258–273
- Lee J.H., Kwon K.C., An D.S., Shim D.S. GPS Spoofing Detection Using Accelerometers and Performance Analysis with Probability of Detection. Int. J. Control Autom. Syst. 2015;13:951–959. doi: 10.1007/s12555-014-0347-2
- Nielsen, J & Broumandan, Ali & Lachapelle, Gérard. (2010). Spoofing Detection and Mitigation with a Moving Handheld Receiver. 21. 27-33
- Radin D.S., Swaszek P.F., Seals K.C., Hartnet R.J. GNSS Spoof Detection Based upon Pseudoranges from Multiple Receivers; Proceedings of the 2015 International Technical Meeting of the Institute of Navigation; Dana Point, CA, USA. 26–28 January 2015
- Zhang Z.J., Zhan X.Q. GNSS Spoofing Network Monitoring Based on Differential Pseudorange. Sensors. 2016;16:1771 doi: 10.3390/s16101771
- Zhang, Zhenjun & Zhan, Xingqun. (2018). Statistical analysis of spoofing detection based on TDOA: SPOOFING DETECTION BASED ON TDOA. IEEJ Transactions on Electrical and Electronic Engineering. 13. 10.1002/tee.22637
- Broumandan A., Jafarnia-Jahromi A., Lachapelle G. Spoofing detection, classification and cancelation (SDCC) receiver architecture for a moving GNSS receiver. GPS Solut. 2015;19:475–487. doi: 10.1007/s10291-014-0407-3
- Psiaki M.L., O’ Hanlon B.W., Bhatti J.A., Shepard D.P., Humphreys T.E. GPS spoofing detection via dual-receiver correlation of military signals. IEEE Trans. Aerosp. Electron. Syst. 2013;49:2250–2267. doi: 10.1109/TAES.2013.6621814
- Wang W.Y., Chen G., Wu R.B., Lu D., Wang L. A low-complexity spoofing detection and suppression approach for ADS-B; Proceedings of the Integrated Communications Navigation and Surveillance (ICNS) Conference; Herdon, VA, USA. 21–23 April 2015
- Psiaki, M.L. & Powell, S.P. & O’Hanlon, B.W.. (2013). GNSS spoofing detection: Correlating carrier phase with rapid antenna motion. 24. 53-58
- Tao H.Q., Li H., Lu M.Q. A Method of Detections’ Fusion for GNSS Anti-Spoofing. Sensors. 2016;16:2187 doi: 10.3390/s16122187.
- Ke Liu, Wenqi Wu, Zhijia Wu, Lei He, and Kanghua Tang. Spoofing Detection Algorithm Based on Pseudorange Differences