Introduction
In this video, we proved that GPS spoofing has become simple and inexpensive. We were successful in spoofing the UBLOX M8T module with embedded spoofing detection and mitigation algorithms. The spoofing detection flag did not function during our experiment and we decided to discover why.
In this article, we styled an experiment in which we attempted to create module conditions to detect spoofing without error.
Setup
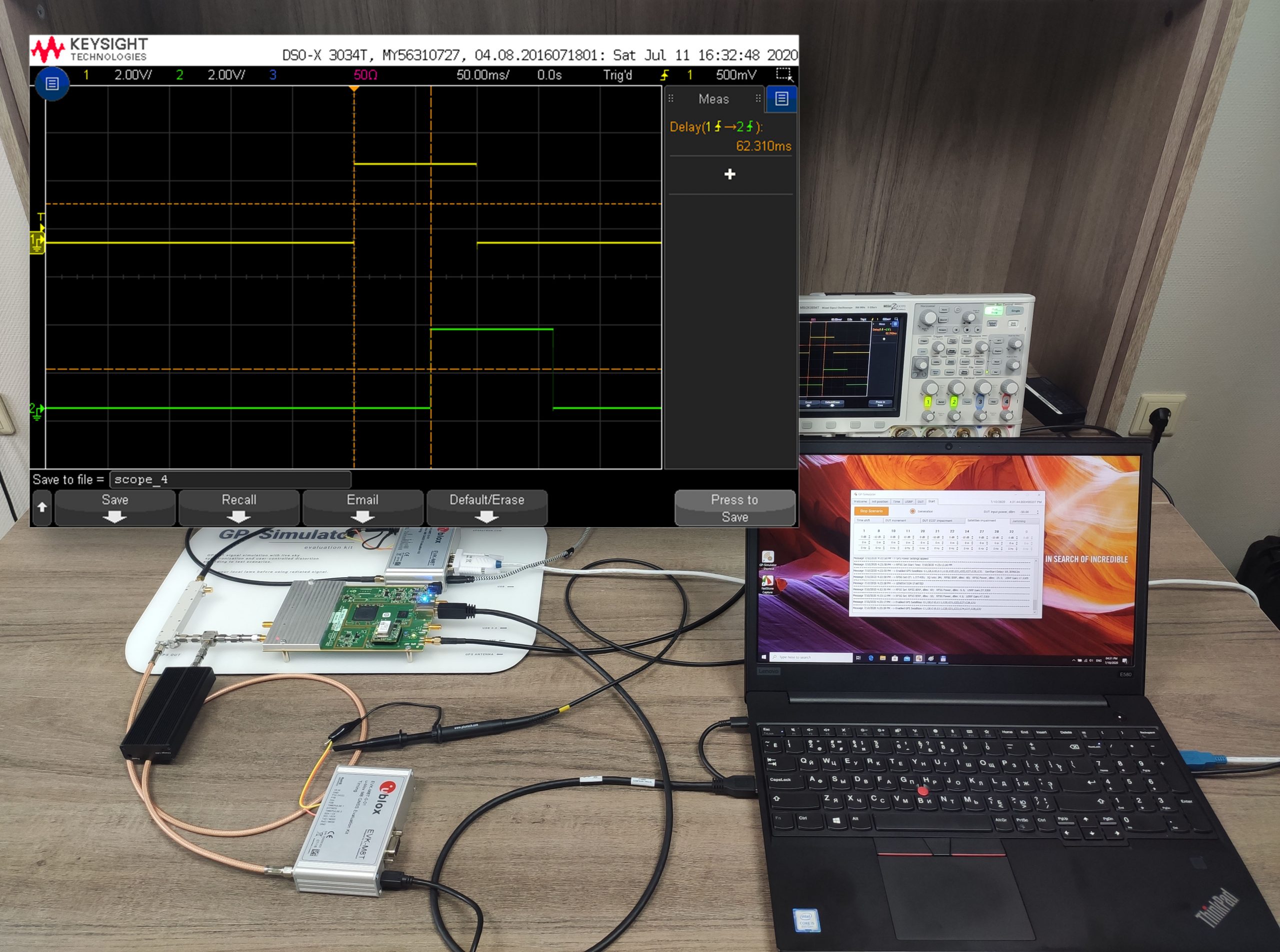
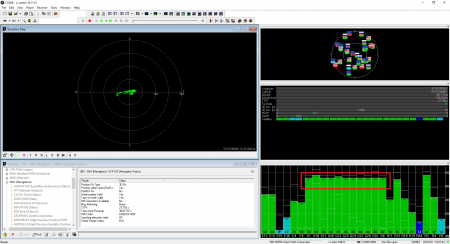
The experiments were conducted under live-sky conditions with the GP-Simulator Test Kit. The kit components are as follows:
- Ettus Research USRP Bus Series with GPSDO;
- Ublox M8T GNSS receiver for live sky synchronization (We utilized it as a reference to check PPS offset);
- GPSPATRON software.
- UBLOX EVK-M8 Evaluation Kit – Device Under Test.
- UBLOX EVK-M8 Evaluation Kit – Reference PPS source, the part of GP-Simulator Test Kit.
- The GNSS jammer is used to block an ariginal sattelites’ signals.
- Three active GNSS antennas.
- RF coupler, attenuators.
- Oscilloscope to measure offset between PPS phases.
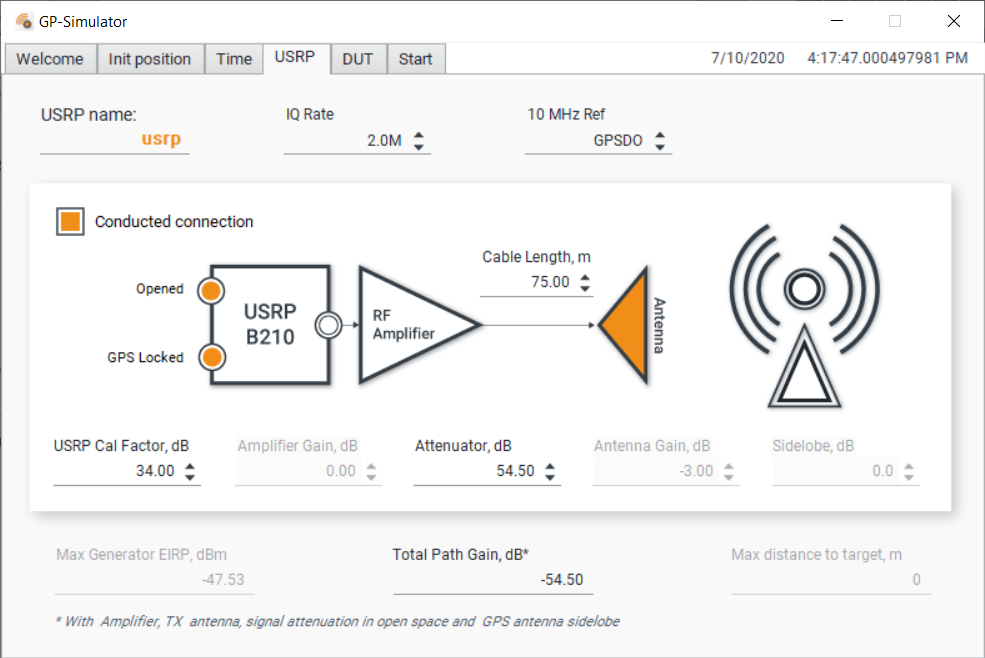
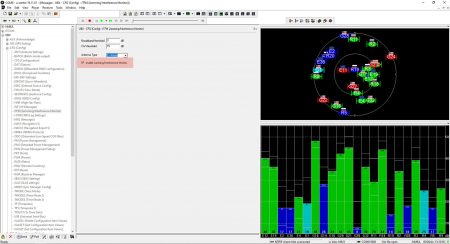
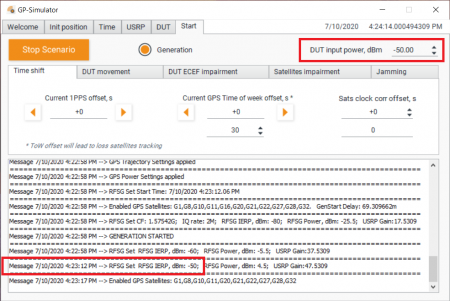
GP-Simulator Power Level Calibration
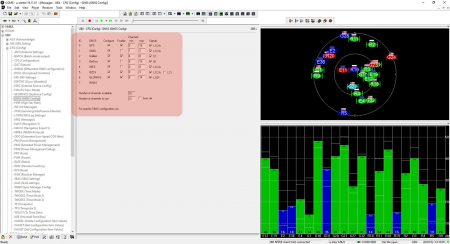
UBLOX M8T Configuration
We utilized U-Center to configure the GNSS module and made the following settings:
- Used GNSS constellations – GPS, Galileo, and GLONASS
- Interference monitoring – Enable
Experiment #1 - Asynchronous Spoofing Attack
The purpose of this experiment is to discover the conditions the embedded spoofing detection flag would trigger. We simulated a GPS signal with a large power level and improper correlation peak position. Learn more about spoofing attack scenarios in our article.
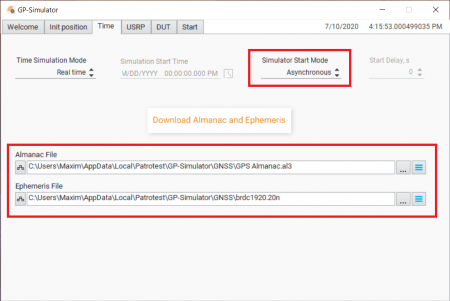
We utilized current ephemeris and almanac data from:
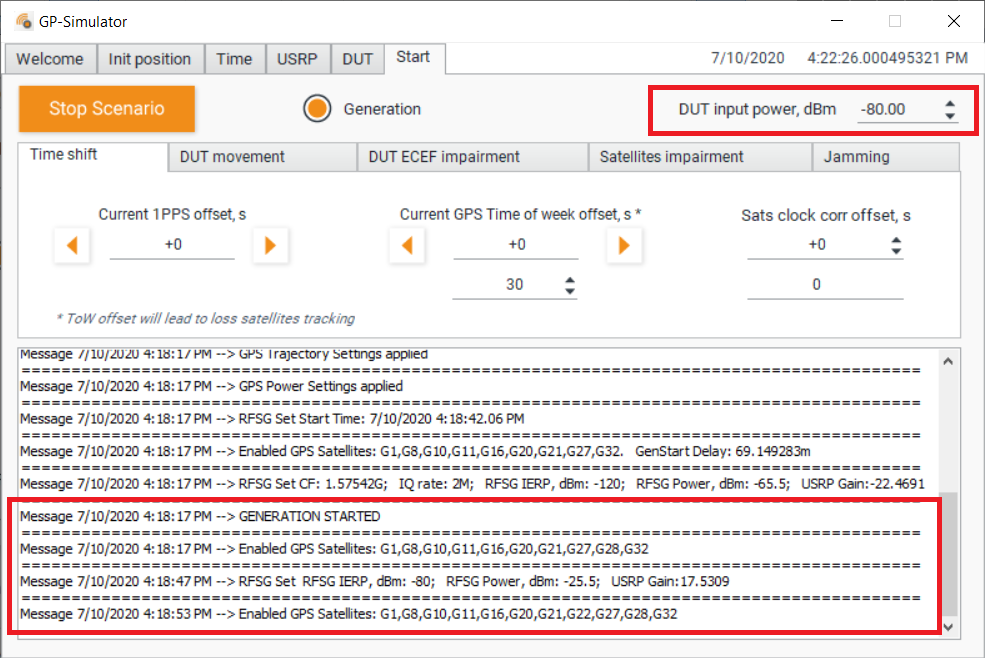
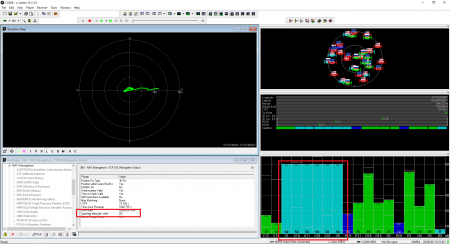
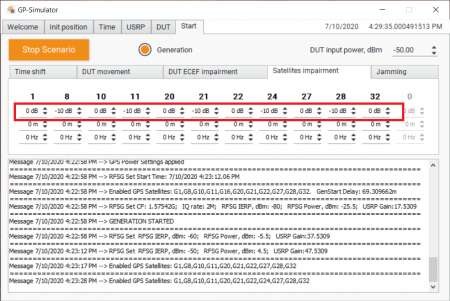
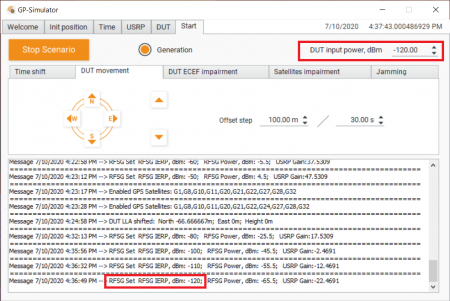
Run the generation with output power level -80 dBm:
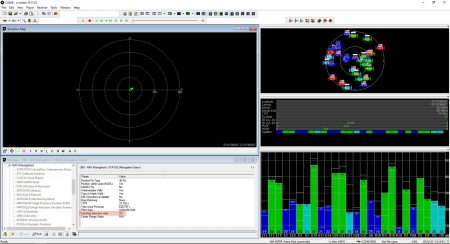
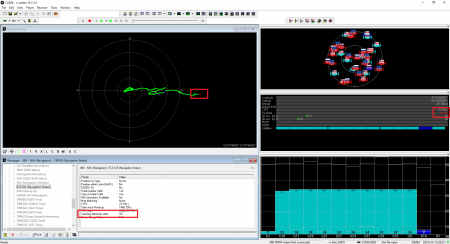
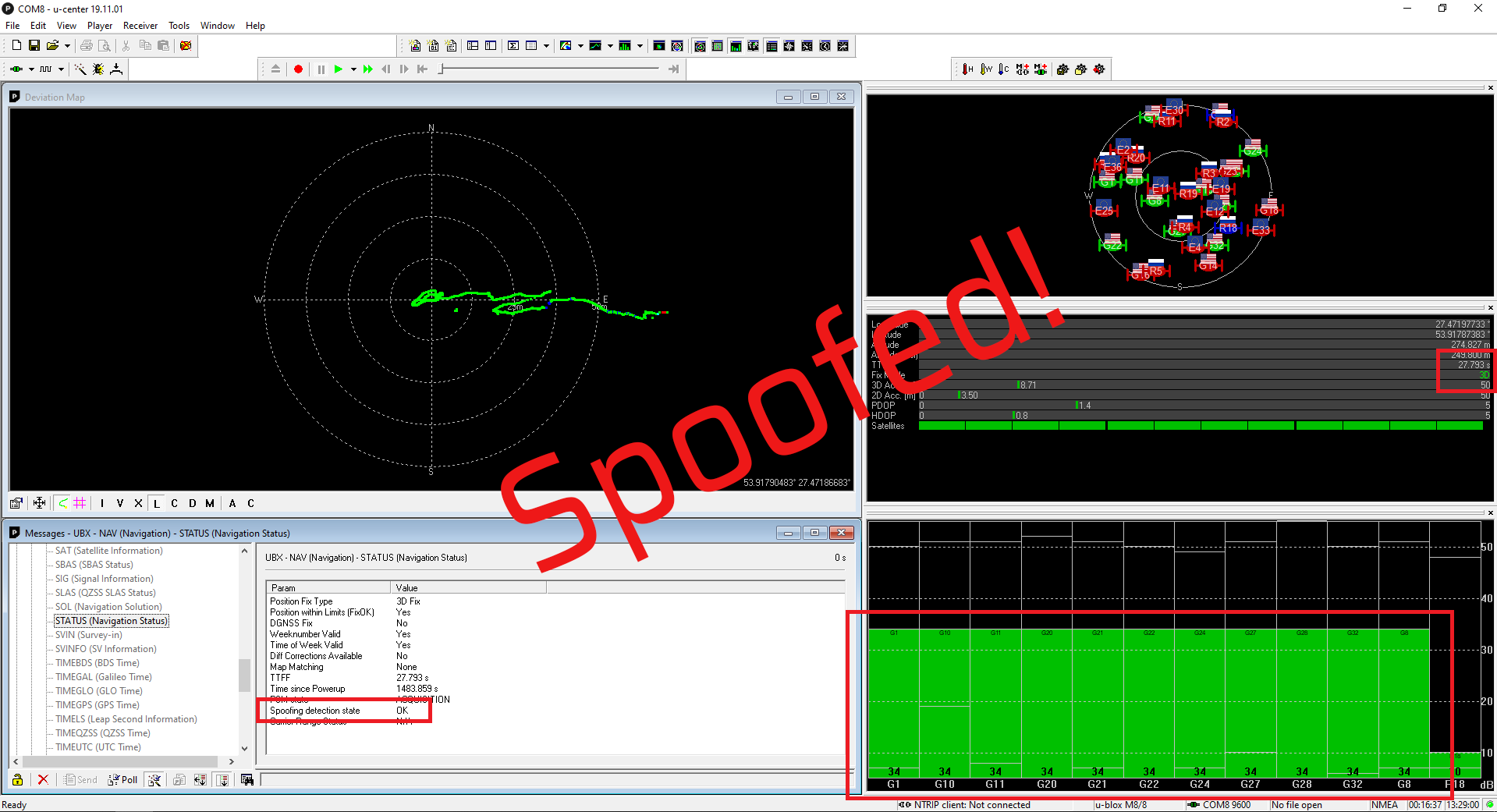
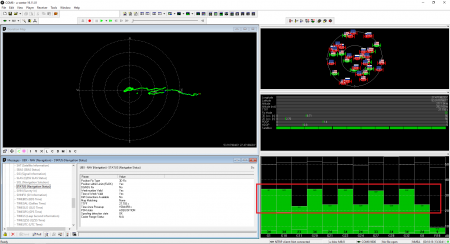
The receiver detected the counterfeit satellite signals but did not use it. Spoofing detection flag showed OK:
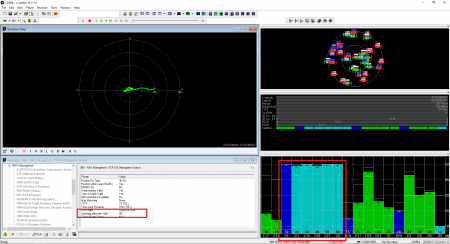
To show that the receiver was locked to the counterfeit signal, we set the relative power of the satellites to minus 10 dB in steps:
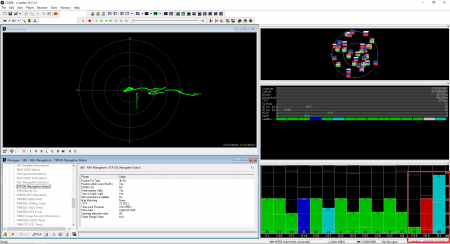
15 seconds after the spoofer was turned off, the receiver switched to the authentic signals. The PPS phase has taken its place.
Experiment #2 - Synchronous Spoofing Attack
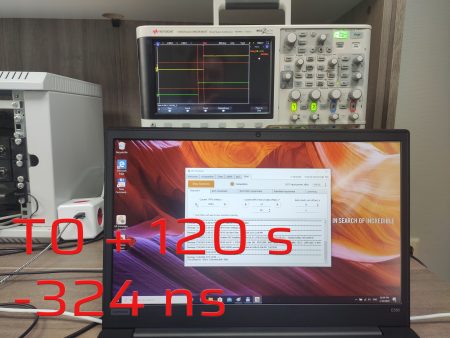
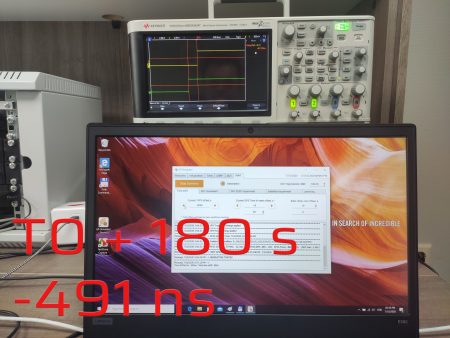
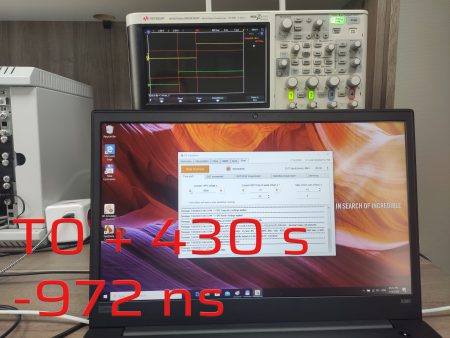
In this experiment, we wanted to understand how the receiver would perform under a synchronous attack. In the first step, we generated a signal that mimics a genuine one with overpowering in 20 dB. Then we added 500 ns offset.
The receiver was configured the same way as in the previous experiment.
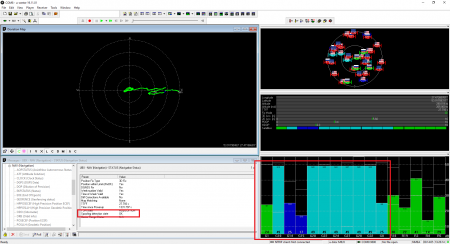
500 ns offset
After thirty seconds, the signal phase began to move at a sluggish pace. Although the module reveals that it uses satellites from three navigation systems, the PPS phase only follows the GPS. Three minutes later after offset adding, the PPS offset was about 900 ns. This overjump might be related to the transients in the Kalman filter due to a severe time shift.
Conclusion
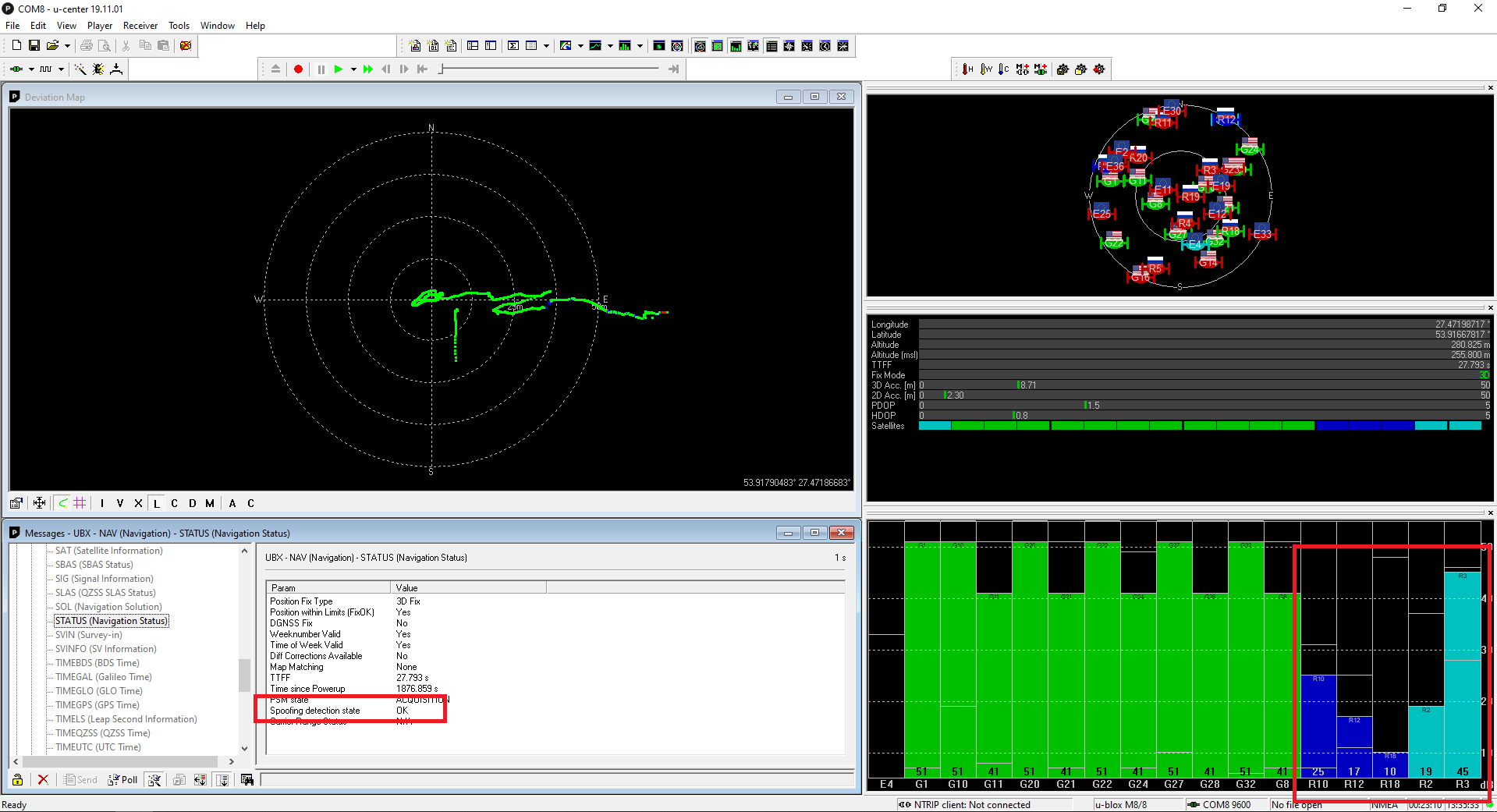
1. During the experiments, we could not realize conditions to trigger an embedded spoofing detection flag. A UBLOX support team provided the following explanation:
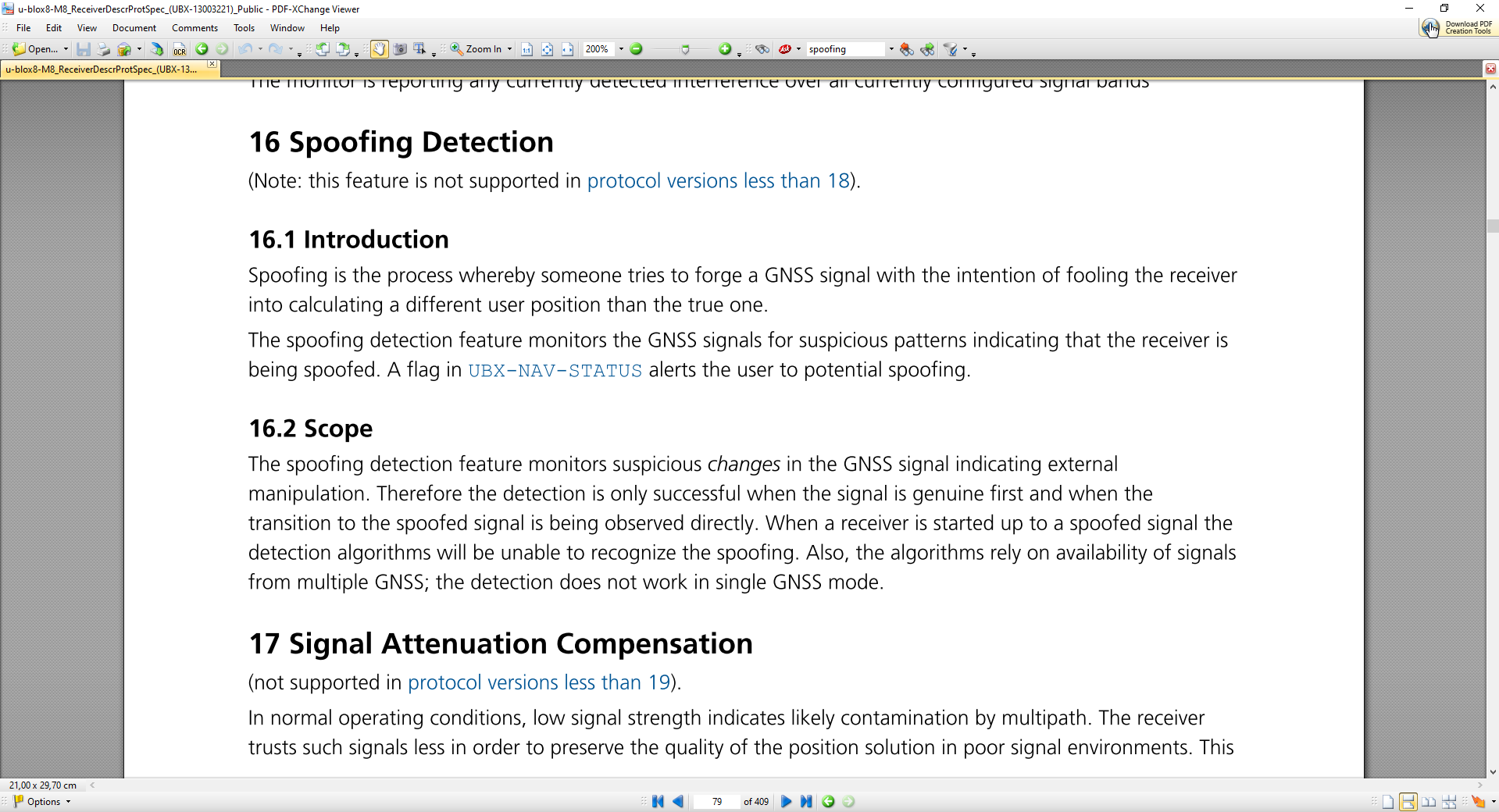
-The spoofing detection feature monitors the GNSS signals for suspicious patterns indicating that the receiver is being spoofed.
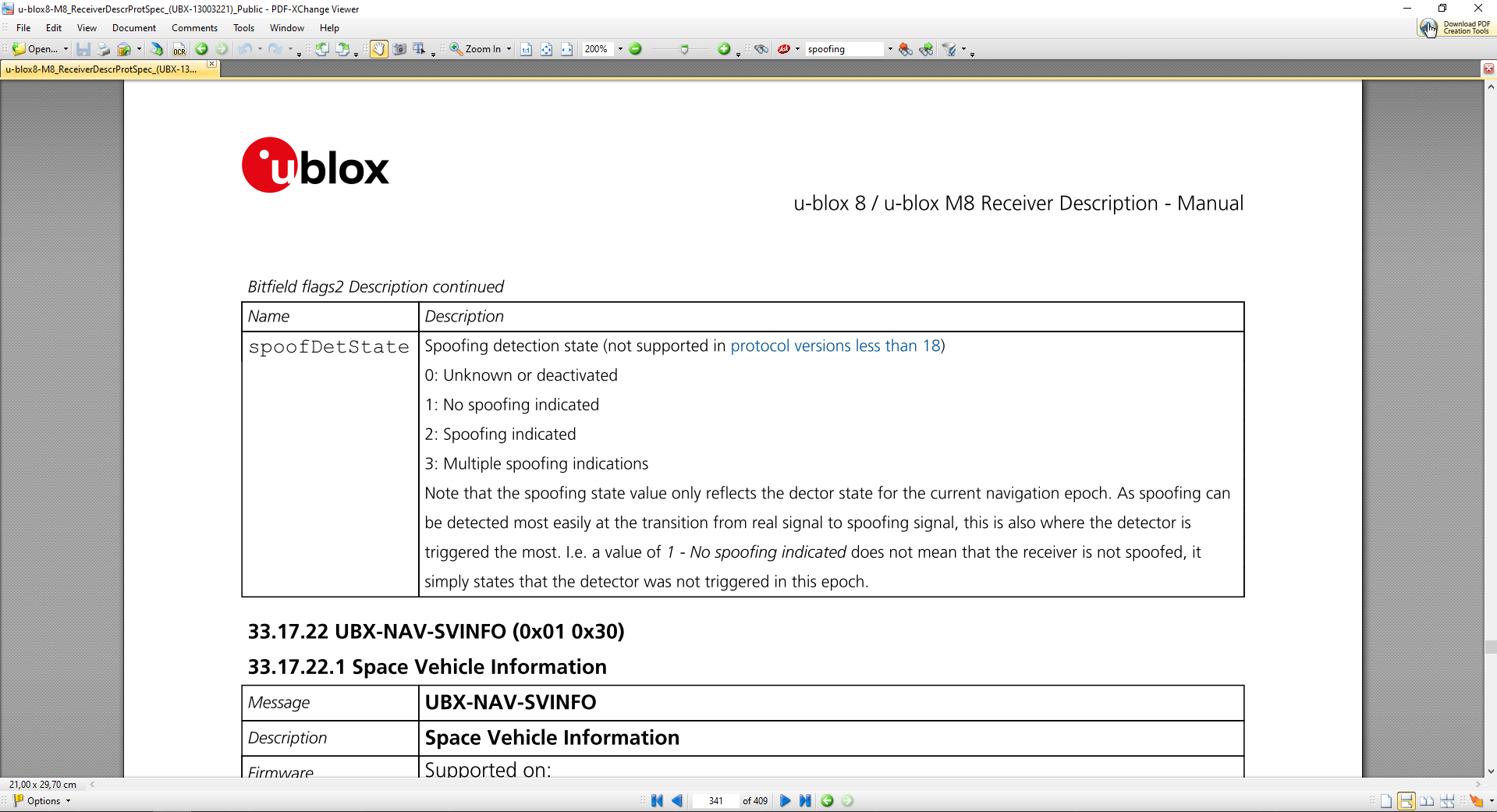
-A flag in UBX-NAV-STATUS message (flags2 – spoofDetState) alerts the user to potential spoofing.
-The spoofing detection feature monitors suspicious changes in the GNSS signal indicating external manipulation.
-Therefore the detection is only successful when the signal is genuine first and when the transition to the spoofed signal is being observed directly.
-When a receiver is started up to a spoofed signal the detection algorithms will be unable to recognize the spoofing.
-Also, the algorithms rely on availability of signals from multiple GNSS.
-In general the receiver will look for inconsistencies in signal strength and SV positioning across all the received constellations to make a judgement on spoofing.An additional point is that M8 products are not our latest generation of products. 9th generation products are already on the market.
Therefore, I consider we have met all the necessary conditions for the success of the embedded spoofing detection algorithms. However, for some reason, we did not see it working successfully. In the next experiment, we will try to test the 9th generation module.
2. Under a synchronous attack, the receiver was following the shifted counterfeit GPS signal. It appear as if the M8T module uses GPS constellation as a reference and does not take into account other systems!
Disclaimer
In this study, we made no attempt to discredit UBLOX’s products. Some vendors of time servers’ rely on spoofing detection aptitude of the M8T module. We only wanted to discover how it performs.
Although we have not been able to create conditions for the effective triggering of the spoofing detection flag, we are not claiming that the algorithms do not work. We hope to get detailed comments from the UBLOX’s support team or the professional community.