GPSPATRON is facilitated to protect GNSS-dependent infrastructure against GNSS spoofing/jamming or other GNSS signals anomalies that cause time/position accuracy degradation. GPSPATRON uses a 3-channel GP-Probe with triple-spaced antennas. The probe measures various signal parameters of all discernable satellites and sends it to the GP-Cloud for real-time data analysis. The GP-Cloud uses a neural network for anomalies detection. If an inconsistency is discovered, algorithms classify its type: jamming or spoofing (intentional or unintentional).
GPS/GNSS spoofing is not a novel problem for GNSS experts, but 95% of cybersecurity professionals are not familiar with the issue. The main source of synchronization of critical infrastructure is a time server with a GNSS module, which is ultra-sensitive to spoofing. Thanks to the proliferation of low-cost SDR and open-source software for counterfeit satellite signal generation, the problem is becoming critical.
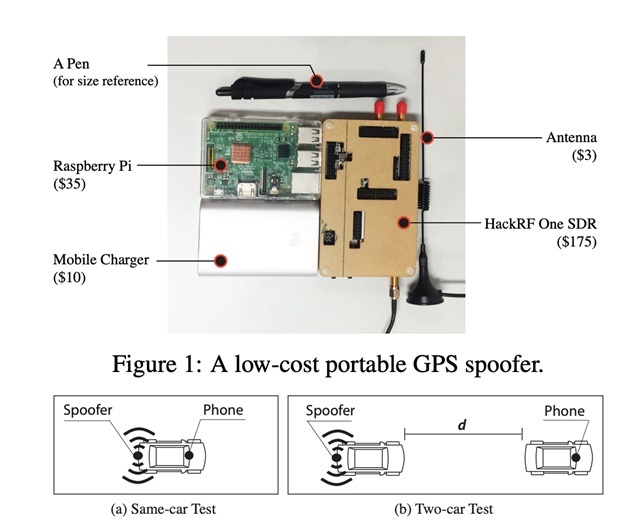
Nowadays, anyone can conduct a spoofing attack on a bank’s processing center in 15 minutes with $ 200 HackRF One and software downloaded from GitHub (e.g., osqzss/gps-sdr-sim). There are also many files on the Internet with exhaustive instructions about spoofing/jamming.
Authorities for VIP protection against drones actively utilize GNSS spoofing. AArmed Forces use GNSS spoofing during military exercises and for base protection against UAF.
Persons use a GPS spoofer to:
- Mislead vehicle tracking systems;
- Cheat services with geolocation: carshare, bike-share, Pokemon Go;
GPSPATRON detects GNSS spoofing/jamming events every day, with a duration from a few minutes to several days.
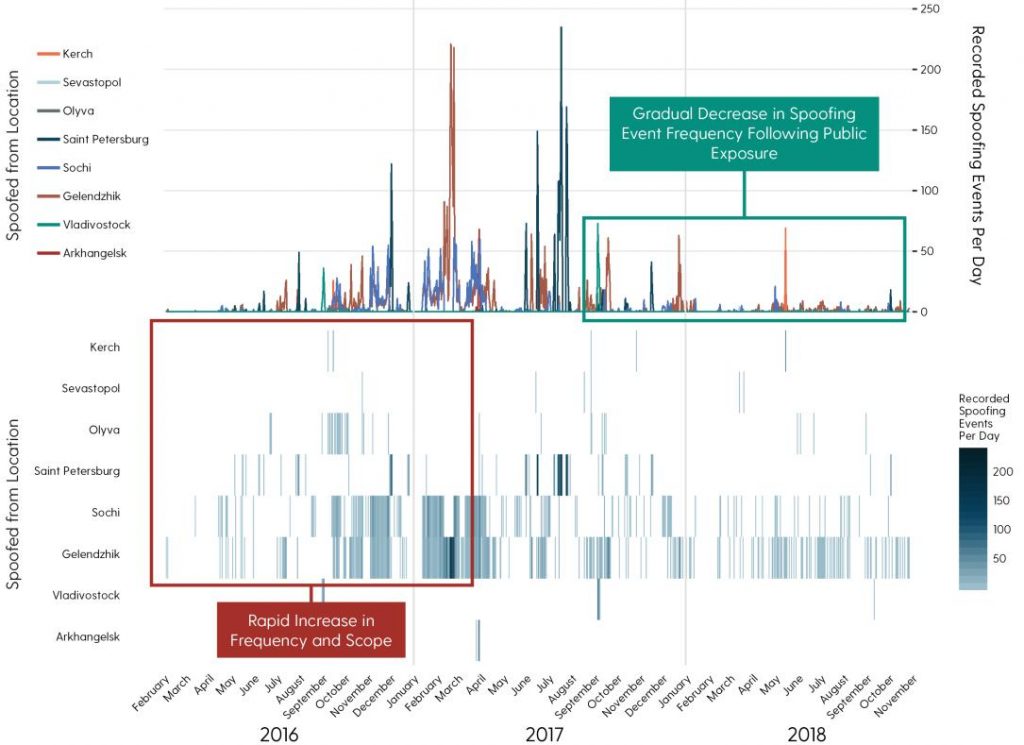
In early 2019, a non-profit organization C4ADS released a report on the use of GPS spoofing — ABOVE US ONLY STARS. There were 9883 emergency events registered over the two years of research.
When GNSS spoofing is used in a densely populated city, then banks, cellular base stations, smart power grids, and other GNSS-dependent infrastructure can depreciate from this attack.
Detection algorithms
We utilized our GPS spoofer to create a detection method. We developed various breach techniques, conducted hundreds of experiments, and evaluated the time servers of leading manufacturers.
There are many infringement scenarios, but we recognize two main categories: the deliberate and non-deliberate attack. In the case of a deliberate attack, the intruder simulates a signal in the phase center of the “target” antenna with identical parameters of the genuine signal. The power of counterfeit signals should be slightly higher than the power of authentic signals. As a result, an intruder can smoothly change the time and/or coordinates.
In the instance of a non-deliberate attack, the spoofer imitates bogus coordinate and time data. The power of “fake” signals should be several times higher than the original signal — about 30…50 dBs. This is called an asynchronous attack.
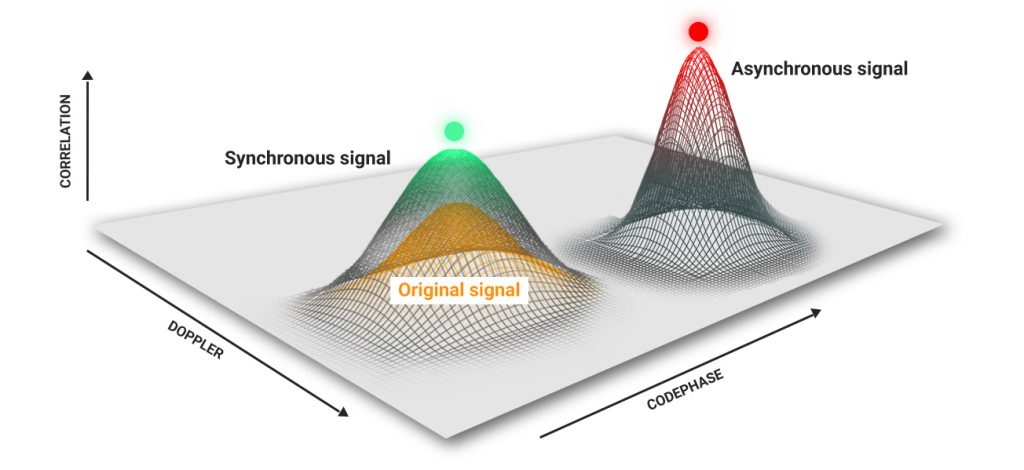
This is an unrefined classification, but we can affirm with confidence that all synchronous attacks are deliberate. The methods for detecting synchronous and asynchronous attacks vary, as are the responses of the navigation modules. An asynchronous attack can be identified with no trouble due to the sharp jumps in power, coordinates, and time.
GPSPATRON estimates the distortion of a navigation field and detects for anomalies using a neural network. Our system can only be deceived by many spoofers mounted on drones with synchronized atomic clocks, but it’s daunting to perform such an infraction in real life.
GPSPATRON for Spoofing Detection
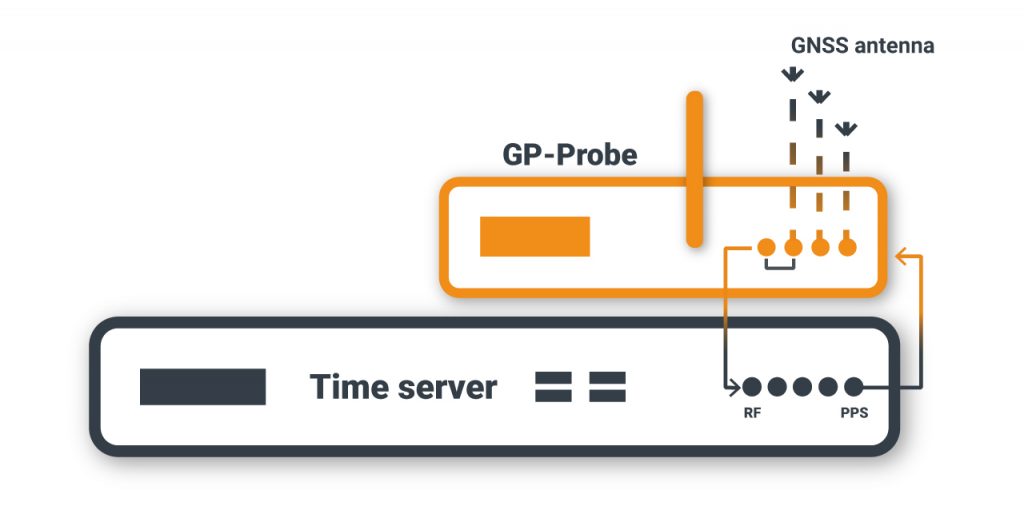
1. Install the GP-Probe at a control point, e.g., near the time server.
2. The GP-Probe registers more than 900 parameters per second for all visible satellite GPS, GLONASS, BeiDou, Galileo, and sends this data to the cloud for processing.
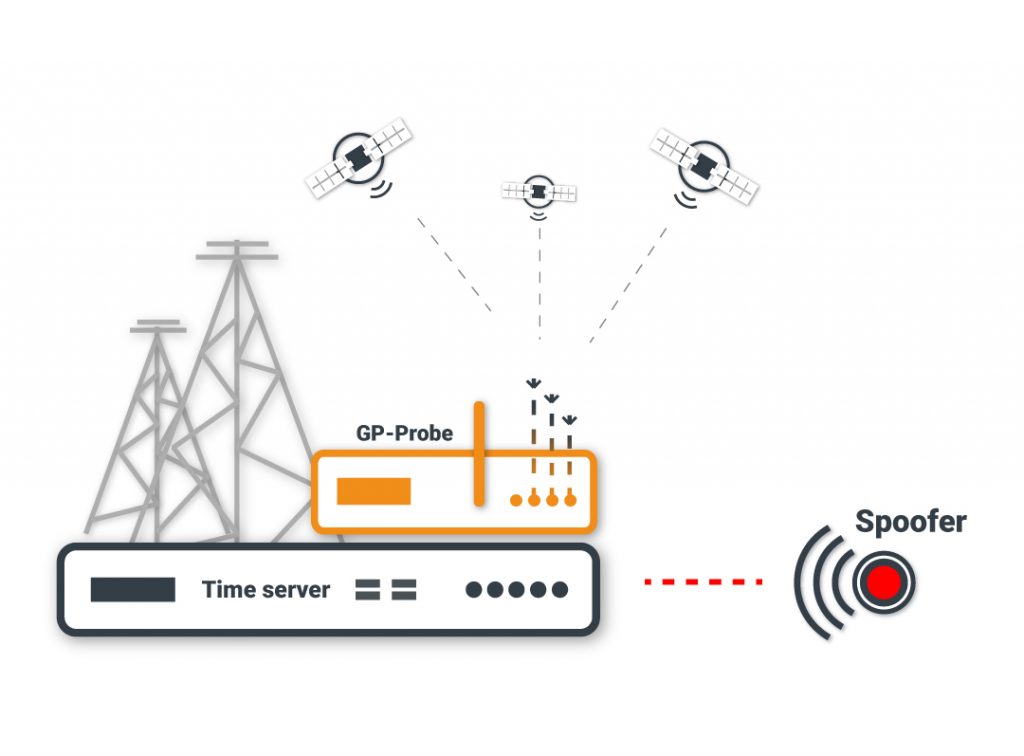
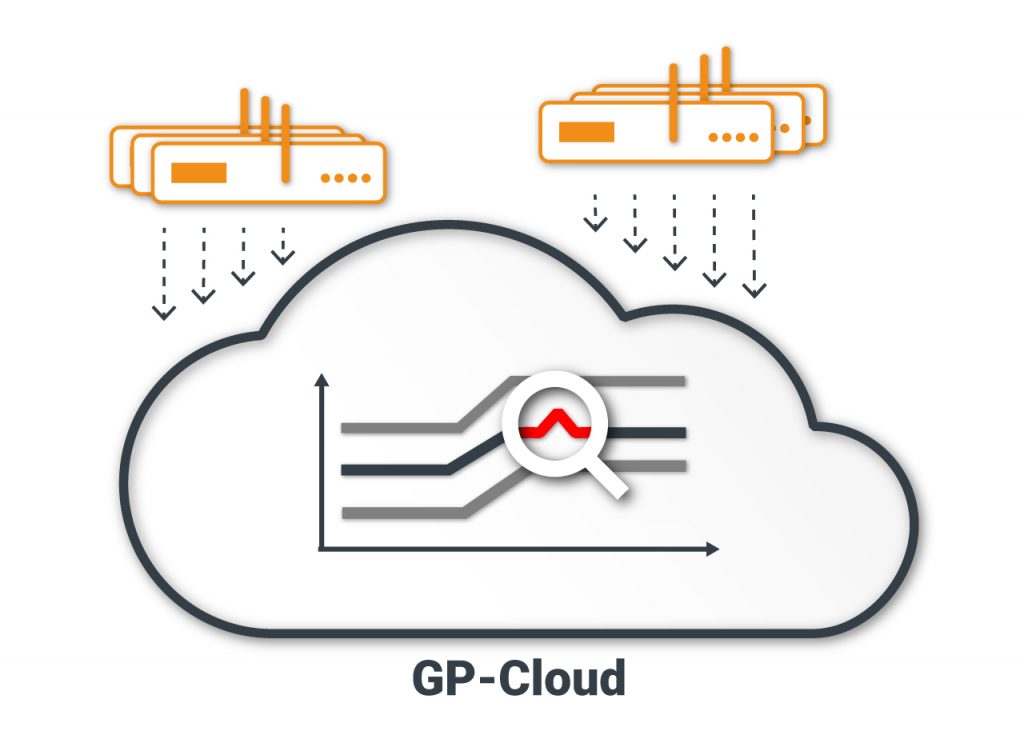
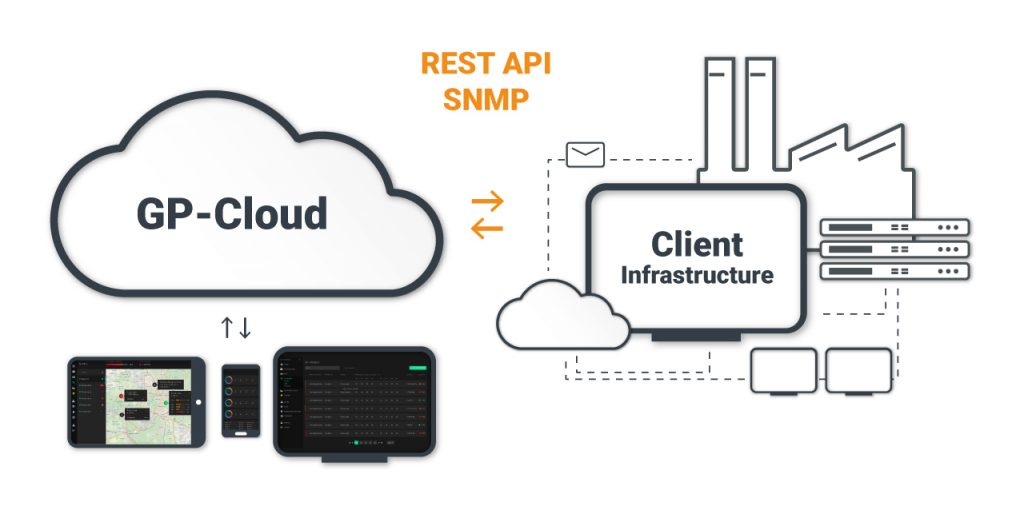
3. The GP-Cloud analyzes the received data, detects and classifies anomalies, and calculates the probability of spoofing, interference power, and time/coordinates accuracy.
4. The GP-Cloud interface allows users to monitor the navigation field status in real time. The GP-Cloud API integrates the app into existing systems.
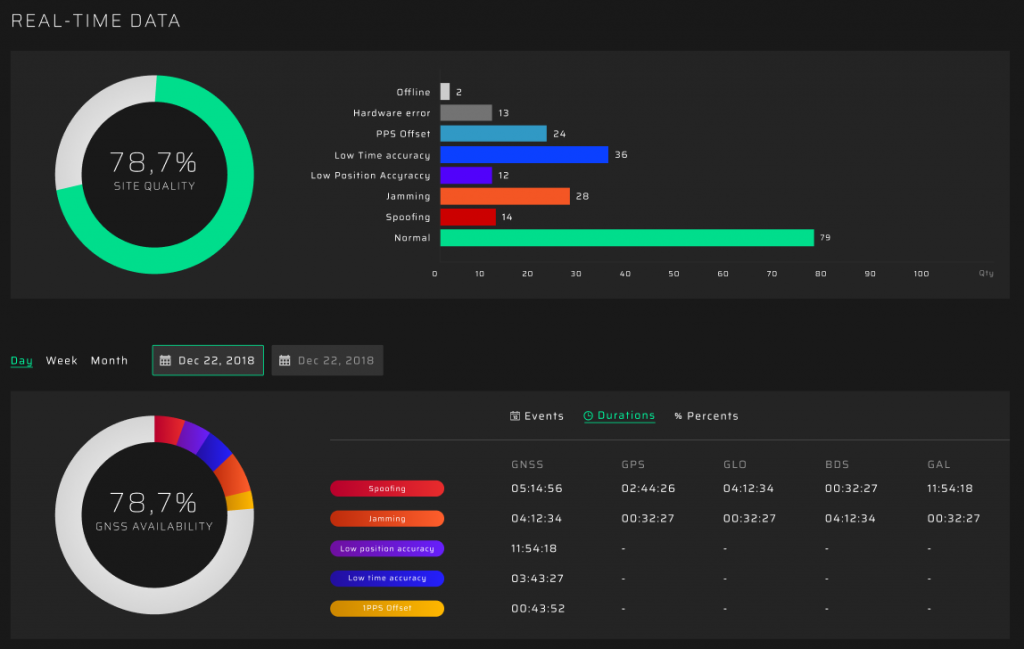
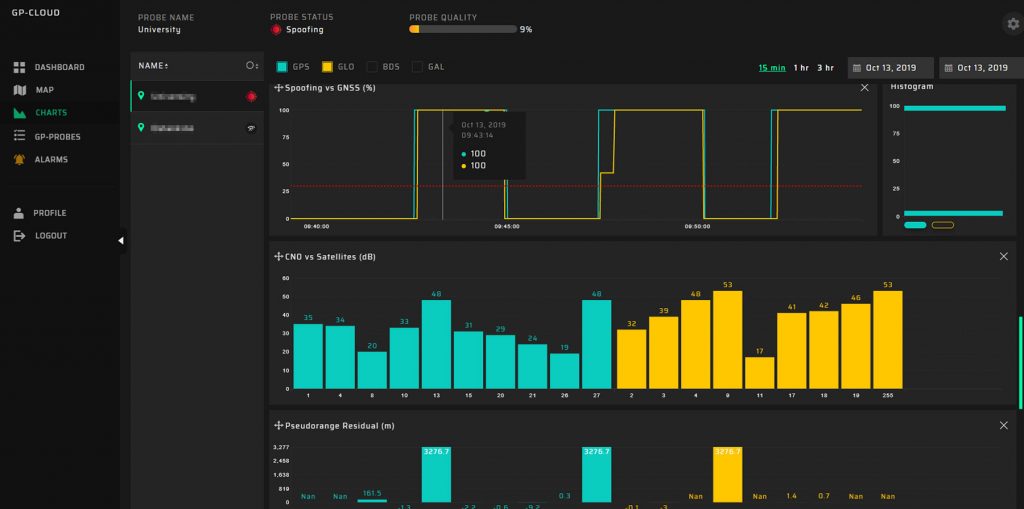
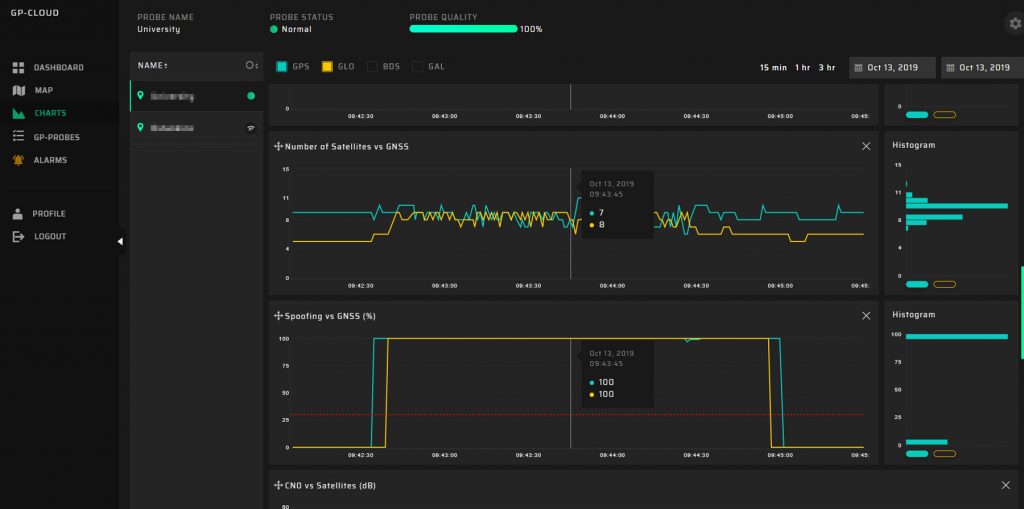
Dashboard for Spoofing and Jamming Analysis
The information is divided into two blocks on the dashboard:
- The current status of GP-Probes in real time
- Event statistics
The first block contains charts indicating the status of GP-Probes, detecting spoofing or jamming, and other GNSS parameters.
The second block displays information about the quantity and duration of registered events for a defined period.
All dashboard information is automatically updated in real time.
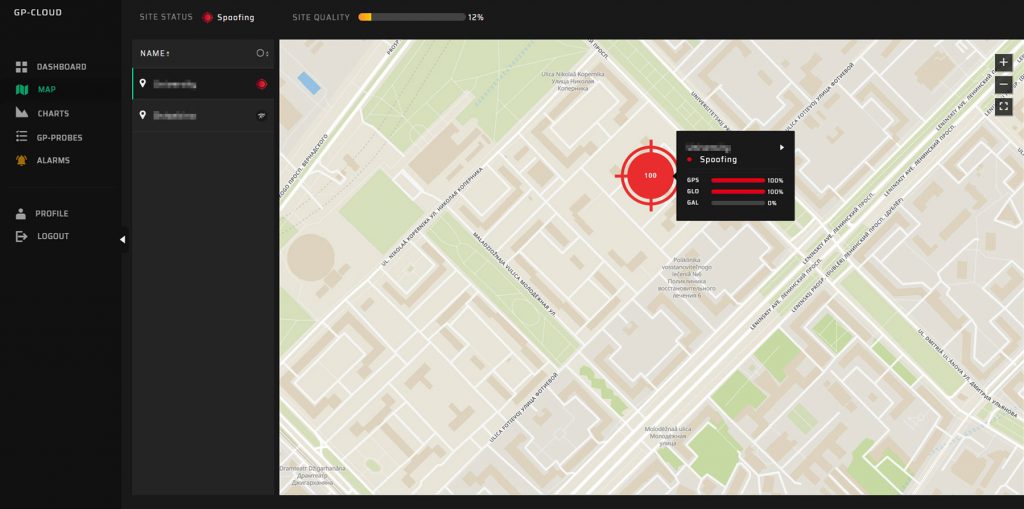
Map
The status of the navigation field is visible at all control points on the map. Different icons indicate the status of each GP-Probe.

Spoofing

Jamming
The numbers in the center of the icon disclose the probability of detecting the event. Click on any icon to get detailed status information and open the charts to perform in-depth scrutiny of all parameters.
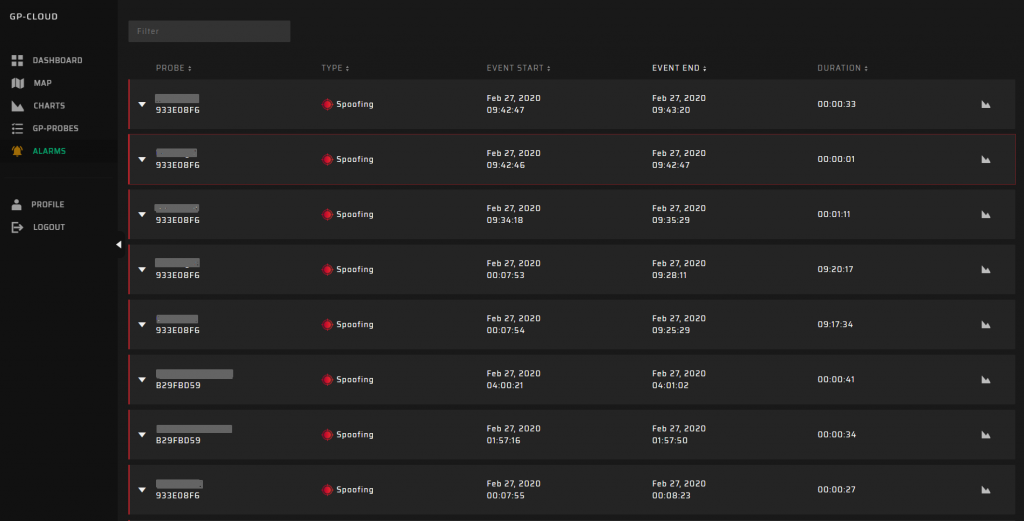
Alarms
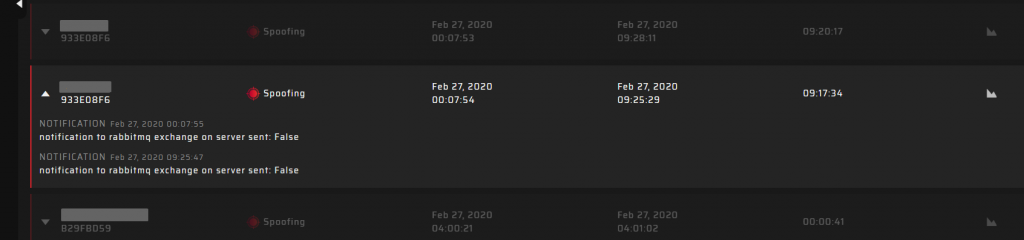
The GP-Cloud registers spoofing and jamming events and display it in the Alarms table. You can view the tabled list of accidents with comprehensive information about the type, start/end time, and duration of each event. You can also click the chart icon to obtain a detailed analysis.
GP-Cloud sends notifications when registering each accident according to system settings. All performed actions are available for analysis: