On October 25th, Maksim Barodzka, CEO of GPSPATRON, addressed the Time Appliances Project (TAP) on safeguarding time servers from GNSS spoofing. His presentation scrutinized various protective strategies, from sophisticated antenna systems to innovative data monitoring techniques. Key points included the limitations of conventional methods against advanced spoofing, the advantages of real-time anomaly detection in raw GNSS data, and the practical implications of GNSS vulnerabilities in today’s technology landscape. The insights provided by Barodzka highlighted the evolving nature of GNSS spoofing threats and the necessity for adaptive defenses in critical infrastructure.
Techniques to Safeguard Time Servers against GNSS Spoofing
Sophisticated Antenna Systems
There are two primary types of antenna systems for GNSS interference mitigation: Null Steering and Beamforming.
Null Steering
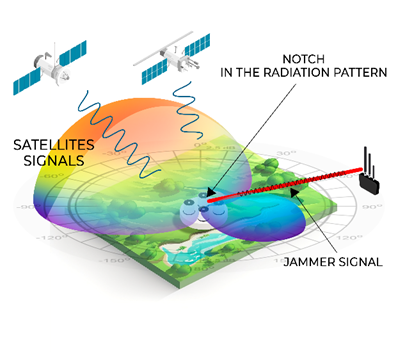
- Real efficiency starts at 4 antenna elements.
- 40-60 dB interference suppression level.
- Effective against jamming and partially against spoofing.
Beamforming
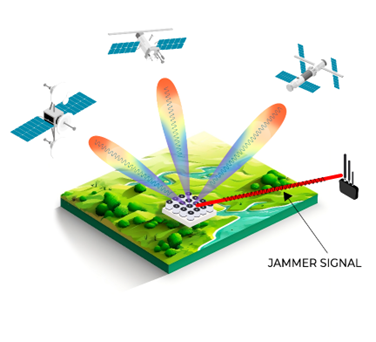
- Requires 8-16 antenna elements.
- High cost, large size and power consumption.
- Acceptable technique to counteract low-power GNSS spoofing.
Beamforming, on the other hand, is a more advanced and effective technique that requires a larger number of antenna elements. With Beamforming, narrow beams are formed and directed towards each satellite based on their calculated position. This method allows for more precise and targeted signal reception, improving the overall performance and accuracy of the GNSS receiver. However, it is worth mentioning that Beamforming antenna systems are more complex, expensive, and larger in size compared to Null Steering systems. These factors make Beamforming less suitable for widespread commercial infrastructure deployment.
Null Steering technology creates a null antenna pattern towards the source of interference. Using an antenna system with multiple elements (typically four), the technology can suppress interference from all directions by 40 to 60 decibels. However, note that Null Steering technology may be unsuitable for countering spoofing attacks where the power of the fake signal is below the system’s noise floor. In such cases, the fake signal may go undetected by the system.
While sophisticated antenna systems provide some protection against spoofing attacks, it’s important to understand their limits. All techniques can suppress no more than 60 dB of interference, enough to combat jamming but not spoofing. This is because the power of original signals is very low and easy to spoof.
In addition, antenna systems are very costly, subject to export controls, and may not be used for commercial infrastructure.
Synchronization Systems with Grandmaster Cross Monitoring
The concept behind this method is to have multiple grandmaster clocks that are distributed across different locations. These grandmasters continuously monitor and cross-check each other’s time signals to ensure synchronization accuracy. By implementing this cross-monitoring approach, any discrepancies or anomalies in the time signals can be quickly detected and flagged as potential spoofing attacks.
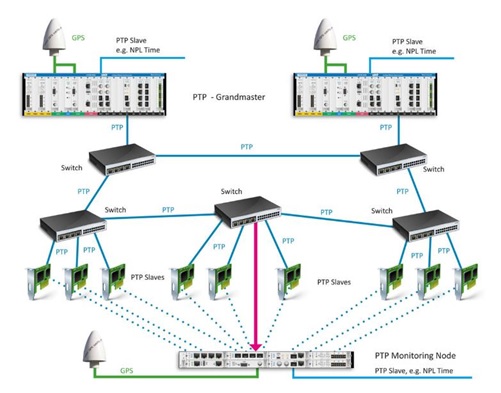
One advantage of this method is that it is relatively simple and requires little investment. Many companies utilize this approach because it provides a basic level of protection without significant additional costs. However, there are a couple of limitations to consider.
- Firstly, the detection in this method may happen after the grandmaster has already been successfully spoofed, and part of the synchronization system has already received incorrect data. This delay in detection reduces the effectiveness of the approach in preventing the impact of spoofing attacks.
- Secondly, if a powerful spoofing attack covers a large region, all the grandmasters within that region may be under the same attack. This means that the cross-monitoring system might not be able to differentiate between legitimate and spoofed signals, potentially affecting the accuracy of synchronization.
RAW GNSS Data Monitoring
If you have access to raw data coming from an embedded GNSS receiver, it becomes possible to detect anomalies caused by spoofing or jamming attacks. The main advantage of this approach is the early detection of anomalies before they can have any impact on the time server. By recognizing that something is not going as usual in the raw GNSS data, appropriate action can be taken to address the issue promptly.
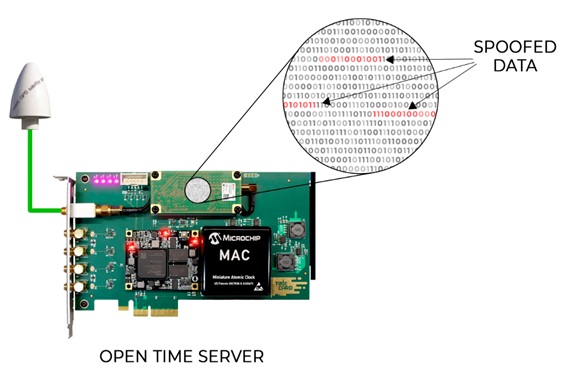
Another advantage is that this method can often be implemented as a software-only solution, without the need for additional hardware. This makes it a cost-effective approach for time server protection.
However, one requirement for this approach is access to the raw GNSS data. This can be easily achieved with an open-time server architecture.
GNSS Interference - Growing Threat
GNSS Spoofing in Anti-Drone Systems
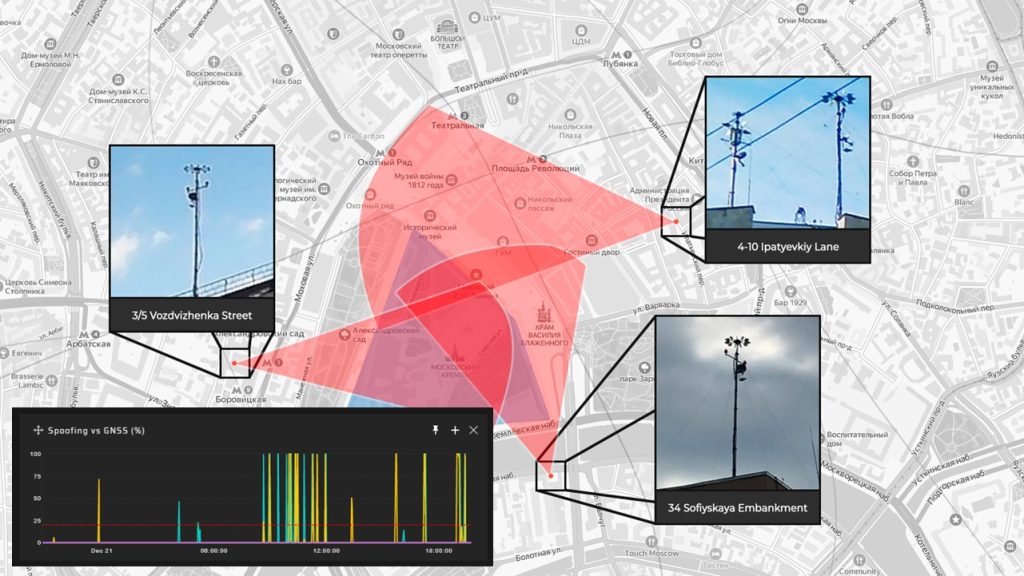
Over the past decade, the issue of GNSS spoofing has gained significant attention. The first mentions of GNSS spoofing were reported from Russia approximately 10 years ago. In major Russian cities, anti-drone systems utilizing GNSS spoofing were deployed, marking the beginning of the problem for civilian infrastructure in Russia.
Check out the detailed report released by the C4ADS team in 2018 on the use of GNS from poofing in Russia in Crimea and Syria – “ABOVE US ONLY STARS”
GNSS Spoofing to Bypass Sanctions
According to a New York Times investigation, shippers use GNSS spoofing to evade sanctions on Russian oil exports. The report said ships tamper with their tracking systems to mislead authorities.
Investigators analyzed data from the vessels’ tracking systems and satellite images, identifying several instances of deliberate spoofing that deceived the ships’ trackers.
Satellite photos showed the ships docked at Russian ports while their trackers simultaneously placed them at entirely different locations, according to the report. The full investigation can be found here: https://www.nytimes.com/interactive/2023/05/30/world/asia/russia-oil-ships-sanctions.html
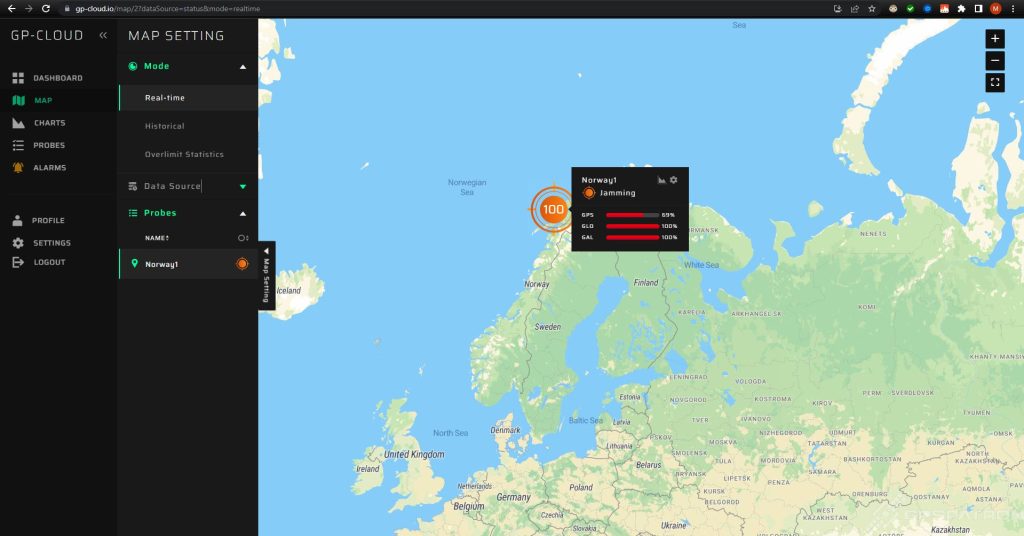
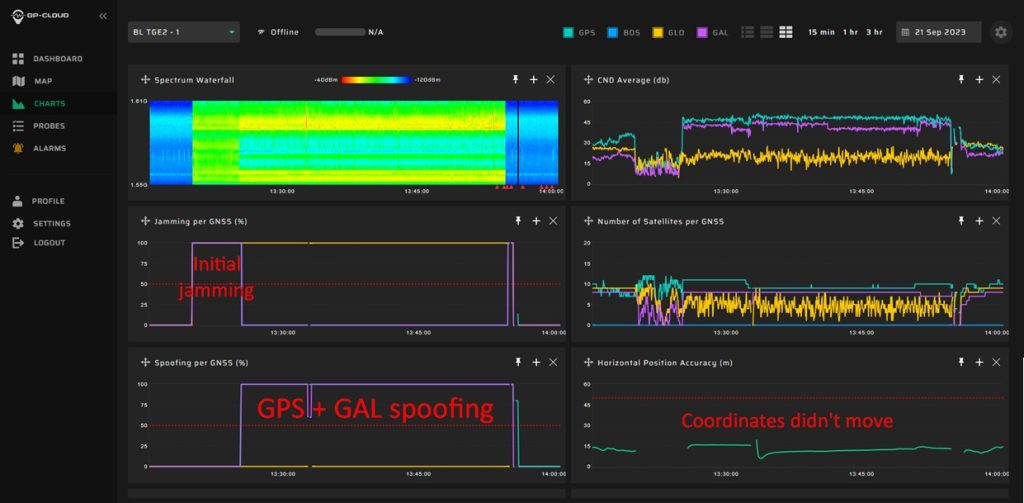
In May 2023, our system detected a long-term GNSS jamming in the north of Norway. Our GP-Probe TGE2 interference detector was installed in a remote region. The only likely source of such a powerful and prolonged interference was most likely a ship at sea.
It was a series of episodes of different durations:
This incident highlights how unintentional GNSS jamming can potentially impact critical infrastructure located near coastal regions.
GNSS Spoofing Impact on Aviation Traffic
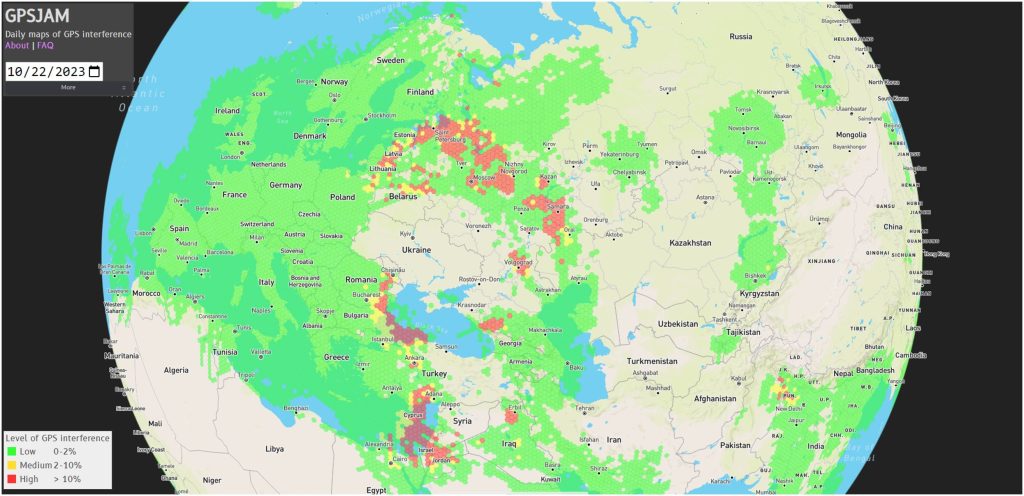
Data analysis from GPSjam.org has provided insight into the prevalence of GNSS interference using aircraft tracking system (ADS-B) data. The analysis revealed instances where aircraft experienced difficulties receiving GNSS signals, indicating powerful interference blocked GNSS signal reception:
The growing prevalence of GNSS spoofing can be attributed to various factors. The accessibility of affordable software-defined radio boards and the availability of open-source applications for GPS signal simulation have contributed to the ease of conducting spoofing attacks. Moreover, the relatively low cost and simplicity of carrying out such attacks have attracted interest and raised concerns about the security of GNSS systems.
In conclusion, GNSS interference, particularly in the form of spoofing, has become a growing threat in recent years. It has been observed in various contexts, including anti-drone systems, ship navigation, and even potentially for evading sanctions. Monitoring and detecting anomalies in GNSS data have become crucial for protecting critical infrastructure and ensuring the reliability of GNSS-based systems.
Types of GNSS Spoofing Scenarios
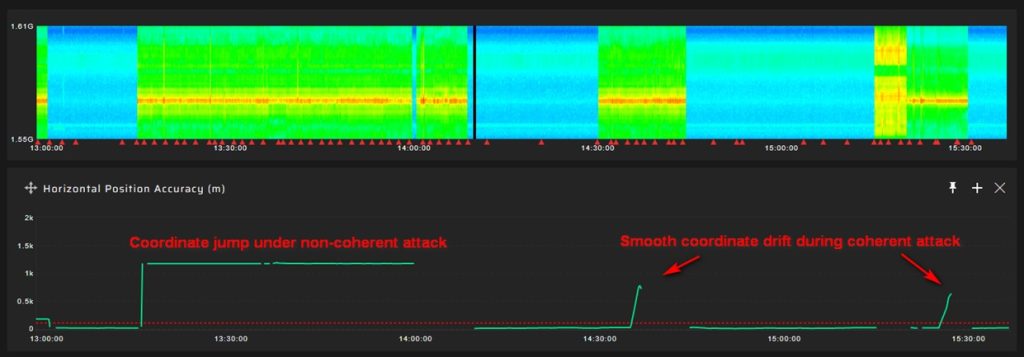
Non-Coherent GNSS Spoofing
In a non-coherent spoofing attack, the attacker generates a fake GNSS signal that is not synchronized with actual signals and contains incorrect information such as coordinates, datastream values, pseudo-ranges, Doppler, etc.
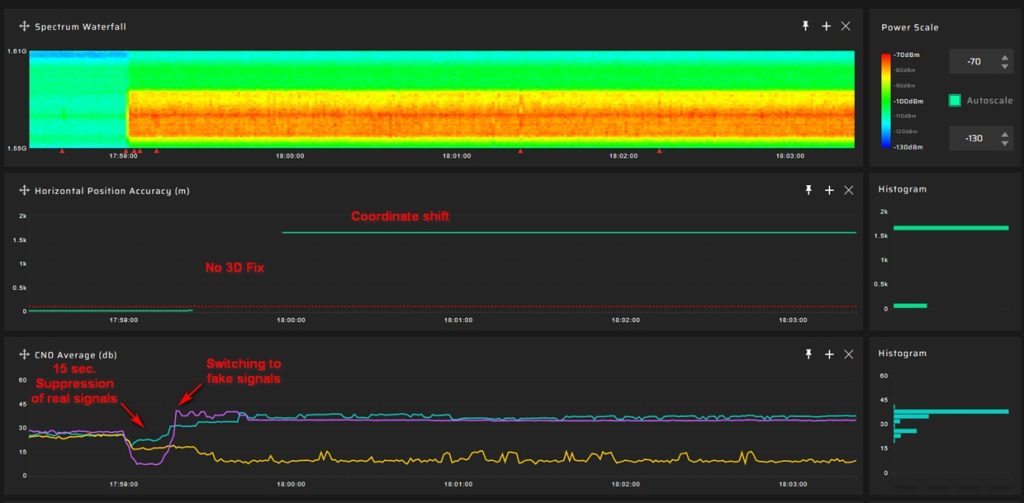
The attack occurs in several stages. First, the attacker suppresses genuine signals, causing the target receiver to enter search mode. After 15-30 seconds the receiver locks onto the fake signals.
Non-coherent spoofing attacks can be easily detected by monitoring anomalies in parameters like automatic gain control, coordinates, velocity, pseudorange residuals, signal-to-noise ratio, and others.
Coherent GNSS Spoofing
In a coherent spoofing attack, the attacker generates a fake GNSS signal that is entirely identical to the genuine signal in all parameters. This means that the fake signal perfectly mimics the real signal’s pseudoranges, Doppler, datasteram, and other characteristics.
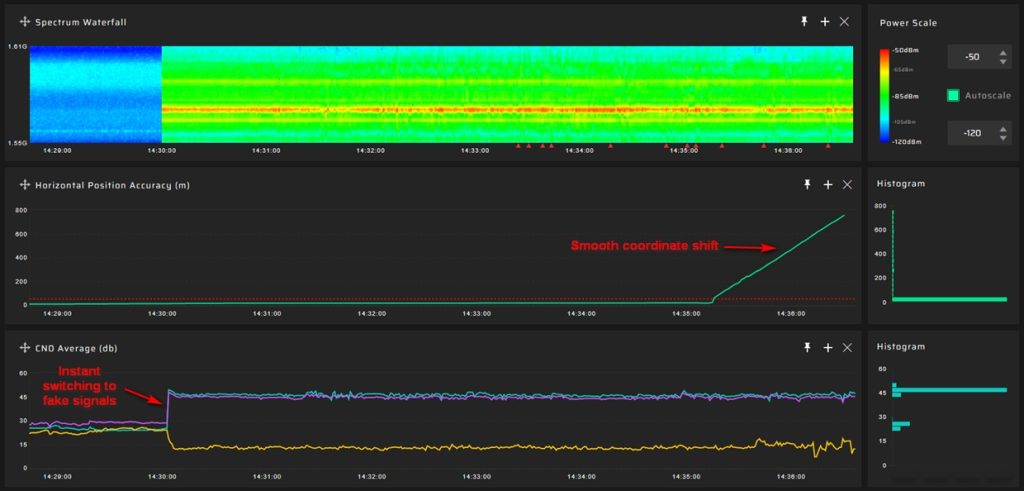
Unlike with non-coherent attacks, a target receiver immediately switches to a falsified signal. Then, the attacker can gradually manipulate the time or coordinate values, leading to a smooth drift in positioning or timing.
Detecting precisely executed coherent spoofing attacks is challenging due to the initial similarities between genuine and fake signals. Having only one GNSS antenna provides insufficient information to analyze. Anomaly monitoring techniques can help but only after an attacker has manipulated parameters.
Learn more about the types of GNSS spoofing in this awesome animation:
Data Available for Analysis
All GNSS receivers support NMEA format, but the data provided is limited. Access to proprietary binary data offers significantly more information to analyze. However, each GNSS chipset vendor uses different protocols. We’ll look at one of the most popular: UBX from U-blox.
NMEA
NMEA (National Marine Electronics Association) is a common data protocol used by GNSS receivers to output essential information in a human-readable format. This format includes parameters such as timestamp, coordinates, velocity, signal-to-noise ratio, and more. While NMEA provides basic data for analysis, it may not offer the full range of information needed to detect complex spoofing attacks.
Available data for anomaly detection:
- Timestamp
- Coordinates
- Velocity
- Signal to noise ratio
- Number of visible sats
UBX
UBX (u-blox proprietary binary data format) is a binary data format specific to u-blox GNSS receivers. It provides a more extensive set of data compared to NMEA. With UBX, you can access additional parameters such as gain, RF spectrum, residuals, datastream, and more. This format allows for detailed analysis, including monitoring power, pseudorange residuals, and even validating datastream.
Available data for anomaly detection:
- Gain
- RF Spectrum
- Residuals
- Pseudorange
- Doppler
- Carrier Phase & Lock Time
- Datastream
Anomaly Detection Algorithms
Coordinate Monitoring
This method involves tracking and analyzing the changes in coordinates provided by the GNSS receiver. The advantages of coordinate monitoring lie in its simplicity. By comparing the reference coordinates with the coordinates obtained from the GNSS module, any discrepancies or abnormal shifts can be identified as potential signs of spoofing. This straightforward algorithm allows for easy implementation and detection of spoofing attacks.
However, there are certain limitations to coordinate monitoring. One major drawback is that it may only detect spoofing after the receiver has already been successfully spoofed. This means that the detection is reactive rather than proactive:
An attacker can easily simulate the coordinates of your GNSS receiver. It is possible to manipulate only the time component, making it undetectable through coordinate monitoring alone:
Check out our video to learn about the manipulation of the PPS phase in time servers through coherent spoofing:
CN0 Monitoring
This method involves monitoring the average signal-to-noise ratio (CN0) provided by the GNSS receiver for each satellite.
The advantage of CN0 Average Monitoring lies in its ability to detect spoofing attacks at an early stage. By setting a threshold above the average CN0 level, any significant increase in the CN0 value can indicate the presence of a spoofing attack. This method is relatively simple to implement and can provide timely alerts for potential spoofing incidents.
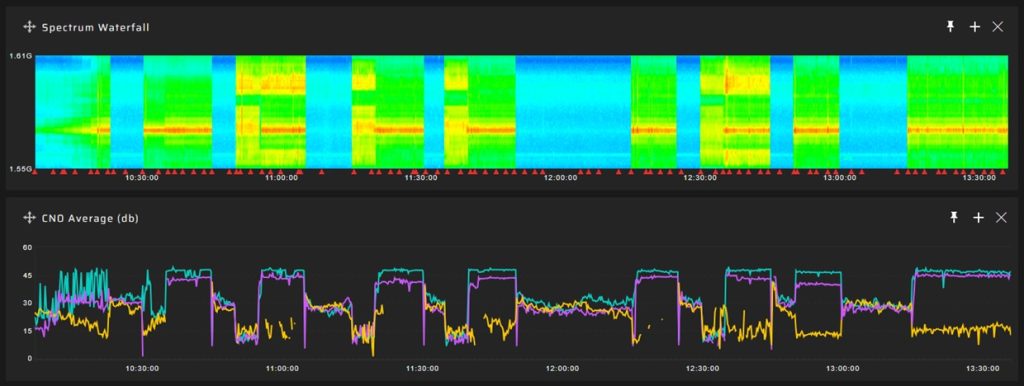
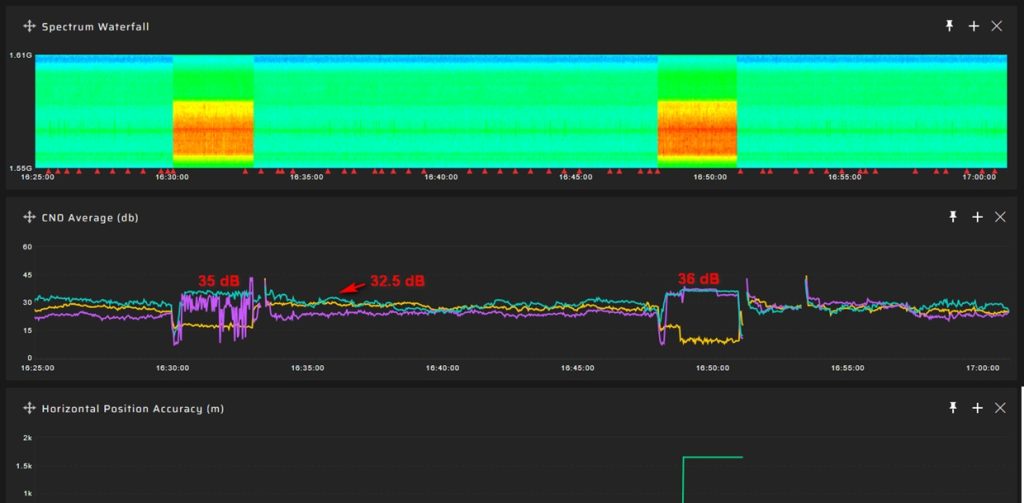
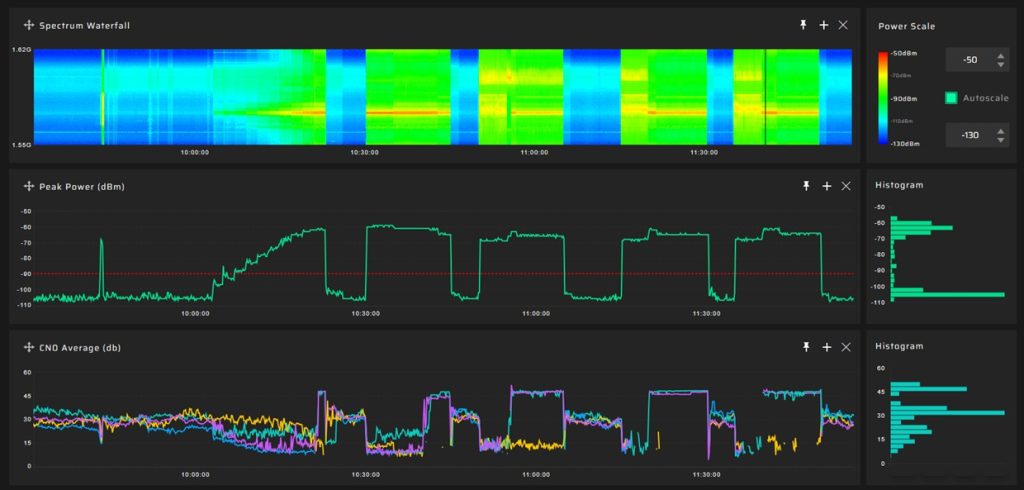
In the screenshot below you can see multiple spoofing episodes when the average value of the signal-to-noise ratio increased significantly. And in this case there is no problem with setting the detection threshold:
Disadvantages of CN0 Monitoring for detecting GNSS spoofing, include:
- A GNSS generator can simulate any signal-to-noise ratio value, making it challenging to distinguish between authentic and spoofed signals.
- Setting thresholds for detecting low-power spoofing is complex, especially when trying to balance this with an acceptable rate of false alarms.
- The average value of the signal-to-noise ratio varies widely throughout the day even without any interference, which complicates the process of setting a threshold.
The screenshot below shows two episodes of low-power spoofing. The signal-to-noise ratio increased insignificantly, about 4-5 dB above the average level. It is difficult to set a detection threshold for this case. Because it is necessary to avoid false alarms.
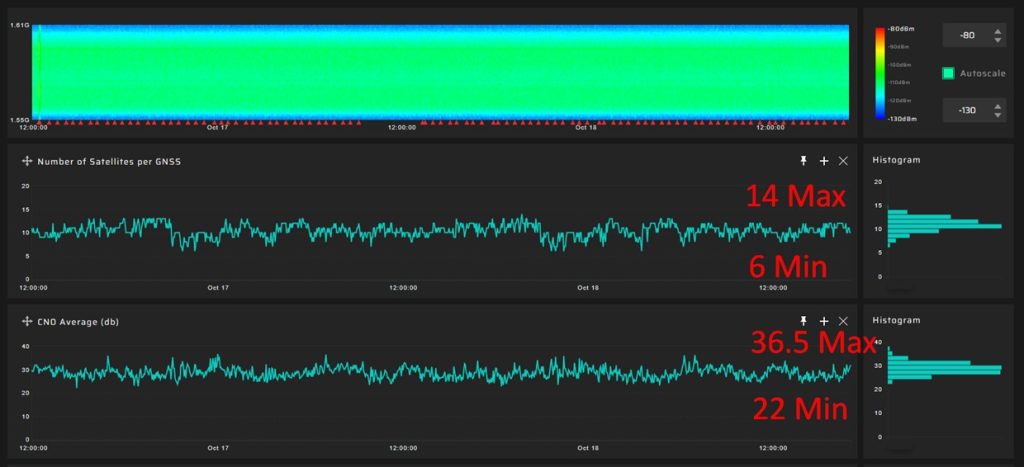
Here is an example of CN0 fluctuation in a day for GPS:
The variation in CN0 is significant throughout the day, indicating that setting a basic threshold would primarily be effective in identifying only high-power interference.
Residuals Monitoring
The Pseudorange Residuals Monitoring method for detecting GNSS spoofing is based on the difference between the estimated range to satellites and the measured pseudoranges. In a non-coherent attack, where pseudoranges differ greatly from actual values, this method reveals large residuals, indicating spoofing.
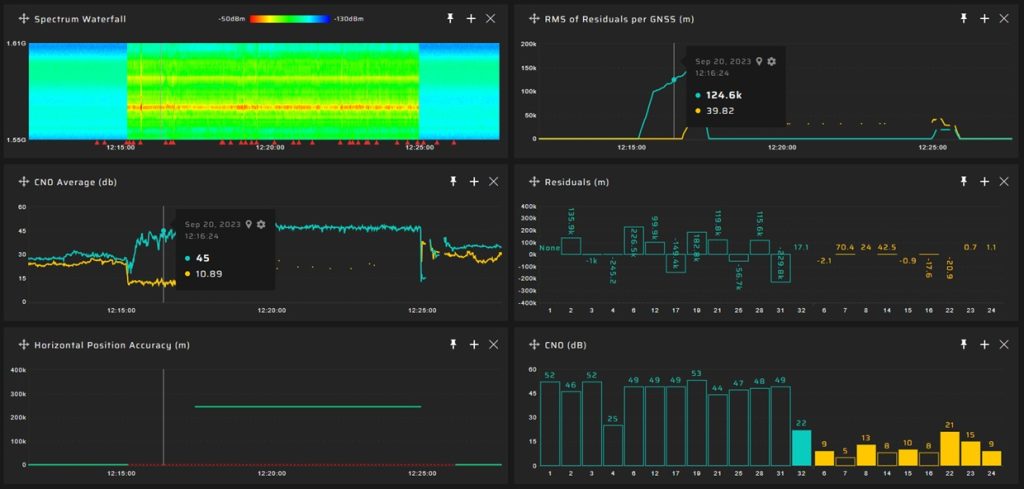
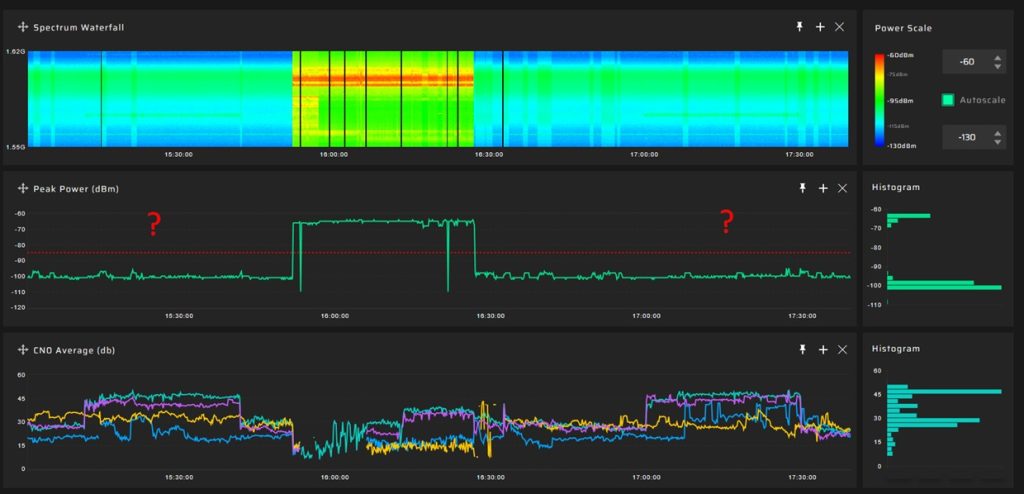
The screenshot below is an illustration of a non-coherent GNSS spoofing attack, identifiable by the substantial pseudorange residuals. These large residuals can be observed and detected prior to the GNSS receiver beginning to yield incorrect positional coordinates, thereby serving as an early warning indicator of such an attack.
Under certain non-coherent spoofing scenarios, the residuals can spike to extreme levels, even up to a million meters, making detection straightforward. However, in other scenarios, the values may increase modestly, only by a few hundred meters. This subtlety poses a challenge in setting effective detection thresholds, as similar residual patterns could result from signal reflections, especially in urban environments with high-rise buildings.
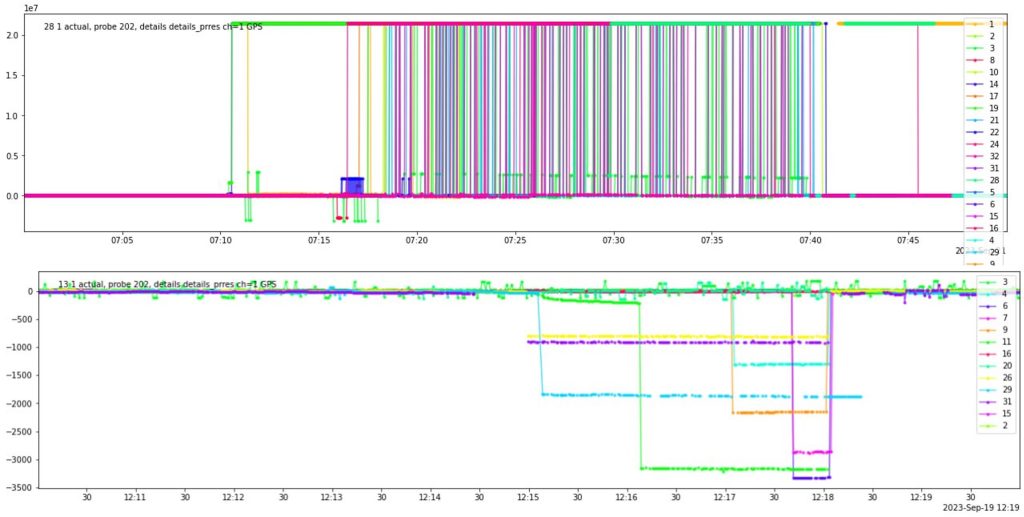
In the image, the residuals for each satellite can be seen under two non-coherent attacks. The residuals have significantly increased in the upper graph and slightly in the lower one:
Disadvantages of the residuals monitoring algorithm:
- Limitation in Detecting Coherent Attacks: Indeed, the residuals monitoring algorithm is primarily effective for non-coherent attacks. In cases of coherent spoofing, the residuals are often close to zero, making them indistinguishable from normal conditions. This necessitates alternative strategies for detecting coherent attacks.
- Challenges in Urban Environments: In urban settings, where tall buildings are prevalent, GNSS signals often reflect off these structures. This phenomenon, known as multipath, can create residual patterns similar to those observed in spoofing scenarios, complicating the detection process and potentially leading to false positives.
Spectrum, Power & Gain Monitoring
Spectrum, power, and gain monitoring are essential components in the detection of GNSS spoofing. Some GNSS receivers have the capability to report preamplifier gain, provide spectrum data, and even offer raw IQ data. This information can be instrumental in identifying interference of high-power events:
The screenshot below illustrates three different GNSS spoofing events, differentiated by their signal power. The central event is powerful and easily detectable due to its strength, while the two flanking events are weak, making them unnoticeable for power monitoring:
DataStream Authentication
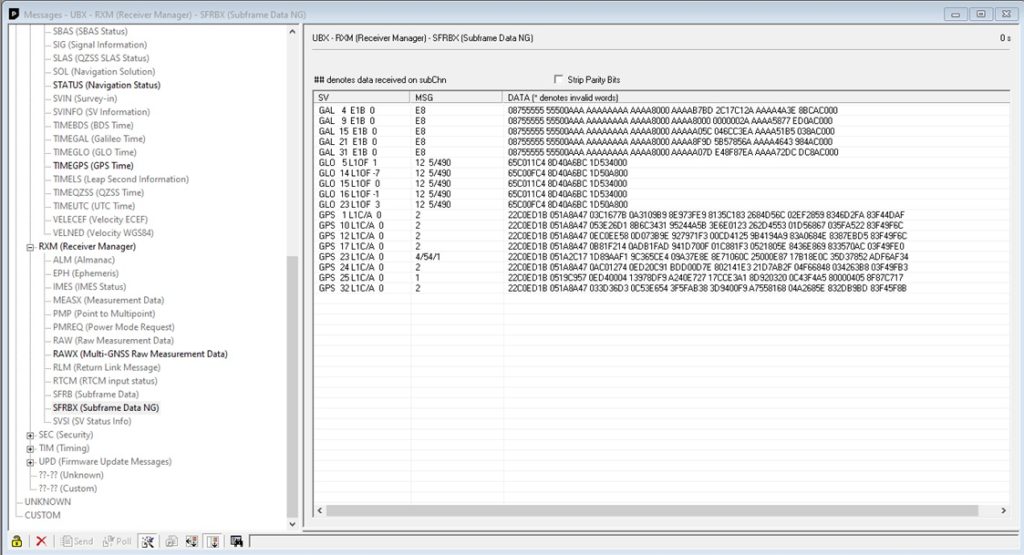
DataStream Authentication is a crucial aspect for ensuring the integrity GNSS signals. U-blox receivers can transmit raw binary data coming from satellites:
By harnessing this raw data, it becomes feasible to implement straightforward validation techniques for each data type. For instance, users can compare the ephemerides obtained from their GNSS receivers with the authentic ephemerides available from reliable sources such as NASA’s website. This comparison is a practical approach to authenticate the data’s legitimacy.
Monitoring the timestamp from satellites is another relatively simple yet effective measure. By regularly checking the consistency of the timestamp against a known standard, any discrepancies or anomalies that might suggest spoofing. This practice enhances the reliability and security of navigation and timing solutions provided by GNSS receivers.
The GPSPATRON Approach to Anomaly Detection in Raw GNSS Data for Anti-Spoofing Defense
As you may have realized from the article, implementing anomaly monitoring based on just one of the parameters mentioned will protect you only against the most aggressive spoofing attacks.
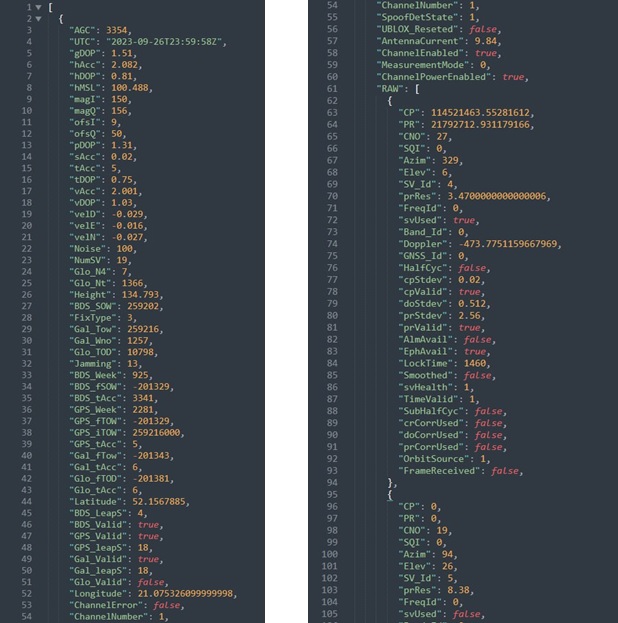
In our solutions, we interpret this data as a series of correlated time-series data, which opens up far more analytical opportunities. We analyze a much broader scope of data provided by the GNSS module:
The concept of anomaly detection in raw observations is realized in our new device GP-Probe DIN L1:
The device cannot differentiate between GNSS spoofing and jamming as effectively as its advanced counterpart, the GP-Probe TGE2. Nonetheless, it is capable of identifying anomalies caused by sophisticated spoofing attacks, as demonstrated during JammerTest 2023.
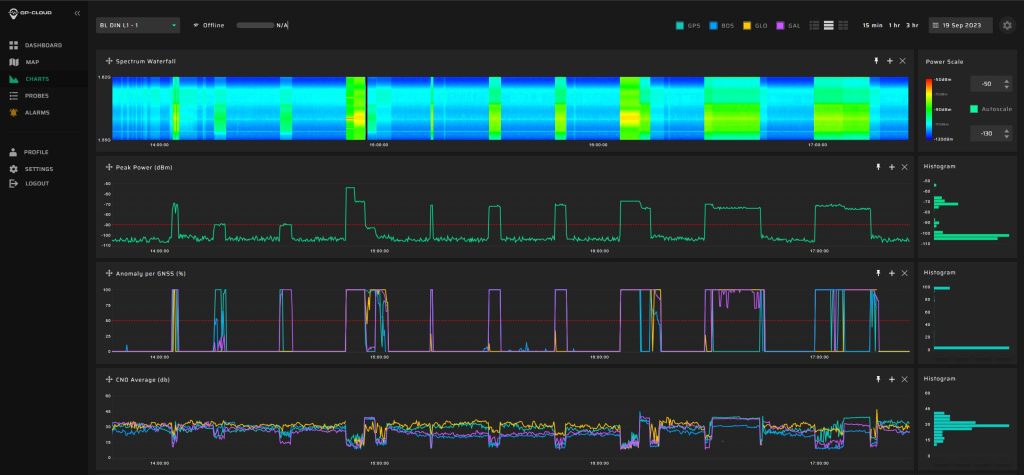
In the screenshot below, you can see the successful detection of multiple complex GNSS spoofing scenarios, including low-power meaconing attacks:
Book a Demo
Witness firsthand how GPSPATRON tackles various GNSS interferences including complex modulation jamming, non-coherent and coherent spoofing. Don’t miss this opportunity to see cutting-edge technology in action!