To write this article I was inspired by the strong opinion of some GNSS specialists that spoofing is not dangerous for RTK base stations, as the existing control systems can easily detect it.
If the RTK base station is affected by interference or intentional jamming, this becomes obvious as satellite tracking is lost. But what transpires in the case of non-coherent spoofing?
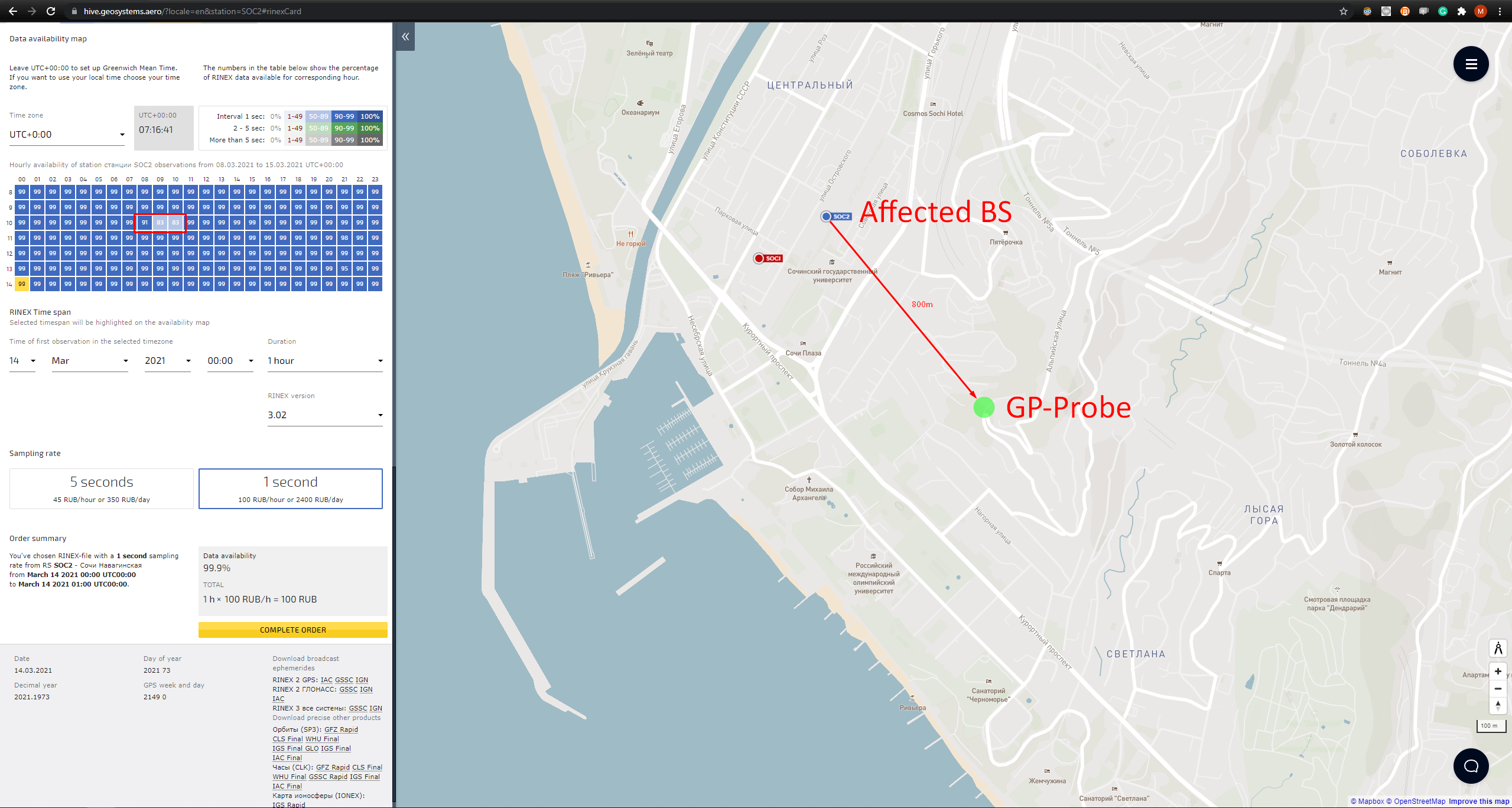
According to our measurements, Russia is the region with the most frequent use of GNSS spoofing as a counter-drone measure. A while ago, we had a test zone on the Black Sea coast. One of the probes was installed near the GNSS base station, which is called SOC2. Data provided by the hive.geosystems.aero system:
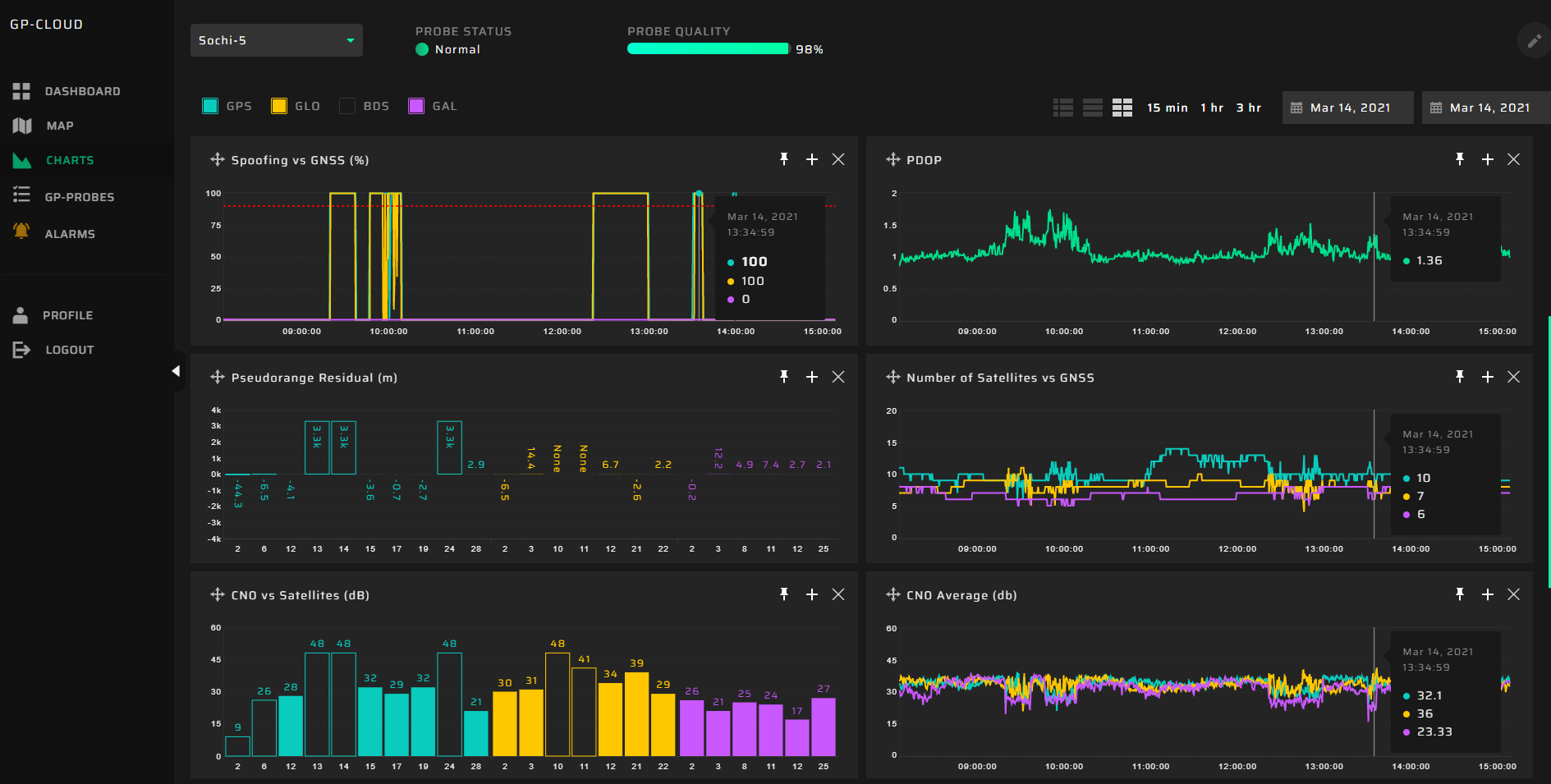
The measurements were taken on March 14, 2021. The probe detected 4 episodes of non-coherent spoofing. In most cases of non-coherent spoofing, the wrong coordinates are simulated, and the fake signal has significant differences in code phase and Doppler. Follow this link to learn about coherent and non-coherent spoofing.
In the screenshot above note the huge pseudorange residual for some satellites. This indicates a non-coherent attack.
Registered incidents:
| From (UTC) | To (UTC) | Duration |
| 06:20 | 06:37 | 17 minutes |
| 06:48 | 07:09 | 21 minutes |
| 09:22 | 10:00 | 38 minutes |
| 10:31 | 10:37 | 6 minutes |
We calculated the affected hours and compared it with hive.geosystems.aero system data:
| Hourly availability of station observations | ||
| Hour | GPSPATRON data | hive.geosystems.aero data |
| 06 | 51.6% | 99% |
| 07 | 85% | 99% |
| 08 | 100% | 91% |
| 09 | 36% | 83% |
| 10 | 90% | 83% |
As outlined, the data provided by GPSPATRON and NTRIP management software differ.
How We Can Prove Our Results
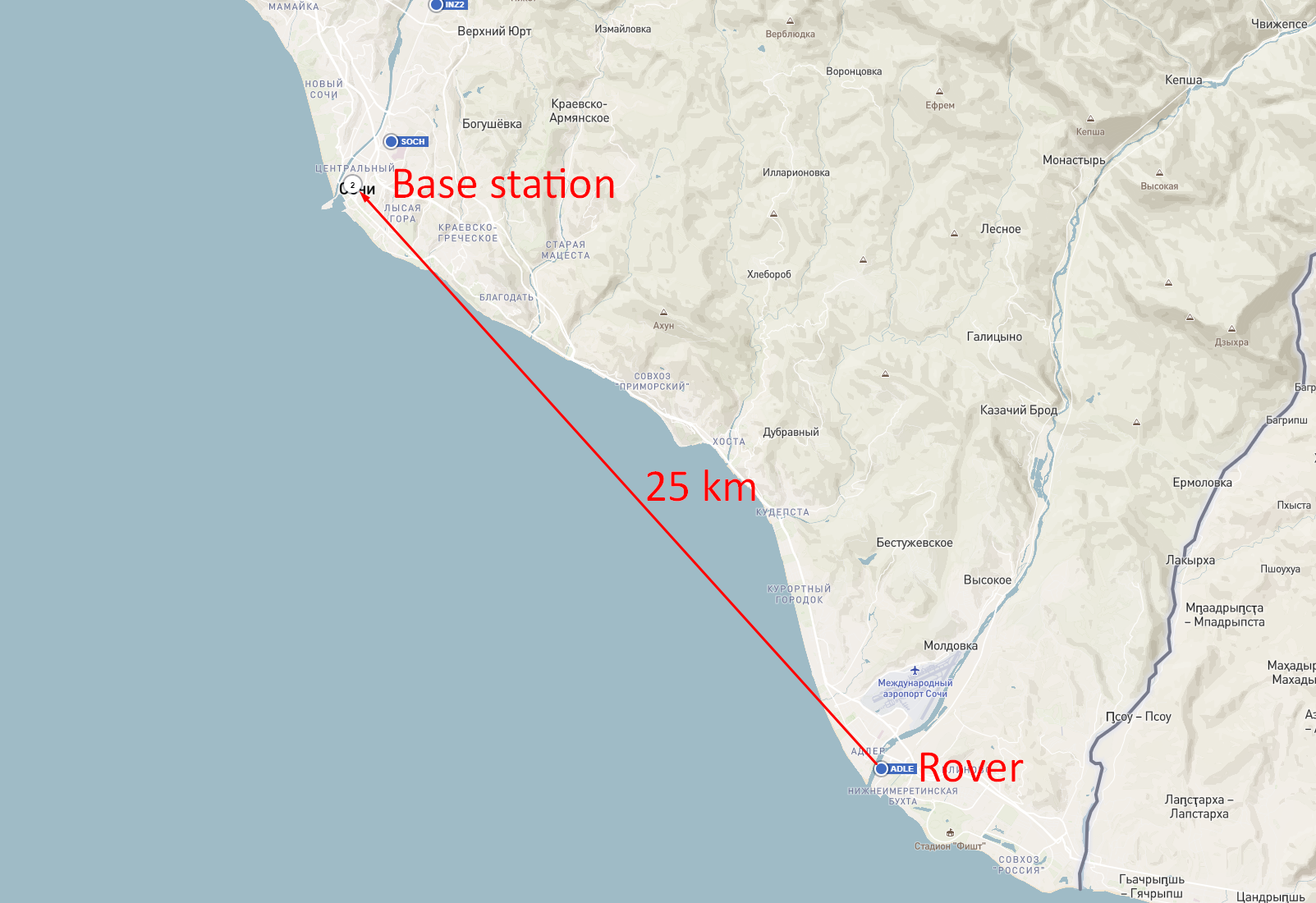
We downloaded the RINEX files of the affected base station and the station that is 25 km away:
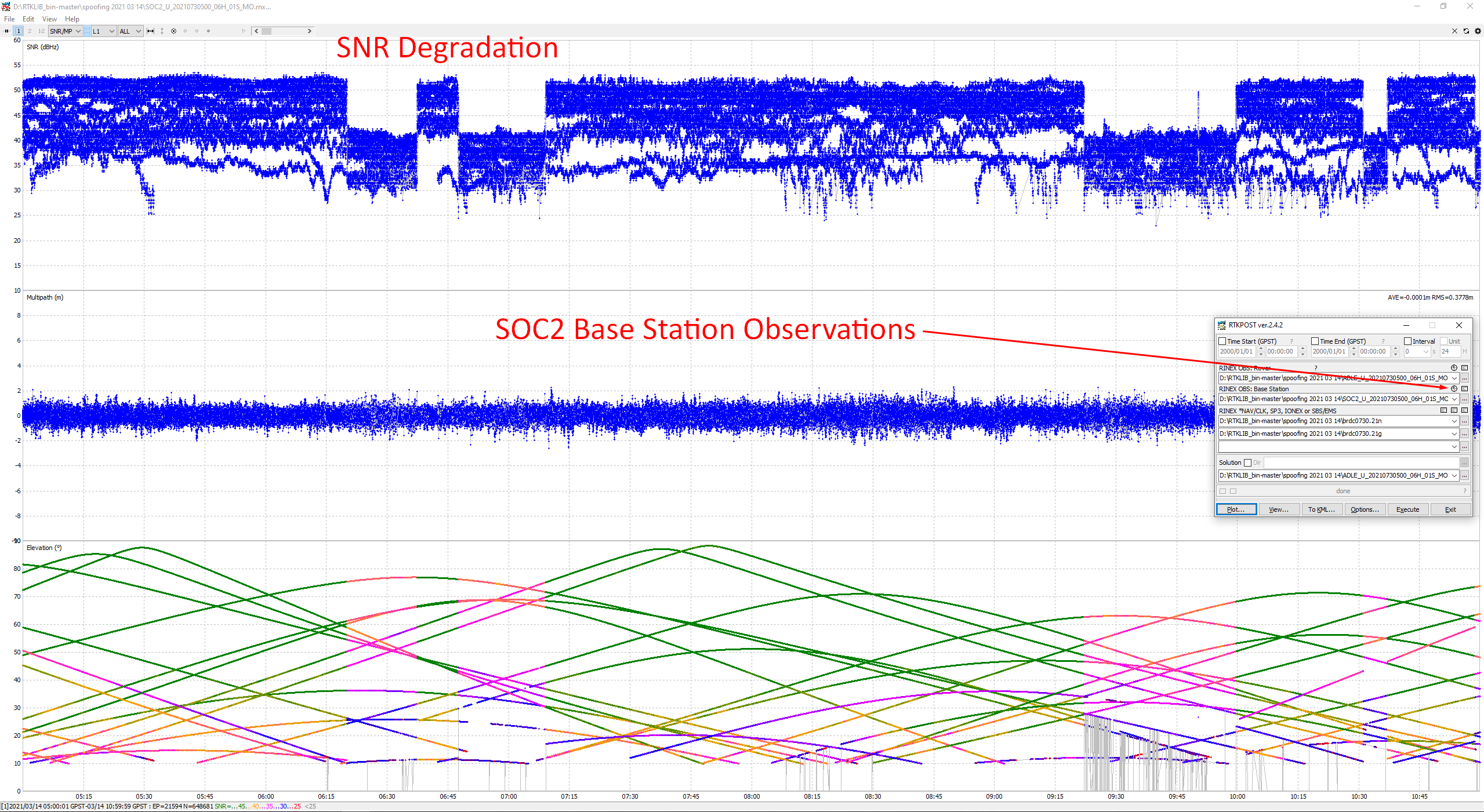
Then we processed the files in RTKLIB. In the following picture a significant degradation of SNR of the base station during the spoofing is observed:
The moments of SNR degradation match the spoofing events from the GPSPATRON system.
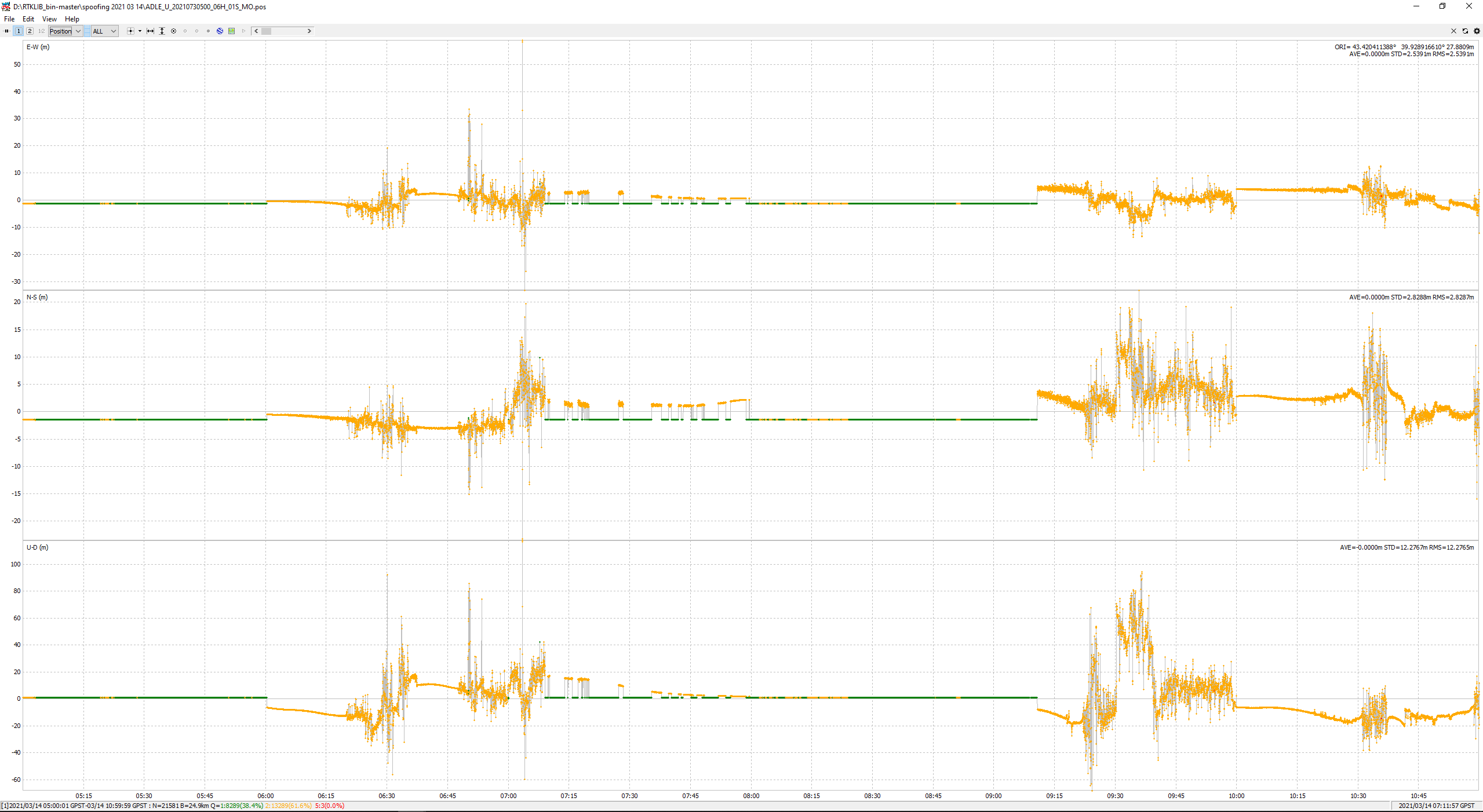
Now let’s solve the navigation task for the rover:
Notice that during the spoofing the navigation solution does not converge and the derived coordinates have a significant error.
Conclusions
- NTRIP caster software only monitors the measurements availability and does not control their quality. It is suitable for monitoring jamming, but it is not applicable for detecting even a basic spoofing scenario. We are confident that this conclusion is true not only for the HIVE system, but also for other NTRIP management applications.
- When post-processing, non-coherent spoofing is evident and not likely to be dangerous. Although, if you’ve spent a lot of time and collected data at a remote location, and then you see in the office that the base station had bad data during observation, it will be frustrating.
- For autonomous machines using Real-Time Kinematic positioning (RTK), even unintentional non-coherent spoofing can be an issue. All consumers connected to the affected base station will diminish positioning accuracy. This can be risky for numerous applications.
GPSPATRON Solution
We provide two options for protection:
- With GP-Probe
- Base Station raw GNSS data analysis
GP-Probe
We can install GP-Probe near protected GNSS base station. If an incident is registered, GP-Cloud will classify the interference as spoofing or jamming, determine which GNSS is affected (GPS, GLONASS, BeiDou, Galileo), and send a real-time alert to customers. The users can stop their operation or switch to an alternative base station.
Pros
- Guaranteed detection of deliberate coherent spoofing attack
- Interference classification
Cons
- Installation of additional equipment is required (GP-Probe)
Raw GNSS Data Analysis
The GP-Cloud supports 1-Hz GNSS data from GNSS base stations over RTCM\NTRIP. Using neural network, GP-Cloud detects anomalies and sends a real-time alert.
Pros
- No additional equipment is required
Cons
- It is not possible to classify interference into spoofing and jamming.
- Unable to detect a deliberate coherent attack