In the previous article, we described some of the open-source projects for GPS signal simulation which exist. In this article, we explain possible attack scenarios with SDR, a server response to spoofing, and how to detect spoofing and mitigate the effects. We are not using expensive GNSS signal simulators (Spirent, Orolia, Rohde & Schwarz) or electronic warfare. We are reviewing what attack scenarios can be run with just a $1,000!
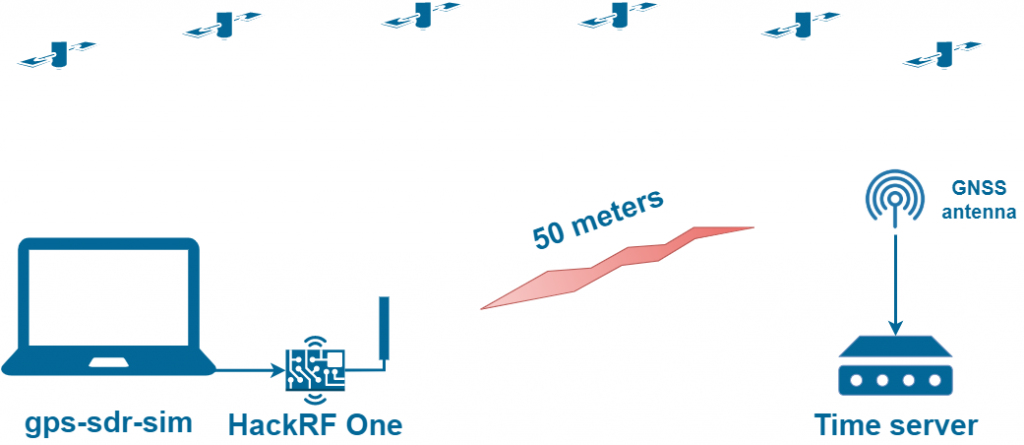
GPS Spoofing with HackRF One
This setup generates GPS signals only. If your receiver supports GLONASS and BeiDou, such spoofing is not a problem. Galileo signal reception will not save you because Galileo and the GPS share the same radio band. And a fake GPS signal will block reception of Galileo signals.
But sometimes the fake GPS signal power is so high that it overloads the input channel of the GNSS receiver, and it can no longer perceive GLONASS and Beidou.
| Attack cost | Depends on the SDR being used:
|
| Attack time | From 15 seconds to 5 minutes.
It depends on the embedded algorithms of LO tuning. We have repeatedly observed cases where an LO was realigned to a fake GPS signal in just 15 seconds after an attack started. Check out this video: https://youtu.be/si7Y5hx_ZA0. |
| Time server behavior | If the spoofer signal is strong enough, the time server GNSS receiver loses the original signals, stops providing a navigation solution, and goes into search mode. The time server indicates an error and goes into holdover mode. In about 10-30 seconds, the GNSS receiver finds the fake signals and indicates the erroneous data. The time server aligns the built-in reference oscillator according to fake GNSS signals. |
| Attack distance | 50 meters (approximate figure).
It strongly depends on signal propagation conditions. HackRF One RMS output power level for GNSS signals is about -10 dBm. This is enough to overpower the real signals within a radius of 5 km in line of sight. So why did we specify only 50 meters? In this scenario, the SDR generates an asynchronous signal, which the GNSS receiver perceives as noise/interference because the GNSS receiver is locked only to real signals. The high power of the spoofer here is needed to completely block the reception of the original signals to force the receiver into search mode. At a distance of 50 meters, the spoofer signal power is 40 dB higher than the original signals. This overloads the first preamplifier of the GNSS receiver, making the genuine signal become lost. Therefore, high power is needed only in the first seconds of the attack. |
| Protection | Protecting a time server is easy. You can use any modern GNSS receiver that supports Glonass, Galileo, Beidou. The GNSS receiver will automatically exclude false GPS signals from the calculation of the navigation solution due to large pseudorange/doppler errors compared to other systems. |
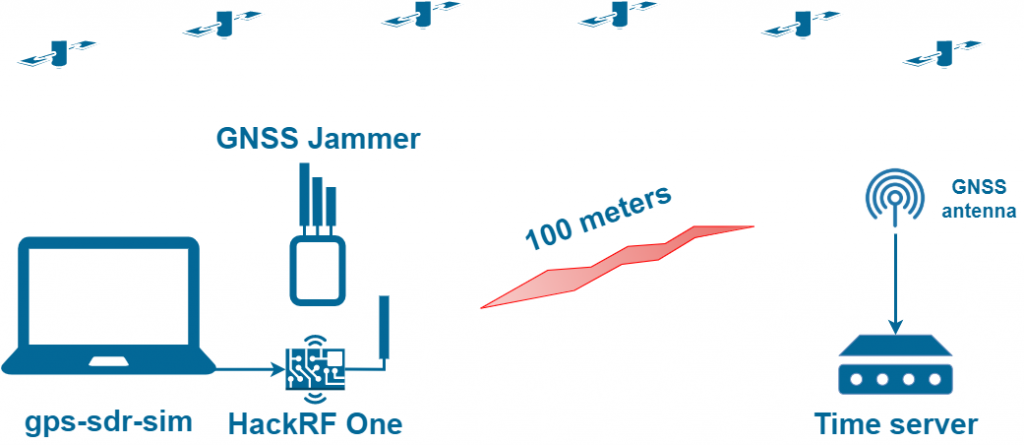
GNSS Spoofing with HackRF One and Jammer
For a guaranteed spoofing of multi-constellation GNSS receivers, it is only necessary to add a GNSS jammer. Which reliably jams the reception of GLONASS and BeiDou signals. You just need to adjust the power of the GNSS jammer and the GPS spoofer. So that only real signals are jammed, and the fake GPS signal is received.
| Attack cost | 320 USD for HackRF One and 150 USD for GNSS jammer |
| Attack time | same as in the first case |
| Time server behavior | same as in the first case |
| Attack distance | 100 meters.
The attack range can be slightly greater than in the first case, as a GNSS jammer can be used to disrupt the tracking of the original signals. This attack is more challenging to perform since it is necessary to adjust the output power of the spoofer and jammer so that the original signals would be suppressed and the fake GPS would not. Check out this video: https://youtu.be/Ya_B7tqA-X8. |
| Protection | Protecting a time server is not easy. Almost all GNSS receivers available on the market cannot resist this attack. What algorithms for protection can be implemented at the time server level?
1. SNR MonitoringIt is very easy to monitor the average SNR value and disable the GNSS receiver if the value has become unrealistically high. Nevertheless, according to our observations, in most real cases of spoofing, the SNR value decreases in the case of non-coherent attacks. In addition, there is no problem in lowering the SNR when generating a fake signal. 2. Coordinates MonitoringYou can disable the GNSS receiver if there is a significant shift in coordinates. The top two methods are really bad in the case of time servers, and by the time you notice a change in coordinates or SNR, it will be too late. The time server’s reference generator would already start adjusting to the fake signal and ultimately provide you with the wrong time. 3. PPS Phase MonitoringSince each time server has a perfect local oscillator, it is possible to compare the PPS phases from the GNSS receiver and the LO every second. In the case of a spike, you can instantly disable the sync signal. Implementation Problems
System-level ProtectionThe best protection method can be implemented when you have several time servers distributed in space. If one of the time servers starts producing an invalid timestamp, you can easily disable it. The method’s performance depends on the quality of the network (the accuracy of synchronization through the PTP) and the number of time servers. But there are also disadvantages. In the first seconds of spoofing, when the time server just begins generating the wrong time, the critical infrastructure that uses that particular time server may be affected. In the case of a bank, some transactions can go to the database with the wrong timestamp. |
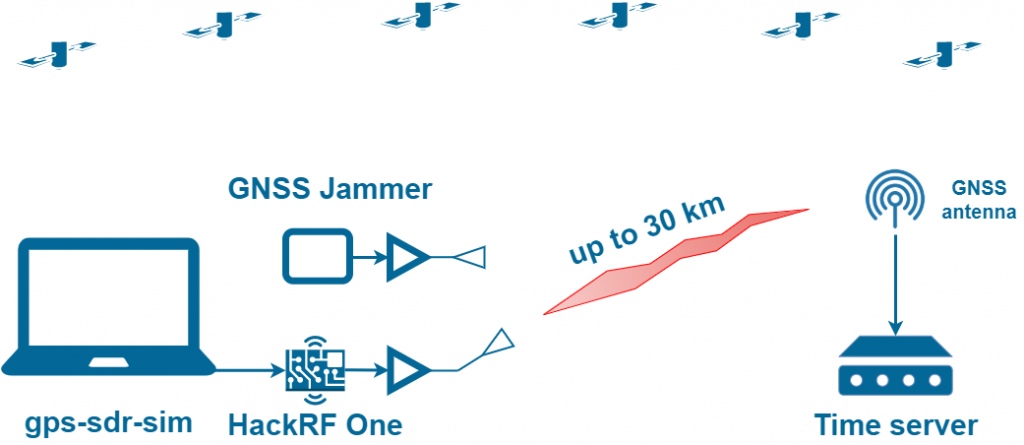
GNSS Spoofing with HackRF One, Jammer, and RF Amplifier
What is needed to extend the range of the attack?
Just a 10 Watts RF amplifier on AliExpress and a directional antenna:

| Attack cost |
1470 USD total. |
| Attack time | same as in the first case |
| Time server behavior | same as in the first case |
| Attack distance | 30 km if you install the spoofer on the roof of a building 40 meters high.
Just imagine that a fifteen hundred dollars set-up can spoof everything in a major city! Many will argue that such a powerful signal will immediately be tracked by the agencies responsible for monitoring the radio spectrum. But this is not precisely true because high power is needed only during the first seconds, which would force GNSS receivers to lose track of the original signals and go into search mode. Then, the power of the spoofer can be made negligible. And source localization will not be such an easy task anymore. And how quickly will the radio frequency agencies respond to this threat? In an hour, two hours, half a day? Imagine the scale of the financial loss to the entire economy of the region. |
| Protection | System-level protection will not help because all time servers in the synchronization system may be affected.
Without specialized anti-spoofing systems, there is nothing you can do. |
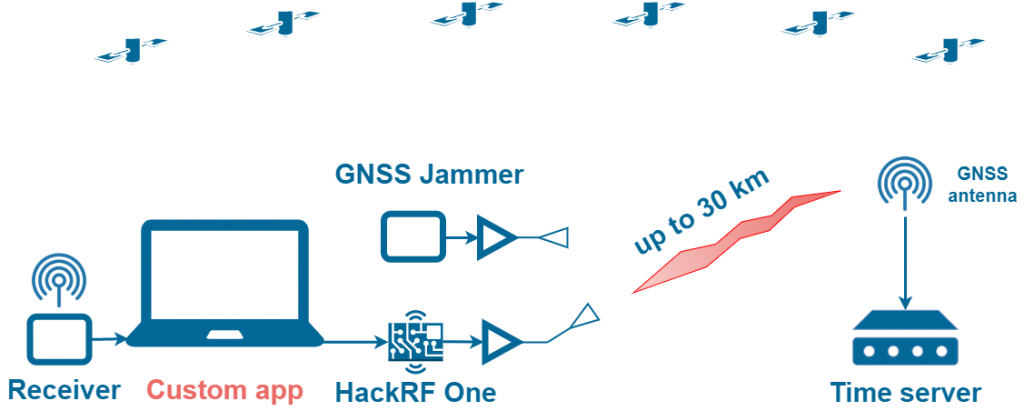
GNSS Spoofing with Synchronization. Deliberate Coherent Attack
The scenarios above correspond to non-coherent attacks. In the first phase of the attack, the GNSS receiver loses track of real satellites and switches to fake ones after a while. Such attacks are characterized by sharp jumps in power, PPS phase, and coordinates, and they can be relatively easily detected. But what happens if we synchronize with the real signals. And in the first phase of the attack, we will generate a signal that perfectly matches the real one in time, coordinates, pseudorange, Doppler, data stream, and SNR.
There is no way to download software from GitHub for such an attack. You can either modify one of the GPS-SDR-SIM forks yourself or buy commercially available solutions.
| Attack cost | 1470 USD in case you modify the source code of GPS-SDR-SIM yourself
50k USD for commercially available solutions |
| Attack time | Instantly |
| Time server behavior | A receiver instantly switches to the fake signal! The time server does not issue any errors or warnings and does not go into holdover mode.
After a successful takeover of the receiver, a smooth and controlled shift of time and/or coordinates is possible. Watch this video to see how the receiver responds to coherent attacks: https://youtu.be/Ws76xfJc1Pg. |
| Attack distance | Limited by the radio horizon only |
| Protection | Let’s think about what the purpose of such an attack could be.
By the way, an ideal case of synchronous attack can be executed using a GNSS repeater. If your time server antenna happens to be hit by a GNSS repeater signal from the nearest store, you will constantly have a slight time shift. There is only one method of protecting the time server from such an attack. This is a combination of spoofing detection systems with spatial signal analysis (antenna array) + alternative source of PNT. |
In this article, we are not trying to advertise our solution by finding the disadvantages of the listed anti-spoofing methods. Our extensive experience in real spoofing environments shows that these simple, elementary methods do not work.
Contact us and learn how to defend against all types of spoofing attacks.