GPS/GNSS spoofing is a well-known vulnerability of satellite navigation systems. However, this type of infringement has increased quite recently. For the most part, it was due to the substantial cost reduction of the equipment to generate counterfeit satellite signals with no engineering skills. Therefore, the likelihood of a deliberate or unintended breach on essential GNSS-dependent infrastructure has amplified in the last few years.
GPSPATRON is devised to protect the time synchronization system of critical infrastructure; we must guarantee the system’s operability.
Since no typical scenarios or methods for verifying such systems exist, the main goal for the GPSPATRON team was to develop the process of validating spoofing detection algorithms.
To become an expert in the detection of GPS spoofing, you must be an authority in spoofing attacks.
At the launch of the project, we understood that we needed to develop a GPS spoofer for inventing various attack scenarios, allowing us to study the impact of spoofing on time servers and then to build and test our detection algorithms.
With the help of a spoofer, we conducted hundreds of experiments and developed dozens of attack scenarios:
- asynchronous attack with an up-to-date or incorrect timestamp, and high or low power
- synchronous attack with simulated satellite’s clock drift and incorrect ephemeris
- synchronous attack with smooth phase offset
- attacks with/without authentic signals jamming
- multipath simulation to degrade the accuracy of determining the time
We analyzed the impact of spoofing on time servers of all leading manufacturers.
Experiments
We provide clients a GNSS spoofing testing service. Experiment objectives:
- assessment of customer’s GPS time servers vulnerability to spoofing
- infrastructure impact assessment
- demonstration of GP-Probe and GP-Cloud spoofing detection
These experiments demonstrate the functionality of our solution and the effectiveness of spoofing detection algorithms.
Validation in Moscow
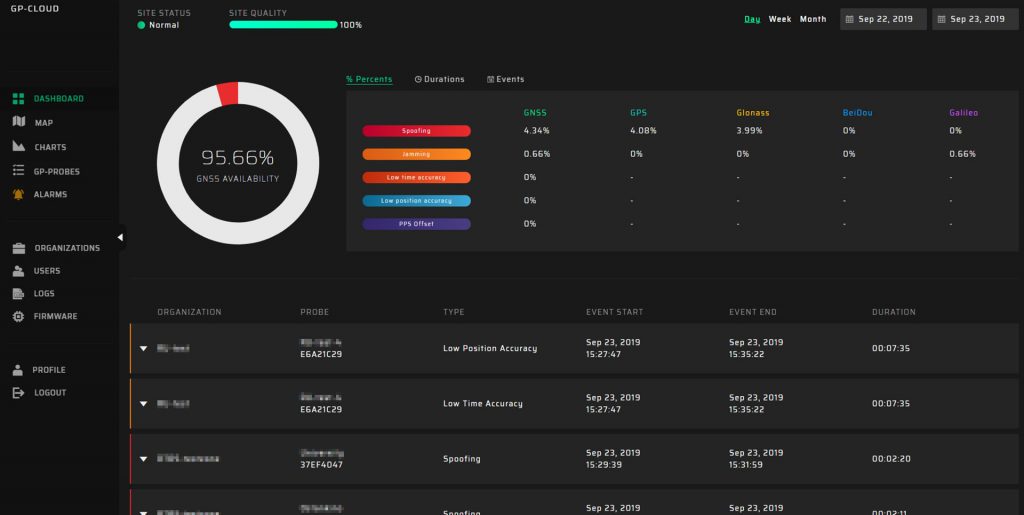
The largest number of GNSS spoofing events occur in the Russian Federation (Moscow, St. Petersburg, and the coastal regions of the Black Sea). Since October 2019, we have deployed pilot zones for field-testing of the system with a dozen installed GP-Probes. The GP-Probes are connected to time servers and measure the PPS signal phase shift. The algorithm validation criterion is the absence of PPS signal shifts under the GNSS spoofing attack. If there is a phase shift on the PPS without spoofing detection, then our algorithms do not work properly.
Pilot zones have been operating for several months. Every day we identify multitudes of spoofing attacks. All spoofing incidents were distinguished and time servers were protected against spoofing.
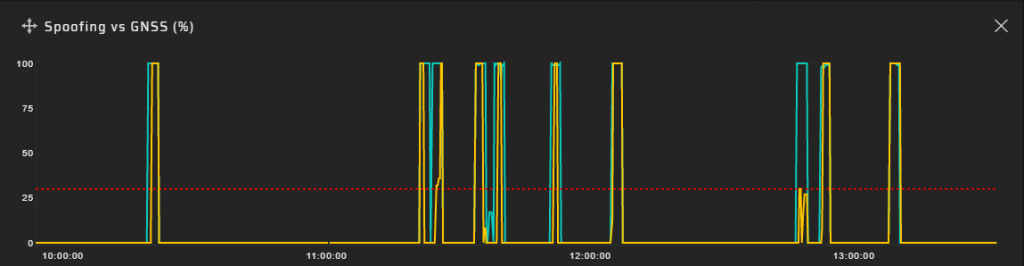
Another validation method is to check the synchronization of spoofing detection by various probes with antennas installed in different conditions: with “poor” or “good” visibility of the sky, at diverse heights, at assorted distances from the proposed spoofer location.
It is necessary not only to detect spoofing but also to evaluate the response speed. Our research showed that in some scenarios of an asynchronous attack, the time server accepted the bogus satellite signals and shifted PPS in 15 seconds after the assault started. In GPSPATRON all data is processed on the server side, and the result is transmitted to the GP-Probe. Therefore, it is imperative to ensure the real-time operation and detection delays.
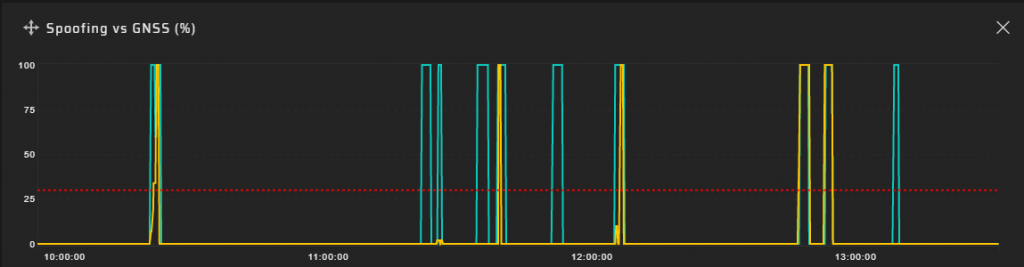
Spoofing charts for spaced probes installed in different conditions:
The last graph demonstrates the spoofing probabilities for the GP-Probe installed on the windowsill of an office building with poor visibility of the sky, but a good fake signal attenuation due to high buildings.
Note that the system shows not power, but the likelihood of spoofing. It is challenging to analyze broadband signals with a power lower than the power of background noise.
Our team constantly develops new methods of spoofing detection and novel attack scenarios, modifies algorithms, and surveys “real” spoofing in the Russian Federation.
Our goal is to become the authorities in GNSS spoofing and develop the best protection system.