Since mobile navigation systems are used by millions of consumers around the world, it is important to recognize their flaws. Even though GPS spoofing is a well-known threat, a lack of comprehensive knowledge exists on how GPS spoofing affects mobile GPS navigation systems used in civilian vehicles.Conducted by Kexiong (Curtis) Zeng, Shinan Liu, Yuanchao Shu, Dong Wang, Haoyu Li, Yanzhi Dou, Gang Wang, Yaling Yang (Virginia Tech; University of Electronic Science and Technology of China; Microsoft Research), in a study titled “All Your GPS Are Belong To Us: Towards Stealthy Manipulation of Road Navigation Systems” the researchers demonstrated how GPS spoofing attacks can manipulate road navigation system and devices.
Existing research demonstrates that even though it is undemanding to perform simple attacks by randomly setting user locations, such invasions are easily detectable since they may refute actual physical conditions. The main goal of the enquiry was to explore the possibility of a stealthy manipulation spoofing attack on GPS navigation systems by triggering fake turn-by-turn navigation of the corresponding systems and guiding the casualties to erroneous destinations without being detected.
The primary objective was to somewhat shift the GPS location so the fake navigation route would match the form of the genuine roads and initiate tangibly probable instructions. To do so, the following steps were taken:
- Measurements: Implementation of a GPS spoofer for performing empirical measurements and getting data on attackers’ practical constraints and capacities;
- Stealthy Attack Algorithms: Designing the attacking algorithms and evaluating them based on the empirical taxi driving traces. Extensive evaluations were performed using a trace-driven simulation from the traces of 600 taxies in Manhattan and Boston;
- Real World Driving Test: System implementation and its validation by means of real-life driving tests;
- User Study: Conduction of “deceptive” consumer studies to examine the feasibility of the attack with other users (non-authors) in the loop for gaining data on key factors that ensure their success.
Measurements: Researchers established that attackers can build a portable spoofer for a relatively low cost (about $223), which would be capable of penetrating the body of a car for taking control over its GPS navigation system with little effort. The measurements demonstrate that the effective spoofing range is 40–50 meters and the target device can consistently lock onto the false signals without losing connections. Attackers can perform the assault in two ways, by placing the spoofer inside or under the target vehicle and control the spoofer remotely or tailgate the target car to perform the spoofing attack.
Stealthy Attacking Algorithm: The attacking algorithm was designed in such a way that it crafted the GPS inputs to the target device and triggered the navigation instruction that would display routes on the map consistently with the physical road network. In reality, the victim who followed the instruction was led to the incorrect road (or an improper destination). The researchers evaluated algorithms using trace-driving simulations (600 taxi trips in total) from Manhattan and Boston. On average, the algorithm identified 1547 potential assailing routes for each target trip for the attackers to choose from. As a result, the algorithm turned out to be capable of crafting special routes that could contain inaccurate destinations or roads for 99.8% of the trips. Moreover, the algorithm also can enable attackers to pre-define a particular target finishing point where they want to lead the victim.
Real-world Driving Test: The empirical part of the research included the practical implementation of the algorithm and testing it by attacking the researchers’ vehicle in a real-life driving test. The results confirmed the possibility of the attack to trigger the target navigation instructions in real-time while the victim (the author) was moving (driving).
User Study: Researchers examined the attack feasibility with users (non-authors) in the loop. To avoid intruding actual cars, the researchers performed a deceptive experiment using a driving simulator. The simulator was customized to load a high-resolution 3D street map of real cities. The user study was conducted in the United States and China with consistent results. The consequences of the attack were highly effective, establishing that 38 out of 40 participants (95%) followed the navigation to the erroneous destinations.
Portable GPS Spoofer
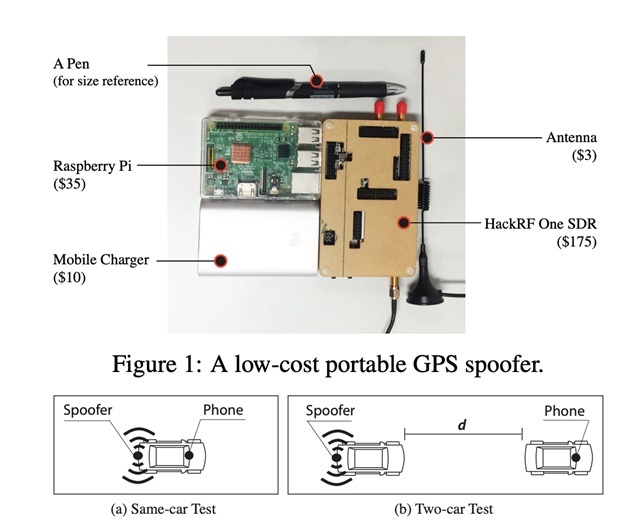
A portable GPS spoofer was implemented to accomplish the controlled experiments: As demonstrated in Figure 1. The spoofer consisted of four main components: a HackRF One-based frontend, a Raspberry Pi, a portable power source and an antenna. The spoofer is compact, allowing it to be placed in a small box. HackRF One is a Software Defined Radio (SDR). It was connected to an antenna with a frequency range between 700 MHz to 2700 MHz that covers the civilian GPS band L1 (1575.42 MHz). A Raspberry Pi 3B (Quad Core 1.2GHz Broadcom BCM2837 64bit CPU, 1GB RAM) was used as a central server. GPS satellite signals were generated by an open-source software called Wireless Attack Launch Box (WALB) running on Raspberry Pi. By controlling the Raspberry Pi, the researchers could inject the real-time GPS location information manually or by using scripts. All components of the spoofer are easily accessible averaging the total cost of the spoofer to around 223 US Dollars ($175+$35+$10+$3).
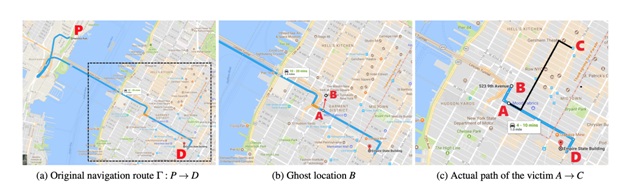
Figure 2 Demonstrates the example of a spoofing attack: “The victim’s original navigation route is P → D; At location A, the spoofer sets the GPS to a ghost location B that forces the navigation system to generate a new route B → D. Following the turn-by-turn navigation, the victim travels from A to C in the physical world”

User Reactions to GPS Spoofing Attacks
The attack conducted by the researchers demonstrates a success rate of 95%. Out of 40 people, only one participant from the US and one from China were able to recognize the attack. The remaining 38 participants finished the four rounds of driving tasks and followed the spoofed GPS navigation instructions, which resulted in reaching incorrect destinations. These outcomes lead to a conclusion that in real-life conditions, most drivers (users) would not notice they are being spoofed.
Conclusion
Researchers explored the feasibility of real-time stealthy GPS spoofing attacks that targeted mobile GPS road navigation systems. The probability rates of such intrusions were based on the data obtained from the real-life driving tests, taxi-trace evaluations, and human-in-the-loop user study results. Subsequently, researchers proved that GPS spoofing attacks on civilian vehicles with mobile road navigation systems have a 95% likelihood. Moreover, the corresponding spoofing attacks can be conducted using low-cost and easily accessible equipment as well as open source software.